- Research Article
- Open access
- Published:
Introducing an Adaptive Method to Tune Initial Backoff Window (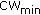 -ATM) in IEEE 802.11 Wireless Networks
-ATM) in IEEE 802.11 Wireless Networks
EURASIP Journal on Wireless Communications and Networking volume 2010, Article number: 323598 (2010)
Abstract
IEEE802.11 access protocol uses CSMA/CA in its Medium Access control layer as the main access function, which carries several deficiencies. In these networks, as the number of active stations increases, delay and throughput degrade severely. As far as throughput and service delay are vital elements in Quality of Service (QoS) determination, such degradation could lead to intolerable situations and reduce the efficiency of WLANs. Networks (WLANs). Studies proved this problem arises due to constant initial backoff windows size ( ), which is an important parameter in determination of network behavior. In this paper, we introduce a new method to tune this parameter adaptively according to changes in channel load. In this method, we do tune this parameter after every transmission using a feedback from transmission channel. Later it will be proven that applying this method in MAC layer enhances network stability; delay trend in all traffic classes exhibits a considerable reduction when compared with simple Enhanced Distributed Coordination Access (EDCA) scenarios. Also throughput exhibits a salient improvement in level. In other word, QoS improves. Especially, with the aid of this method, delay variations in all decrease considerably and more smoothen delay trends are achieved.
), which is an important parameter in determination of network behavior. In this paper, we introduce a new method to tune this parameter adaptively according to changes in channel load. In this method, we do tune this parameter after every transmission using a feedback from transmission channel. Later it will be proven that applying this method in MAC layer enhances network stability; delay trend in all traffic classes exhibits a considerable reduction when compared with simple Enhanced Distributed Coordination Access (EDCA) scenarios. Also throughput exhibits a salient improvement in level. In other word, QoS improves. Especially, with the aid of this method, delay variations in all decrease considerably and more smoothen delay trends are achieved.
1. Introduction
In recent years, desires to utilize Local Area Network (LAN) for communication increased dramatically. Undoubtedly, one of the most important classes of these access networks is IEEE 802.11 that was innovated in 1999 [1]. IEEE 802.11 networks work based on a contention-based access mechanism namely Carrier Sense Multiple Access supported with collision avoidance capability (CSMA/CA). This was the subject of investigation for many researchers during these years [2–4]. As time went by and new, delay sensitive services emerged with real-time requirements, attentions were attracted toward applying diff-serve model on IEEE 802.11 Medium Access control (MAC) layer. Henceforth, many literatures focused on this subject [5–13].
Arrival of IEEE 802.11e standard into scene was a clear response to these efforts that have not been stopped yet. In this paper, we follow the idea behind [14–16] which is improving the 802.11 MAC performance using a channel adaptive backoff scheme. We investigate the merits and shortcomings of Distributed Coordination Function (DCF) and Enhanced Distributed Coordination Access (EDCA) and verify their dependency on network parameters. It would be claimed that using the legacy exponential backoff technique in DCF and EDCA leads to destructive dependence of network performance on initial backoff windows size, number of stations, and network load. This is apparently a drawback from network viewpoint. By applying this adaptive method, each station could periodically estimate network load (by continuously hearing to channel activities). That helps us directly in tuning of  . Simulation results confirm the suitability of this method.
. Simulation results confirm the suitability of this method.
We apply our proposed method on EDCA of IEEE 802.11e to probe its effect on different traffic classes. As DCF is a specific case of EDCA, the totality of argument is reserved.
2. Legacy IEEE 802.11
In this section, we do summarize DCF performance and then limitations of this protocol on supporting Quality of service (QoS) will be discussed.
2.1. DCF
The IEEE 802.11 MAC layer protocol is a distributed coordination function and works based on carrier sense multiple access technique. In this technique, each station transmits its MAC service data units (MSDUs) after sensing the channel and ensuring that no transmission is in progress. In case two or more stations find channel idle and hence transmit simultaneously, the collision occurrence is inevitable. Therefore, IEEE 802.11 working group devised a mechanism, namely, collision avoidance, to reduce the collision probability. In this mechanism, stations start a backoff procedure before transmission; to that end, they should keep silent for a random amount of time immediately after channel remains idle for DCF Inter frame Space (DIFS). The DIFS value considered to be around 34  s in IEEE 802.11a standard. Upon the expiration of this random time, stations are allowed to transmit. The length of this random time should be multiple of slot length. In fact, each station carries a parameter, namely, contention window from which this random time is to be extracted.
s in IEEE 802.11a standard. Upon the expiration of this random time, stations are allowed to transmit. The length of this random time should be multiple of slot length. In fact, each station carries a parameter, namely, contention window from which this random time is to be extracted.
Upon the correct reception of each data frame, recipient terminal transmits an acknowledgement packet back to sender confirming the correct reception of previous data frame. In case a collision occurs, the contention window size is multiplied by a persistent factor (PF) mentioned in standard. This mechanism is named exponential backoff. It would be titled truncated exponential backoff scheme in case there is an upper bound on contention windows size.
