- Research Article
- Open access
- Published:
Performance and Reliability of DSRC Vehicular Safety Communication: A Formal Analysis
EURASIP Journal on Wireless Communications and Networking volume 2009, Article number: 969164 (2009)
Abstract
IEEE- and ASTM-adopted dedicated short range communications (DSRC) standard toward 802.11p is a key enabling technology for the next generation of vehicular safety communication. Broadcasting of safety messages is one of the fundamental services in DSRC. There have been numerous publications addressing design and analysis of such broadcast ad hoc system based on the simulations. For the first time, an analytical model is proposed in this paper to evaluate performance and reliability of IEEE 802.11a-based vehicle-to-vehicle (V2V) safety-related broadcast services in DSRC system on highway. The proposed model takes two safety services with different priorities, nonsaturated message arrival, hidden terminal problem, fading transmission channel, transmission range, IEEE 802.11 backoff counter process, and highly mobile vehicles on highway into account. Based on the solutions to the proposed analytic model, closed-form expressions of channel throughput, transmission delay, and packet reception rates are derived. From the obtained numerical results under various offered traffic and network parameters, new insights and enhancement suggestions are given.
1. Introduction
Transportation safety is one of the most important intelligent transportation system (ITS) applications. Active safety applications, that use autonomous vehicle sensors such as radar, lidar, and camera are being developed and deployed in vehicles by automakers to address the vehicle accident problem. Communications systems are expected to play a pivotal role in the ITS safety applications. Message communication in the ITS is normally achieved by installing a radio transceiver in each vehicle allowing wireless communications. Vehicle-to-vehicle (V2V) communication is of critical importance to many ITS safety-related services. The DSRC standard with 75 MHz at 5.9 GHz band was projected and licensed to support low-latency wireless data communications among vehicles and from vehicles to roadside units in USA [1–3]. Essentially, the DSRC radio technology is IEEE 802.11a adjusted for low-overhead operations in the DSRC spectrum. It is being standardized as IEEE 802.11p [2–5].
Safety applications usually demand direct V2V ad hoc communication networks due to highly dynamic topology of the networks and the stringent delay requirements [6]. They will likely work in a broadcast fashion since safety information can be beneficial to all vehicles around a sender and safety message senders might not expect a response at the application level. For the purpose of high reliability and simple implementation, some direct (or single-hop) broadcast solutions to safety-related message transmission have been suggested and investigated. Xu et al. [7] propose several single-hop broadcast protocols to improve reception reliability and channel throughput. Torrent-Moreno et al. [8] propose a priority access scheme for IEEE 802.11-based vehicular ad hoc networks and show that the broadcast reception probability can become very low under saturation conditions. Jiang et al. [9] raise channel congestion control issues for vehicular safety communication, and introduce feedback information to enhance system performance and reliability. ElBatt et al. [10] discuss the suitability of DSRC periodic broadcast message for cooperative collision warning application. To date, all analyses and observations are mainly based on simulations [8, 11]. Although the connectivity of unicast wireless networks is studied theoretically [12], the factors that affect DSRC system performance and reliability such as IEEE 802.11 backoff counter process, hidden terminals, channel access priority, message generation interval, and high mobility on the road have not been theoretically addressed yet for the analysis of the DSRC safety broadcast communications. As a matter of fact, the exact analysis of such broadcast ad hoc networks with hidden terminal is still an open problem [13].
In this paper, we first introduce and justify an effective solution to the design of the control channel in DSRC with two levels of safety services covering most of the possible safety applications. Then, we construct an analytical model based on Markov chain method in [14] to evaluate performance and reliability indices such as channel throughput, transmission delay, and packet reception rates of a typical network solution for DSRC-based safety-related communication under highway wireless communication environment. We apply our proposed model to evaluate the impact of message arrival interval, channel access priority scheme, hidden terminal problem, fading transmission channel, and highly mobile vehicles on the performance and reliability. Based on the observations of numerical results under typical DSRC environment, some enhancement schemes are suggested or validated accordingly.
The remainder of this paper is organized as follows. Section 2 briefly reviews the DSRC communication system and environment, specifies requirements for the safety-related communication, and presents DSRC control channel design to cover most of the possible safety applications. Section 3 demonstrates an analytic model for broadcasting two levels of safety-related messages using the control channel in the highway scenario. Consequently, closed-form expressions of performance and reliability indices are derived. In Section 4, the proposed analytical model is validated by extensive simulations. In terms of the numerical results, some important observations and constructive enhancement suggestions are given. This paper is concluded in Section 5.
2. DSRC System Descriptions and Solution to Safety Message Broadcast
2.1. DSRC System for Safety Applications
The 5.9 GHz DSRC is a wireless interface expected to support high speed, short-range wireless interface between vehicles, and surface transportation infrastructure, as well as to enable the rapid communication of vehicle data and other content between on board equipment (OBE) and roadside equipment (RSE).
The DSRC spectrum consists of seven ten-megahertz channels that include one control channel and six service channels. Channel 178 is the control channel, which is generally restricted to safety communications only [2, 3]. The DSRC physical layer uses an orthogonal frequency division multiplex (OFDM) modulation scheme to multiplex data. The DSRC physical layer follows exactly the same frame structure, modulation scheme, and training sequences specified by IEEE 802.11a physical layer. However, DSRC applications require reliable communication between OBEs and from OBE to RSUs when vehicles are moving up to 120 miles/hour and having communication ranges up to 1000 meters. According to the updated version of the DSRC standard, the MAC layer of the DSRC adopts 802.11a layer specification with minor modifications. This is a random access scheme for all associated devices in a cluster based on carrier sense multiple access with collision avoidance (CSMA/CA). In the 802.11 MAC protocols, the fundamental mechanism for medium access is the distributed coordination function (DCF). DCF is meant to support an ad hoc network without the need of any infrastructure element such as an access point, but DCF is not able to provide predictable quality of service (QoS). The development of a robust and efficient MAC protocol will be central to the new generation DSRC devices.
Broadcast procedure of 802.11 MAC follows the basic medium access protocol of DCF except that no positive acknowledgement and retransmission exist. Broadcast of DSRC MAC occurs when a broadcast packet arrives at DSRC MAC layer from the upper layer and the MAC senses the channel status first and stores the status. Next, once an idle period equal to DIFS/EIFS is observed, MAC takes the next operation according to the stored channel status and the current value of its backoff time. If the current value of the backoff counter is not zero, MAC begins the backoff countdown process. If the current value of the backoff counter is zero and the status of the medium is busy, MAC generates random backoff time and begins the backoff countdown process. If the backoff counter counts down to zero, MAC begins data packet transmission immediately. During the backoff countdown process, carrier sense persists. If the medium becomes busy again, MAC goes back to the DIFS/EIFS observation process. During or after a broadcast transmission, MAC does not monitor the success or failure of the transmission. Once transmission completes, MAC simply releases the medium and competes for it when a new packet is ready to be sent.
There are two types of safety-related life messages that will likely be transmitted over the control channel [7, 15]: event-driven (or emergency) safety messages and periodic (or routine) safety messages. Event-driven messages will contain information about environment hazards. They will be transmitted when an emergency or a nonsafe situation is detected to make all the vehicles in the area aware or activates an actuator of an active safety system. Event-driven communications happen only occasionally, but must meet a requirement of fast and guaranteed delivery. Routine messages will contain state of vehicles (e.g., position, speed, and direction) and will be broadcasted by all vehicles at a frequency 10–20 times per second.
2.2. DSRC Environment
Under V2V communication environment, the vehicles are highly mobile and the network topology changes very frequently. These changes are due to the high relative speed of vehicles, even when they are moving in the same direction. Two vehicles can directly communicate only when they are within their radio range. For safety communication in DSRC, the high mobility of vehicles on the road may cause two adverse effects on performance of message sending and receiving. On one hand, during the transmission of safety-related message, some of the receivers may move out of the transmission range of the sender, resulting in failure of receiving the message. On the other hand, high mobility makes worse Doppler spread on OFDM, which leads to higher packet error rates and consequently lower channel capacity.
V2V communications present scenarios with unfavorable characteristics to deploy wireless communications, for example, multiple reflecting objects that are able to degrade the strength and quality of the received signal. While there are many factors that can affect the bit error rate (BER) on a multihop communication environment, mobility of nodes is one of the most important factors that can cause packet errors.
The problem of hidden terminals is a critical issue affecting the performance and the reliability of ad hoc networks. Hidden terminals are two terminals that although they are outside the interference range of one another, they share a set of terminals that are within the transmission range of both. Broadcast in IEEE 802.11 does not use virtual carrier sensing and thus only relies on physical carrier sensing to reduce collision [16]. In the case of broadcast communication, the potential hidden terminal area needs to include the receiving range of all the terminals within transmission range of the sender. Thus, the potential hidden terminal area in broadcast can be dramatically larger than that of unicast. In other words, the broadcast fashion of V2V safety communications makes them more sensitive to hidden terminal problems.
2.3. Requirements of Safety-Related Communication
It is possible to design safety systems based on a high speed wireless communication network to improve the safety on the road. For example, chain collisions can be potentially avoided or their severity lessened by reducing the delay between the time of an emergency event and the time at which the vehicles behind are informed about it [17]. A vehicle on a freeway could move at speed as fast as 120 miles per hour. Once an emergency situation occurs, it is critical to let the surrounding vehicles realize the situation as soon as possible. Because the driver reaction time (the duration between when an event is observed and when the driver actually applies the brake) to traffic warning signals can be in the order of 700 milliseconds or longer, the update interval of safety message should be less than 500 milliseconds (we refer to it as lifetime of safety message). Otherwise, the safety system is useless to help the driver deal with the emergency situations. Hence, It is required that the DSRC safety-related V2V communication must provide a service delivering messages within their lifetime with high reliability under high-speed vehicular environment. According to the requirements in [11], the probability of message delivery failure in a vehicular network should be less than 0.01. Table 1 summarizes typical parameters for road traffic scenarios associated with safety-related communication. As we see from Table 1, safety messages are usually very short. The message range is the maximum distance at which a message should be received.
2.4. Solutions to Broadcasting of Safety Message
To support safety applications in the DSRC system with high reliability and low delay, the basic link-layer behavior and the environment of safety communications in the control channel can be defined as follows [8, 9, 15].
-
(1)
Vehicle safety communication networks are entirely distributed ad hoc wireless networks.
-
(2)
Two types of the safety messages are broadcasted in the control channel; event-driven safety messages consist of all real-time safety critical information, while routine safety messages consist of the state of vehicles, and some safety-related information with loose delay requirement.
-
(3)
Most of the identified safety applications are based on direct or single-hop broadcast communication among vehicles within the range of one another.
-
(4)
Transmission power of each vehicle for safety-related communication should be strong enough to reach all potentially affected vehicles that need to take actions immediately.
-
(5)
Each safety message is usually very short (100~300 bytes), and thus usually mapped to a single frame.
-
(6)
A real-time priority scheme similar to IEEE 802.11e is adopted to differentiate two safety services by using different distributed coordination function (DCF) backoff window sizes: the higher priority class uses the window
 and the lower priority class uses the window
and the lower priority class uses the window 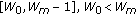 .
.
The above framework of direct (or single-hop) safety message broadcast is justified as follows. (1) As an emergency situation takes place, the potentially affected vehicles that need to be alerted immediately must be very close to where the safety message is sent out. So direct message broadcasting would be enough to reach all such vehicles. (2) Some safety-related services that desire multihops of message forwarding (e.g., road caution hazard notification, and post crash notification) can be transmitted as routine safety message because delay requirement for the services is relatively longer (0.5–2 seconds). (3) Compared with multihop broadcast, single-hop broadcasting communication has the characteristics of lower delay, higher reliability, and being easier to implement and analyze.