All frames that would not be acknowledged during a predefined amount of time (ACK-Timeout) should be scheduled for retransmission; but with a doubled contention window size. This procedure definitely lessens the collision probability when several stations are attempting to access the channel.
Stations that deferred their channel access due to medium busyness, do not initiate a new random backoff time; instead, they continue to count down their most recent frozen values as soon as channel remains idle for at least DIFS. Finally, after each successfully transmitted MSDU, a new random backoff procedure needs to be initiated regardless of the fact that whether the transmitter queue is empty or containing an MSDU (ready to send). This routine is entitled post backoff because of its initiation after each transmission not before that.
Essentially, there is one case in which no backoff procedure is required to be performed, that is, when, the last post backoff has already been finished while the queue is still empty. Thus, an arrived MSDU from higher layer would be immediately transmitted without need to perform a new backoff routine. All other MSDUs coming after last one should be transmitted after this backoff procedure.
In order to reduce the collision length in long frames, the standard suggested fragmentation scheme. In this scheme, long MSDUs should be fragmented to a series of smaller units to be transmitted sequentially one by one and acknowledged as well. The principal benefit of fragmentation is that, in case of collision occurrence, errors are identified in a swifter manner. Apparently, fragmentation's intrinsic drawback is the huge overhead it imposes on network.
In order to confront with hidden terminal problem, which is one of the most prevalent difficulties in CSMA/CA, Request to Send/Clear to Send (RTS/CTS) mechanism is devised. In this mechanism, sender station transmits a short control frame, namely, RTS prior to sending its data frame. Then, RTS recipient replies with another control frame, namely, CTS. Both RTS and CTS frames contain information about the length of following data frame. Following to reception of RTS by terminals in proximity of sender and reception of CTS by hidden terminals in proximity of receiver, all terminals should refrain from sending another frame in order to avoid collision occurrence. In fact, this mechanism helps in protecting system against sending long collided frames, especially in situations where hidden terminal problem is probable. Using Fragmentation, several smaller frames would be transmitted in series whereas using RTS/CTS method, a long frame would be transmitted but with less overhead and in a faster way.
In between each of RTS, CTS, Acknowledgment (ACK), and data transmissions, there should be idle separation intervals, namely, short inter frame space (SIFS) that is lower than DIFS, in length. Short Inter Frame Space (SIFS) value is typically around 
 s (according to IEEE 802.11a specification). Figure 1 illustrates the performance of DCF. As SIFS' length is always smaller than DIFS' length, subsequent frames coming after SIFS intervals are logically furnished with relatively higher priority rather than frames coming after DIFS interval. Such an invention helps in providing ACK, RTS, and CTS with higher priority compared to Data frames.
s (according to IEEE 802.11a specification). Figure 1 illustrates the performance of DCF. As SIFS' length is always smaller than DIFS' length, subsequent frames coming after SIFS intervals are logically furnished with relatively higher priority rather than frames coming after DIFS interval. Such an invention helps in providing ACK, RTS, and CTS with higher priority compared to Data frames.
3. Quality of Service Provisioning Mechanism in 802.11e Access Protocol
In order to support QoS in 802.11 wireless LANs, many proposals have been presented up to now and a lot more are under studying. Recently, IEEE 802.11 task group  approved a new standard by adding few enhancements to MAC layer of IEEE 802.11. The result is a new enhanced distribution coordination function, namely, EDCA. IEEE 802.11e constituted from two distinct access phases, namely, contention period (CP) phase and contention free period (CFP) phase. These two phases alternate steadily in a superframe framework over time. Like DCF, EDCA is a contention-based protocol that is utilized in CP phase.
approved a new standard by adding few enhancements to MAC layer of IEEE 802.11. The result is a new enhanced distribution coordination function, namely, EDCA. IEEE 802.11e constituted from two distinct access phases, namely, contention period (CP) phase and contention free period (CFP) phase. These two phases alternate steadily in a superframe framework over time. Like DCF, EDCA is a contention-based protocol that is utilized in CP phase.
3.1. EDCA
Now we commence with a definition of access category (AC). AC is the classification of different traffic classes in order to serve them with different requirements. To each AC in a station, a distinct EDCA is dedicated. They perform backoff procedure and act independently from each other. Here, backoff procedure starts immediately after channel stays idle for AIFS duration. Depending on physical characteristic of each AC, Arbitration Inter Frame Space (AIFS) might extend from DIFS, which is the bottom value, to larger amounts. Immediately after waiting for AIFS, each backoff entity sets its counter to an integer value extracted uniformly from  interval where Contention Window (CW) in each AC varies from a minimum value, namely,
interval where Contention Window (CW) in each AC varies from a minimum value, namely,  , up to the bound
, up to the bound  .
.
For traffic category  , let
, let  denote contention window size at
denote contention window size at  retransmission stage and let
retransmission stage and let  denote the maximum contention window size. Also,
denote the maximum contention window size. Also,  ,
,  , and
, and  are, respectively, retry limit, persistent factor and number of retransmissions after which
are, respectively, retry limit, persistent factor and number of retransmissions after which  stays constant. (All in class
stays constant. (All in class  .) Below equation encompasses all these parameters and shows their interaction with each other.
.) Below equation encompasses all these parameters and shows their interaction with each other.