Considering that reliability of safety message transmission is the most critical among other performance indices, we introduce or suggest several potential mechanisms to enhance the packet reception rates. (1) Increase backoff window sizes to reduce chances of packet collisions; (2) increase carrier sensing range to withstand the effect of hidden terminal; (3) design proper repetitions of the emergency packet within the packet lifetime; (4) give the event-driven safety service preemptive priority over the routine safety service so that possible collisions between two types of service will be reduced. Normally, routine safety message transmissions dominate the channel. Once an emergency messaging takes place, routine services stop and emergent message delivery will occupy the channel. In this paper, an enhancement scheme that combines step (3) with (4) is modeled and analyzed and all repetitions are separated by SIFS. The reason is that SIFS is long enough for all receivers to be able to identify individual packet, but is not too long to be mistaken by other vehicles as the end of a transmission.
3. System Model and Performance Analysis
3.1. Assumptions for IEEE 802.11 Broadcast in DSRC
In this paper, we focus on reliability and performance analysis of the DSRC control channel with two levels of safety services. Real world radio networks are influenced by many factors. In our model, we assume that IEEE 802.11 broadcast DCF works under the following scenarios.
-
(1)
We consider a highway environment where vehicles are exponentially distributed and they travel in free-flow conditions. As seen in Figure 1, the vehicular V2V network built along a highway is simplified as a one-dimensional (1D) mobile ad hoc networks which consist of a collection of statistically identical mobile stations randomly located on a line.
-
(2)
Vehicles are placed on the line according to a Poisson point process with network density β (in vehicles per meter); for example, the probability
 of finding i vehicles in length of l is given by
of finding i vehicles in length of l is given by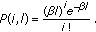 (1)
(1) -
(3)
All vehicles have the same transmission and receiving range, which is denoted by R. The average number of vehicles in transmission range of a vehicle on the road is
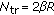 .
. -
(4)
Given the tagged vehicle (the vehicle sending message) placed in origin, all vehicles have the same carrier sensing range
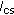 which is assumed to vary between the range
which is assumed to vary between the range  . The average number of vehicles in carrier sensing range of the tagged vehicle on the road is
. The average number of vehicles in carrier sensing range of the tagged vehicle on the road is 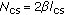 .
. -
(5)
As shown in Figure 1, when the vehicular V2V network considered is simplified as a one-dimensional network, the potential hidden terminal area of the tagged vehicle in broadcast communication drops in the range of
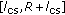 and
and 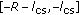 assuming that the carrier sensing range equals the range within which one node interferers with other node. The average number of the potential hidden vehicles of the tagged vehicle on the road is
assuming that the carrier sensing range equals the range within which one node interferers with other node. The average number of the potential hidden vehicles of the tagged vehicle on the road is 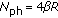 .
. -
(6)
At each vehicle, routine packets and emergency packets have the same average length
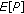 ; both arrivals are Poisson processes with rates
; both arrivals are Poisson processes with rates  and
and 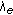 (in packets per second), respectively.
(in packets per second), respectively. -
(7)
There are two queues in each vehicle. One is for routine messages and the other is for emergency messages. They sense and access the channel independently. If two services conflict with each other in a vehicle, the emergency packet will be served first. The queue length of packets each vehicle can store at the MAC layer is unlimited. So each vehicle can be modeled as two independent discrete time M/G/1 queues [18]. Two broadcast services share the common control channel.
-
(8)
The relative velocity of vehicles in the network is assumed to be uniformly distributed in the interval
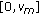 , where
, where  is the maximum relative speed. The average relative velocity of two vehicles in the network is assumed to be a constant value
is the maximum relative speed. The average relative velocity of two vehicles in the network is assumed to be a constant value  .
. -
(9)
V2V communications present scenarios with unfavorable characteristics of channel fading in DSRC. The channel fading is reflected by simply introducing packet error probability
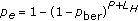 , where P is the length of the packet,
, where P is the length of the packet,  is the length of packet header, and
is the length of packet header, and 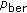 is the fixed bit error rate (BER) probability.
is the fixed bit error rate (BER) probability. 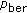 can be numerically evaluated for a Rician fading channel [19]. When data bits are transmitted over Nakagami-m fading links,
can be numerically evaluated for a Rician fading channel [19]. When data bits are transmitted over Nakagami-m fading links,  can be easily obtained using the closed form expressions given in [20]. Capture effect is not considered in this paper.
can be easily obtained using the closed form expressions given in [20]. Capture effect is not considered in this paper. -
(10)
With high channel data rates and relatively big backoff window size W 0 , the consecutive freeze effect [21] in IEEE 802.11 DCF on the broadcast performance is neglected.
-
(11)
All nodes within one-hop range of the transmitted node are assumed to have synchronized time scale. It has been proven that by extensive simulations, the impact of the asynchronous time scale on the performance is negligible; if the transmitted packet is short, the backoff window size is big enough, and the channel data rate is high [22].
3.2. Backoff Process in IEEE 802.11 Broadcast
Now, we construct a model to characterize backoff counter process of each vehicle in IEEE 802.11 broadcast network. We know that the stochastic process indexed by backoff counter values of a broadcast vehicle is a one-dimensional discrete-time Markov chain [21]. Figure 2 shows the Markov chains for two safety services, respectively. Let  and
and  be the probability that a vehicle transmits emergent packet and routine packet, respectively. Here, we derive the unsaturated transmission probabilities through a Markov model for the saturated backoff process. Based on our solutions to the one-dimensional Markov chain [10, 21], we have
be the probability that a vehicle transmits emergent packet and routine packet, respectively. Here, we derive the unsaturated transmission probabilities through a Markov model for the saturated backoff process. Based on our solutions to the one-dimensional Markov chain [10, 21], we have

where  is the probability that there are no emergent (routine) packets ready to be transmitted at the MAC layer in each vehicle, which will be derived later in Section 3.4. In the backoff process, if the medium is sensed idle, the backoff timer will decrease by one for every idle slot detected. When detecting an ongoing transmission, the backoff timer will be suspended and deferred a time period of
is the probability that there are no emergent (routine) packets ready to be transmitted at the MAC layer in each vehicle, which will be derived later in Section 3.4. In the backoff process, if the medium is sensed idle, the backoff timer will decrease by one for every idle slot detected. When detecting an ongoing transmission, the backoff timer will be suspended and deferred a time period of  ,
,

where σ is the slot time duration; δ is the propagation delay, and DIFS is the time period for a distributed interframe space. T b is the average time the channel sensed busy by each node in the network

where R
d
is system transmission data rate. It is assumed that a packet holds size P with average packet length  , and packet header includes physical layer header plus MAC layer header
, and packet header includes physical layer header plus MAC layer header  . When the enhancement (packet repetition with preemptive priority for event-driven safety message) is applied, the transmission time period is modified as
. When the enhancement (packet repetition with preemptive priority for event-driven safety message) is applied, the transmission time period is modified as

where  is the number of packet repetitions, and SIFS is the time duration of short interframe space.
is the number of packet repetitions, and SIFS is the time duration of short interframe space.
3.3. Performance of Channel for Tagged Vehicle
We consider a vehicular wireless ad hoc broadcast network with dynamic topology where each vehicle can send out a packet if there is no transmission sensed within the carrier sensing range of the vehicle. So here a channel is defined with respect to any vehicle sending out packet (referred to as the tagged vehicle).
Now, we calculate channel performance from the tagged vehicle's point of view. Define p b as the probability that the channel is sensed busy by the tagged vehicle. Knowing that the channel is busy if there is at least one vehicle transmitting any type of services in the transmission range of the tagged vehicle, we have

where  . Define p
s
as the probability that the transmission from the tagged node is successful. Taking hidden terminal into consideration, we obtain
. Define p
s
as the probability that the transmission from the tagged node is successful. Taking hidden terminal into consideration, we obtain

where  may be either
may be either  for emergent transmission or
for emergent transmission or  for routine transmission;
for routine transmission;  is the hidden vulnerable period, p
e
is packet error probability defined in Section 3.1, and
is the hidden vulnerable period, p
e
is packet error probability defined in Section 3.1, and  is link breaking probability for a communication pair, which will be defined and evaluated later in Section 3.5. Note that here "successful" means all nodes within transmission range of the tagged vehicle have received broadcast information from the tagged vehicle. From (7), we can see that the successful transmission takes place under the following conditions: (1) no nodes within transmission range of the tagged vehicle transmit at the time instant when the tagged vehicle starts to transmit; (2) no nodes in the two potential hidden terminal areas (see Figure 1) transmit during a vulnerable period
is link breaking probability for a communication pair, which will be defined and evaluated later in Section 3.5. Note that here "successful" means all nodes within transmission range of the tagged vehicle have received broadcast information from the tagged vehicle. From (7), we can see that the successful transmission takes place under the following conditions: (1) no nodes within transmission range of the tagged vehicle transmit at the time instant when the tagged vehicle starts to transmit; (2) no nodes in the two potential hidden terminal areas (see Figure 1) transmit during a vulnerable period  (normalized to the number of time slots through dividing by length of a virtual slot); (3) no transmission errors occur during the packet transmission; (4) no vehicles receiving the packet move out of the transmission range of the tagged vehicle throughout the packet transmission. The reason for the vulnerable period calculation is that the collision caused by nodes in potential hidden area could happen during the period that begins a transmission period before the tagged node starts its transmission and ends after the tagged node completes its transmission. In the one-dimensional mobility model as shown in Figure 1, there are two potential hidden terminal areas with respect to the tagged node. In each potential hidden terminal area, a transmission from a hidden node will be sensed by other hidden nodes in the same area, which may cause silence of the other nodes. Since two potential hidden terminal areas in Figure 1 are
(normalized to the number of time slots through dividing by length of a virtual slot); (3) no transmission errors occur during the packet transmission; (4) no vehicles receiving the packet move out of the transmission range of the tagged vehicle throughout the packet transmission. The reason for the vulnerable period calculation is that the collision caused by nodes in potential hidden area could happen during the period that begins a transmission period before the tagged node starts its transmission and ends after the tagged node completes its transmission. In the one-dimensional mobility model as shown in Figure 1, there are two potential hidden terminal areas with respect to the tagged node. In each potential hidden terminal area, a transmission from a hidden node will be sensed by other hidden nodes in the same area, which may cause silence of the other nodes. Since two potential hidden terminal areas in Figure 1 are  away from each other, vehicles in one area cannot hear the transmission status of vehicles in the other area. Transmissions in two areas are mutually independent. Each hidden terminal has chances to fail the target vehicle transmission: either by the tagged vehicle starts sending while a hidden terminal is transmitting or by that one hidden terminal starts transmitting while the tagged vehicle is transmitting.
away from each other, vehicles in one area cannot hear the transmission status of vehicles in the other area. Transmissions in two areas are mutually independent. Each hidden terminal has chances to fail the target vehicle transmission: either by the tagged vehicle starts sending while a hidden terminal is transmitting or by that one hidden terminal starts transmitting while the tagged vehicle is transmitting.
Define p c to be the probability of a collision seen by a packet being transmitted in the medium. It is also the probability that at least one collision takes place in the medium among other vehicles in the interference range of the tagged vehicle under consideration. This yields

3.4. Service Time
The MAC layer service time is the time interval from the time instant when a packet becomes the head of the queue and starts to contend for transmission to the time instant when the packet transmission is over. This time is important when we examine the performance of higher protocol layers. Apparently, the distribution of the MAC layer service time is a discrete probability distribution when the smallest time unit of the backoff timer is a time slot σ. Here, we model the characteristics of each vehicle in the network as two M/G/1 queues and approach service time distributions through probability generating function (PGF).
We understand that the backoff counter in each vehicle will be decremented by a slot once an idle channel is sensed and will wait for a transmission time once a busy channel is sensed. For a tagged vehicle in broadcast communication, the transition for backoff counter decremented by one can be expressed by the following PGF:

where  is a function to round floating point numbers to integers. Denote q
i
as the steady state probability that the packet service time is
is a function to round floating point numbers to integers. Denote q
i
as the steady state probability that the packet service time is  . Let
. Let  be the PGF of q
i
, which is
be the PGF of q
i
, which is

Now, it is possible to draw the generalized state transition diagram for both the emergent packet broadcast transmission and routine packet broadcast transmission, as shown in Figure 3. Knowing that successful transmission and transmission with collision take same amount of time in broadcast, we have  . From Figure 3, we can derive the transfer functions of the linear systems or distributions of the emergent service time and routine service time, respectively,
. From Figure 3, we can derive the transfer functions of the linear systems or distributions of the emergent service time and routine service time, respectively,


Based on (12) and (13), we can obtain the arbitrary n th moment of service time by differentiation. Therefore, the average service times or service rates can be obtained by