Meanwhile,  value is equal to
value is equal to

Figure 2 illustrates EDCA contention in different classes with different priorities.
Figure 3 is the Two-Dimensional Markov chain of backoff mechanism in IEEE 802.11e networks.
Here, it just suffices to mention common equations of 802.11 and 802.11e networks without any proof. These equations are simply derivable from the discrete time Two-Dimensional Makov chain devised by Bianchi. We refer interested readers to [17, 18] for more details. Fundamentally, the transmission probability in class i, is the probability that a station belonging to this class transmits at a given time slot. Furthermore, the collision probability in this class is the probability that a transmitted frame from a station belonging to this class collides with a transmission from another station. Finally, the busyness probability is an indication of the chance of having busy channel at a given time slot (successful transmission or collision). We express transmission probability by  , collision probability by
, collision probability by  , and busyness probability by
, and busyness probability by  . Below
. Below  ,
, ,
, , respectively represent traffic category of that station (or queue), retransmission stage, and value of backoff counter in each retransmission stage. Therefore,
, respectively represent traffic category of that station (or queue), retransmission stage, and value of backoff counter in each retransmission stage. Therefore,



If we define the successful transmission probability as the situation in which at a given time slot all stations refrain from transmission except one, then below equation would be apparent for this parameter:

In above set of equations,  corresponds to the number of traffic categories exist in network and
corresponds to the number of traffic categories exist in network and  to the number of active stations surviving at class
to the number of active stations surviving at class  . The absolute success probability at a given station belonging to class i (instead of conditional one computed above) is achieved after removing the condition in (6) dividing it by
. The absolute success probability at a given station belonging to class i (instead of conditional one computed above) is achieved after removing the condition in (6) dividing it by  . Hence,
. Hence,