In order to derive the average service time distributions, the probability  must be determined, while
must be determined, while  calculation depends on the duration of service time. In this paper, we apply an iterative algorithm to calculate
calculation depends on the duration of service time. In this paper, we apply an iterative algorithm to calculate  .
.
The iterative steps are outlined as follows.
Step 1.
Initialize  , which is the saturated condition.
, which is the saturated condition.
Step 2.
With  , calculate
, calculate  and p
b
according to (3), (4), (5), and (6).
and p
b
according to (3), (4), (5), and (6).
Step 3.
Calculate service time distributions through PGF.
Step 4.
Calculate service rates 
Step 5.
if  otherwise,
otherwise,  .
.
Step 6.
If both  and
and  converge with the previous values, then stop the algorithm; otherwise, go to Step 2 with the updated
converge with the previous values, then stop the algorithm; otherwise, go to Step 2 with the updated  .
.
3.5. Delay
Packet transmission delay  is the average delay a packet experiences between the time at which the packet is generated and the time at which the packet is successfully received. It includes the medium service time (due to backoff, busy channel waiting, interframe spaces, transmission delay, and propagation delay, etc.), and queuing delay.
is the average delay a packet experiences between the time at which the packet is generated and the time at which the packet is successfully received. It includes the medium service time (due to backoff, busy channel waiting, interframe spaces, transmission delay, and propagation delay, etc.), and queuing delay.
For the case of unsaturated condition  , the expected virtual queuing delay can be obtained by the Pollaczek-Khintchine mean value formula [23] for M/G/1 queues
, the expected virtual queuing delay can be obtained by the Pollaczek-Khintchine mean value formula [23] for M/G/1 queues

The average packet transmission delays for two services can be calculated as

3.6. Link Breaking Probability
Define X to be the distance from the position of any vehicle at instant when the tagged vehicle is requesting channel for packet transmission to the boundary of the tagged vehicle transmission range.
From the assumption that all vehicles in the network are one-dimensional Poisson distributed with density β, the PDF of X of a vehicle is

The time period which a mobile vehicle spends within radio transmission range of the tagged vehicle is defined as the radio dwell time  , which follows
, which follows

where V is speed of a vehicle relative to the tagged vehicle, and X and V are assumed to be independent. Consequently, given that the relative velocity of vehicles in the network is uniformly distributed in the interval  , the PDF of the dwell time can be obtained by
, the PDF of the dwell time can be obtained by

Specifically, if the relative velocity is a constant  , we have
, we have

Furthermore, we define the link holding time  as the time period during which a vehicle in the network keeps connected with the tagged vehicle. It is equal to the smaller one between the radio range dwell time
as the time period during which a vehicle in the network keeps connected with the tagged vehicle. It is equal to the smaller one between the radio range dwell time  and the packet transmission time T. That is
and the packet transmission time T. That is

Since the radio range dwell time and the virtual packet transmission time T are independent, we can get the PDF of the link holding time by

where  is the cumulative distribution function (CDF) of the packet transmission time T, and
is the cumulative distribution function (CDF) of the packet transmission time T, and  is the CDF of the radio range dwell time
is the CDF of the radio range dwell time  .
.
When the tagged vehicle is transmitting, the fact that some of receivers are moving out the tagged vehicle's transmission range makes the link break. The link breaking probability  of a communication pair is the probability that the packet transmission time exceeds the radio range dwell time. Thus, we have
of a communication pair is the probability that the packet transmission time exceeds the radio range dwell time. Thus, we have

Knowing that T is a constant, we have

3.7. Normalized Channel Throughput
Define S as the normalized throughput, defined as the fraction of time the channel is used to successfully transmit payload bits. For DSRC V2V network, we analyze the throughput based on a single vehicle's standpoint, and then derived to the total network throughput by summing up individual vehicle's throughput. Also, the computation of nonsaturated throughput and the computation of saturated throughput are carried out separately. Besides, accounting for mobility of vehicles, the throughput decreases since mobile receivers cross the tagged vehicle's transmission range more often causing the network transmission failure. Thus, we have

In (25),  is replaced by
is replaced by  , as the suggested enhancement is applied.
, as the suggested enhancement is applied.
3.8. Packet Reception Rate
Packet reception rate (PRR) is defined as the ratio of the number of packets successfully received to the number of packets transmitted. So PRR can be interpreted as the probability that all vehicles within transmission range of the tagged vehicle receive the broadcast message successfully in a virtual slot.
Impact of Hidden Terminal. We observe that the ratio of receivers affected by the hidden terminals only depends on the position of the hidden node (referred to as hidden crucial node) that has the closest distance to the boundary of the transmitter's sensing range among all transmitting nodes in the potential hidden terminal area. Denote X as a random variable that represents the distance from the hidden crucial node (see A in Figure 1) to the outer boundary of  . Let R
s
be the range in the potential hidden terminal area where no node transmits, such that
. Let R
s
be the range in the potential hidden terminal area where no node transmits, such that

Then the cumulative distribution function (CDF) for X is [13]

where  is the vulnerable period (normalized to the time slot) during which the tagged node's transmission is vulnerable to hidden terminal problem.
is the vulnerable period (normalized to the time slot) during which the tagged node's transmission is vulnerable to hidden terminal problem.
Equation (27) gives the probability that the closest interfering node (or hidden crucial node) in the potential hidden terminal area is at least  away from the transmitter, that is, the probability that no nodes within R
s
transmit during the transmission from the tagged node. Since all nodes are exponentially distributed on a line, we have
away from the transmitter, that is, the probability that no nodes within R
s
transmit during the transmission from the tagged node. Since all nodes are exponentially distributed on a line, we have

where  , and
, and  is the length of a virtual slot [21]. It is easy to prove that x is equal to the range where nodes in
is the length of a virtual slot [21]. It is easy to prove that x is equal to the range where nodes in  are affected by the hidden nodes in
are affected by the hidden nodes in  . Thus, the expected number of failed nodes in
. Thus, the expected number of failed nodes in  due to transmissions of the hidden nodes can be expressed as
due to transmissions of the hidden nodes can be expressed as

Therefore, the percentage of receivers that are free from collisions caused by hidden nodes is evaluated as

Impact of Possible Concurrent Collisions. In addition to collisions caused by the hidden nodes, transmissions from nodes which are  away from the tagged node in the mean time when the tagged node transmits may also cause collisions. When the tagged node transmits in a slot time, collisions will take place if any node in the transmission range of the tagged node (i.e., node in
away from the tagged node in the mean time when the tagged node transmits may also cause collisions. When the tagged node transmits in a slot time, collisions will take place if any node in the transmission range of the tagged node (i.e., node in  ) transmits in the slot. As shown in Figure 1, any node transmitting in the right-hand side of the tagged node (i.e., node in
) transmits in the slot. As shown in Figure 1, any node transmitting in the right-hand side of the tagged node (i.e., node in  ) will result in the failure of all nodes in
) will result in the failure of all nodes in  receiving the broadcast packet. So the ratio of successful receiving nodes in the range
receiving the broadcast packet. So the ratio of successful receiving nodes in the range  can be expressed as
can be expressed as

On the other hand, transmissions of any node in the left-hand side of the tagged node (i.e., node in  ) will only result in the failure of partial nodes receiving the broadcast packet in
) will only result in the failure of partial nodes receiving the broadcast packet in  . Similar to the analysis of the hidden terminal impact, the ratio of successful receiving nodes due to any transmission in
. Similar to the analysis of the hidden terminal impact, the ratio of successful receiving nodes due to any transmission in  depends on the position of the closest node transmitting in
depends on the position of the closest node transmitting in  to the tagged node. Denote Y as a random variable that represents the distance from the closest node transmitting in
to the tagged node. Denote Y as a random variable that represents the distance from the closest node transmitting in  (see B in Figure 1) to the outer boundary of range
(see B in Figure 1) to the outer boundary of range  . Let R
t
be the range in the left-hand side area where no station transmits such that
. Let R
t
be the range in the left-hand side area where no station transmits such that

Then the CDF for Y is

It gives the probability that the closest interfering node in  is at least (
is at least ( ) away from the transmitter, that is, the probability that no nodes within R
t
transmit in the mean time the tagged node starts to transmit. So we have
) away from the transmitter, that is, the probability that no nodes within R
t
transmit in the mean time the tagged node starts to transmit. So we have

Thus, the expected number of failed nodes in  due to concurrent transmission of nodes in
due to concurrent transmission of nodes in  can be expressed as
can be expressed as

Therefore, the percentage of receivers in  that are free from collisions caused by concurrent transmissions of nodes in the range
that are free from collisions caused by concurrent transmissions of nodes in the range  can be evaluated
can be evaluated

Packet Reception Rate (PRR). PRR is defined as a percentage of nodes that successfully receives a packet from the tagged node given that all receivers are within transmission the range of the sender at the moment when the packet is sent out [8]. From the above definition, PRR can be interpreted as the percentage of the mobile nodes in the tagged node's transmission range that receives the broadcasted message successfully in a virtual slot. Taking hidden terminal and possible packet collisions into account, we derive PRR for a single packet transmission or first packet in multiple packet transmissions as

PRR expression (37) is divided into five parts (1) all nodes will receive the transmitting packet from the tagged node if no nodes within the transmission range of the tagged node transmit at the time instant when the tagged node starts to transmit; (2) only part of nodes will receive the transmitting packet as there is at least one node in the transmission range of the tagged node transmitting in a virtual slot; (3) some nodes in  may fail to receive the broadcast packet if any nodes in the two potential hidden terminal areas (see Figure 1) transmit during the vulnerable period
may fail to receive the broadcast packet if any nodes in the two potential hidden terminal areas (see Figure 1) transmit during the vulnerable period  ; (4) some nodes in
; (4) some nodes in  may fail to receive the broadcast packet if any transmission error occurs during the packet transmission; (5) some nodes in
may fail to receive the broadcast packet if any transmission error occurs during the packet transmission; (5) some nodes in  may fail to receive the broadcast packet if the nodes move out of the transmission range during the transmission period.
may fail to receive the broadcast packet if the nodes move out of the transmission range during the transmission period.
Notice that PRR is a very important reliability measure, which evaluates how all vehicles within the transmission range of the tagged transmitting vehicle receive the broadcast safety-related message. Since two levels of safety services share a common control channel, their one-hop theoretical PRRs should be identical.
PRR e for the suggested repetition protocol is a probability that at least one out of N r packets is delivered successfully. Since there is no possible current packet collision after the first transmission, PRRs after the first packet transmission in the proposed enhancement are

Combining (38) with (37), we derive the PRR for the suggested enhancement as

4. Model Validation and Numerical Results
In this section, given a specific DSRC environment, performance of IEEE 802.11a for DSRC and performance of the proposed enhancement are derived and compared. We consider a two-lane high freeway system where all vehicles are exponentially distributed. Each vehicle moves on the road with average velocity 60 miles per hour in two directions. The average relative speed of two vehicles is 120 miles per hour. Each vehicle on the road is equipped with DSRC wireless ad hoc network capability with communication parameters shown in Table 2. The control channel is exclusively used for safety-related broadcast communication. Transmission range of each vehicle is 500 miles. The impact of hidden terminal, high mobility, message length and message arrival rate, variable date rate, and carrier sensing range in IEEE 802.11a is all embodied in the numerical computations and the simulations.
4.1. Model Validation
In order to validate the proposed analytic model, we write our own event-driven simulation program in MATLAB. Our simulation is conducted under a highway DSRC environment within road length of 5000 miles. The simulation program includes main physical (except modulation, demodulation, and coding) and MAC behavior of IEEE 802.11 broadcast ad hoc communication with DSRC parameters. The program adopts assumptions that both vehicles on the road and packet generation interval are exponentially distributed. According to the results from [24], intervehicle spacing in a network that is disconnected due to low traffic volume can be characterized by exponential distribution. With distributed asynchronous channel access and limited transmission range and carrier sensing range, the consecutive freeze effect in IEEE 802.11 DCF, asynchronous time scale, and the hidden terminal problem are naturally reflected in the simulation process. The time resolution of the simulation program is exactly the minimum time unit (1 μ s) specified in IEEE 802.11 standard. Each simulation round lasts 1200 seconds.
Figures 4, 5, and 6 depict the channel throughput, the one-hop packet delivery delay, and one-hop packet reception rates, respectively, over the density of vehicles on the road with varied data rates and packet arrival rates. As we see from these figures, analytical results (lines) practically coincide with the simulation counterparts (symbols). The differences between simulation results and theoretic results when offered traffic is heavy are mainly due to limited road range in the simulation, limited precision of numerical differentiations in the theoretic computations, and possible asynchronous slots among vehicles in the ad hoc network.
Comparing the obtained reliability and performance under typical DSRC environment with requirements set for safety-related ad hoc communication network, we can see that it is no problem for packet delivery delay for emergency safety service (<1.2 milliseconds) to meet the requirement (500 milliseconds); it is even not a problem for routine safety service to reach its 5 hops away destination (2.5 kilometers) within 5 × 2 milliseconds = 10 milliseconds. However, the obtained packet reception rates (<0.8) fail to meet reliability requirement ( ) for DSRC safety critical messaging.
) for DSRC safety critical messaging.
4.2. Observations and Discussions
From Figure 4–6, it is observed that increasing data rate (from 24 Mbps to 54 Mbps) helps significantly improve the delay. However, increasing data rate reduces the channel throughput under unsaturated channel condition. Data rate changes have minor effect on packet reception rate. As the road traffic is getting heavier (<0.2 vehicles/mile), transmission delays and packet reception rates are getting worse, but channel throughputs are increased accordingly because the channel is still unsaturated.
As seen in Figures 4 and 7, As a result of two-level priority scheme with different backoff window sizes, the packet delivery delays of the event-driven message are much shorter than that of periodic routine message (e.g., in Figure 4, when traffic density is 0.1,  millisecond;
millisecond;  millisecond). From Figure 7, we also observe that increasing message generation rates in each vehicle prolongs packet delivery time significantly.
millisecond). From Figure 7, we also observe that increasing message generation rates in each vehicle prolongs packet delivery time significantly.
Figure 8 shows how hidden terminal problem and mobility of vehicle affect PRRs of the DSRC broadcast communication. We observe that the hidden terminal problem degrades PRRs significantly. On the other hand, curves without accounting for mobility and that with taking mobility into account are almost overlapped, indicating higher mobility of vehicles does not significantly affect PRRs. Since the ad hoc broadcast network we consider here for safety application adopts short message, high date rate, and one-hop direct message sending, the link breaking probability due to mobility of vehicles is very small during a packet transmission period.
4.3. Impact of Enhancement
Figures 9 and 10 show the impact of enhancement strategies suggested in Section 2 on reliability and performance of the DSRC safety message broadcast networks (in Figures 9 and 10, the curves with  reflect, resp., delay and PRR without the enhancement). As observed from Figure 10, the PRRs for emergency safety messages reach to 0.998 even with high traffic load as the preemptive broadcast with 5 packet repetitions and bigger backoff window size (256) is applied, indicating that it is possible to enhance packet reception rate to a certain level that meets the safety requirement for reliability
reflect, resp., delay and PRR without the enhancement). As observed from Figure 10, the PRRs for emergency safety messages reach to 0.998 even with high traffic load as the preemptive broadcast with 5 packet repetitions and bigger backoff window size (256) is applied, indicating that it is possible to enhance packet reception rate to a certain level that meets the safety requirement for reliability  as preemptive priority is given to emergency messages, and some system parameters are carefully chosen.
as preemptive priority is given to emergency messages, and some system parameters are carefully chosen.
As shown in Figure 9, although the enhancement brings longer packet delivery delay, the maximum delay introduced ( milliseconds) is still much less than the required message lifetime 500 milliseconds. Increasing the number of message repetitions N
r
and carrier sensing range (
milliseconds) is still much less than the required message lifetime 500 milliseconds. Increasing the number of message repetitions N
r
and carrier sensing range ( ) helps improve reliability of safety message transmission. But as emergency traffic is getting higher (
) helps improve reliability of safety message transmission. But as emergency traffic is getting higher ( pck/s in Figure 10), excessive repetitions may make the PRRs worse instead (see the curve with
pck/s in Figure 10), excessive repetitions may make the PRRs worse instead (see the curve with  ). The reason for the observation is that increasing N
r
actually increases time period on which a transmitting vehicle occupies the channel, thus bringing more chances of collisions and interference. It is noticed that optimal selection of N
r
depends on network environment, network parameters, and vehicle traffic on the road.
). The reason for the observation is that increasing N
r
actually increases time period on which a transmitting vehicle occupies the channel, thus bringing more chances of collisions and interference. It is noticed that optimal selection of N
r
depends on network environment, network parameters, and vehicle traffic on the road.
5. Conclusions
In this paper, we investigate reliability and performance of DSRC ad hoc V2V communication networks with two levels of safety-related services analytically and by simulation. Several important performance indices for broadcast such as channel throughput, packet reception rates, and packet delivery delay are derived from the proposed analytical model taking IEEE 802.11 backoff counter process, fading channel, hidden terminal, nonsaturation traffic, mobility, and so forth, into account. Numerical results reveal characteristics of the DSRC communication system for safety application. From the analysis of DSRC safety services on highway, we observe that (1) under typical DSRC environment, IEEE 802.11a is able to meet the safety message delay requirement, but is not able to guarantee high reliability because of possible transmission collision and harsh channel fading; (2) hidden terminal problem in broadcast is more severe than that in unicast; (3) high mobility of vehicles has minor impact on the reliability and performance of the direct single hop broadcast network with high data rate; (4) with direct broadcast and preemptive emergent message transmission, it is possible to meet both performance requirement and reliability requirement simultaneously through adjusting backoff window size, appropriate number of packet repetitions, and enough range of carrier sensing.
Our future research work will focus on development and analysis of new effective and robust MAC protocols toward 802.11p, which includes adaptively adjusted network parameters in terms of current traffic load and network situation for optimized performance and reliability.
References
Zhu J, Roy S: MAC for dedicated short range communications in intelligent transport system. IEEE Communications Magazine 2003, 41(12):60-67. 10.1109/MCOM.2003.1252800
Federal Communications Commission. FCC 03-324. FCC Report and Order February 2004.
Dedicated Short-Range Communication (DSRC) Working Group http://grouper.ieee.org/groups/index.html
Su H, Zhang X, Chen H-H: Cluster-based DSRC architecture for QoS provisioning over vehicle ad hoc networks. Proceedings of IEEE Global Telecommunications Conference (GLOBECOM '06), November-December 2006, San Francisco, Calif, USA 1-5.
ASTM E2213-03 : Standard Specification for Telecommunications and Information Exchange Roadside and Vehicle Systems—5 GHz Band Dedicated Short Range Communications (DSRC) Medium Access Control (MAC) and Physical Layer (PHY) Specifications. Sepember 2003.
Blum JJ, Eskandarian A, Hoffman LJ: Challenges of intervehicle ad hoc networks. IEEE Transactions on Intelligent Transportation Systems 2004, 5(4):347-351. 10.1109/TITS.2004.838218
Xu Q, Mak T, Ko J, Sengupta R: Vehicle-to-vehicle safety messaging in DSRC. Proceedings of the 1st ACM International Workshop on Vehicular Ad Hoc Networks (VANET '04), October 2004, Philadelphia, Pa, USA 19-28.
Torrent-Moreno M, Jiang D, Hartenstein H: Broadcast reception rates and effects of priority access in 802.11-based vehicular ad-hoc networks. Proceedings of the 1st ACM International Workshop on Vehicular Ad Hoc Networks (VANET '04), October 2004, Philadelphia, Pa, USA 10-18.
Jiang D, Taliwal V, Meier A, Holfelder W, Herrtwich R: Design of 5.9 GHz DSRC-based vehicular safety communication. IEEE Wireless Communications 2006, 13(5):36-43.
ElBatt T, Goel SK, Holland G, Krishnan H, Parikh J: Cooperative collision warning using dedicated short range wireless communications. Proceedings of the 3rd ACM International Workshop on Vehicular Ad Hoc Networks (VANET '06), September 2006, Los Angeles, Calif, USA 1-9.
Yin J, ElBatt T, Yeung G, et al.: Performance evaluation of safety applications over DSRC vehicular ad hoc networks. Proceedings of the 1st ACM International Workshop on Vehicular Ad Hoc Networks (VANET '04), October 2004, Philadelphia, Pa, USA 1-9.
Gupta P, Kumar PR: Critical power for asymptotic connectivity in wireless networks. In Stochastic Analysis, Control, Optimization and Applications: A Volume in Honor of W. H. Fleming. Birkhäuser, Boston, Mass, USA; 1998:547-566.
Choi J-M, So J, Ko Y-B: Numerical analysis of IEEE 802.11 broadcast scheme in multihop wireless ad hoc networks. Proceedings of the International Conference on Information Networking (ICOIN '05), January-February 2005, Jeju, Korea 1-10.
Ma X, Chen X: Delay and broadcast reception rates of highway safety applications in vehicular ad hoc networks. Proceedings of IEEE Workshop on Mobile Networking for Vehicular Environments (MOVE '07), May 2007, Anchorage, Alaska, USA 85-90.
Torrent-Moreno M, Killat M, Hartenstein H: The challenges of robust inter-vehicle communications. Proceedings of the 62nd IEEE Vehicular Technology Conference (VTC '05), September 2005, Dallas, Tex, USA 319-323.
ANSI/IEEE Std. 802.11 : Part 11: wireless LAN medium access control (MAC) and physical layer (PHY) specifications. September 1999
Biswas S, Tatchikou R, Dion F: Vehicle-to-vehicle wireless communication protocols for enhancing highway traffic safety. IEEE Communications Magazine 2006, 44(1):74-82.
Cheng S-T, Wu M: Performance evaluation of ad-hoc WLAN by M/G/1 queueing model. Proceedings of the International Conference on Information Technology: Coding and Computing (ITCC '05), April 2005, Las Vegas, Nev, USA 2: 681-686.
Farhadi G, Beaulieu NC: Connectivity and bit error rate analysis of mobile ad hoc wireless networks. Proceedings of the 64th IEEE Vehicular Technology Conference (VTC '06), September 2006, Montreal, Canada 2644-2648.
Simon MK, Alouini MS: Digital Communications over Fading Channels: A Unified Approach for Performance Analysis. John Wiley & Sons, New York, NY, USA; 2000.
Ma X, Chen X: Saturation performance of IEEE 802.11 broadcast networks. IEEE Communications Letters 2007, 11(8):686-688.
Ma X, Chen X, Refai H: On the broadcast packet reception rates in one-dimensional MANETs. Proceedings of IEEE Global Telecommunications Conference (GLOBECOM '08), November-December 2008, New Orleans, La, USA 1-5.
Trivedi KS: Probability and Statistics with Reliability, Queuing and Computer Science Applications. 2nd edition. John Wiley & Sons, New York, NY, USA; 2002.
Tonguz O, Wisitpongphan N, Bai F, Mudalige P, Sadekar V: Broadcasting in VANET. Proceedings of IEEE Workshop on Mobile Networking for Vehicular Environments (MOVE '07), May 2007, Anchorage, Alaska, USA 7-12.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License (https://creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Ma, X., Chen, X. & Refai, H.H. Performance and Reliability of DSRC Vehicular Safety Communication: A Formal Analysis. J Wireless Com Network 2009, 969164 (2009). https://doi.org/10.1155/2009/969164
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1155/2009/969164
 and the lower priority class uses the window
and the lower priority class uses the window 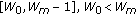 .
. of finding i vehicles in length of l is given by
of finding i vehicles in length of l is given by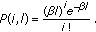
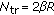 .
.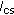 which is assumed to vary between the range
which is assumed to vary between the range  . The average number of vehicles in carrier sensing range of the tagged vehicle on the road is
. The average number of vehicles in carrier sensing range of the tagged vehicle on the road is 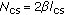 .
.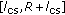 and
and 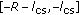 assuming that the carrier sensing range equals the range within which one node interferers with other node. The average number of the potential hidden vehicles of the tagged vehicle on the road is
assuming that the carrier sensing range equals the range within which one node interferers with other node. The average number of the potential hidden vehicles of the tagged vehicle on the road is 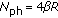 .
.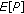 ; both arrivals are Poisson processes with rates
; both arrivals are Poisson processes with rates  and
and 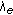 (in packets per second), respectively.
(in packets per second), respectively.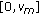 , where
, where  is the maximum relative speed. The average relative velocity of two vehicles in the network is assumed to be a constant value
is the maximum relative speed. The average relative velocity of two vehicles in the network is assumed to be a constant value  .
.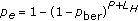 , where P is the length of the packet,
, where P is the length of the packet,  is the length of packet header, and
is the length of packet header, and 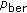 is the fixed bit error rate (BER) probability.
is the fixed bit error rate (BER) probability. 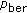 can be numerically evaluated for a Rician fading channel [
can be numerically evaluated for a Rician fading channel [ can be easily obtained using the closed form expressions given in [
can be easily obtained using the closed form expressions given in [



 miles,
miles,
 bytes,
bytes,
 pck/s,
pck/s,
 pck/s.
pck/s.

 bytes,
bytes,
 pck/s,
pck/s,
 pck/s.
pck/s.

 miles,
miles,
 bytes,
bytes,
 pck/s,
pck/s,
 pck/s.
pck/s.

 miles,
miles,
 Mbps,
Mbps,
 bytes,
bytes,
 pck/s.
pck/s.

 miles,
miles,
 Mbps,
Mbps,
 bytes,
bytes,
 pck/s.
pck/s.

 miles,
miles,  Mbps,
Mbps,  bytes,
bytes,  .
.