Now we are ready to introduce two important quantities that will be exploited in our next section treatments; the first one is the mean number of station retries to transmit its packet successfully; the second one is the mean number of consecutive idle slots in an idle burst. These two quantities play important roles in our treatments (referring to [18]):

Up to now, we have presented formulas for EDCA. Hereafter, to the end of this section (and for the reason of simplification), we get back to DCF and extract a simplified equation for transmission probability based on absolute collision probability, p. According to [17], the transmission probability in DCF mode would be equal to

Assuming  (9) gets more simplified for
(9) gets more simplified for  versus CW and
versus CW and  ,
,

Figure 4 demonstrates that for larger  and smaller
and smaller  , the difference between two curves is trivial and the approximation is well.
, the difference between two curves is trivial and the approximation is well.
The larger the value of  (the lower the value of
(the lower the value of  ), the better two curves fit each other.
), the better two curves fit each other.
A delicate difference between DCF and EDCA is regarding the exact time that frozen counters start to decrease. In DCF, decrement occurs at the edge of first slot coming immediately after DIFS idle time, whereas in EDCA the counter reduction is accomplished at the first edge of last AIFS idle slot. Although this little difference may not lead to a tangible influence on performance, it makes the analysis more convenient in EDCA case.
In EDCA mechanism, each station may have up to eight internal queues, each one representing a virtual station working independent of each other. In addition, each queue has its dedicated QoS parameters. When, two or more ACs (queue) inside a station attempt to transmit simultaneously, the virtual collision handler is activated. In this mechanism, among those ACs engaged in collision, the one with higher priority transmits right away and others refrain from transmission. This is in contrast with real collision situations in which two real concurrent transmissions lead to real collisions. Figure 5 illustrates this situation.
3.2. EDCA Performance Evaluation
In order to gain deeper understanding of our dynamic tuning scheme, we establish a set of simulations to study EDCA basic performance. The aim of this section is to prove that differentiation mechanism is only a tradeoff between different classes and cannot improve the overall level of QoS in network. In other word, using differentiation methods, when one of QoS metrics (Throughput, Delay, Utilization...) improves in some classes, we should certainly expect to see degradation in other classes (on the same metric).
We utilized predefined model of IEEE 802.11e existing in Opnet modeler.14 [19]. In this set of simulations, we apply constant traffic load to a group of stations. Traffic is generated based on exponential interarrival rate and constant payload size, the condition that happens in many real situations. We set Mean interarrival time to 0.005 second and mean packet size to 1500 byte, what envisaged being a high load condition. In order to set up a stable working condition, an offset time should elapse after simulation beginning and before traffic generation in stations. To evaluate EDCA performance, three traffic categories have been defined; first, interactive multimedia class; second, interactive voice class; third, Best effort class.
The exploited topology is a ring of radius 20 meter over which 6 stations placed in equal distances. Each two stations belong to the same class standing face to face. No channel fading or noise effects are considered in these scenarios and the only source of error is collision. Also hidden terminal possibility is avoided by putting all stations in hearing range of each other. For the sake of comparison, all three ACs benefit from the same traffic load condition. Other physical layer parameters are cited at Table 1.
It is important to note that, no access point functionality is considered in this article and all stations work in a distributed arrangement as illustrated in Figure 6.
Note that stations in each class only interact with each other, not with stations of other classes; that is to say voice by voice and video by video. At this section, we establish two sets of simulations; firstly, we evaluate network behavior by changing application load and secondly, we evaluate performance by changing MAC layer parameters like  , Transmission Opportunity (TXOP), and AIFS. In the first set, we apply MAC parameters as mentioned in Table 2.
, Transmission Opportunity (TXOP), and AIFS. In the first set, we apply MAC parameters as mentioned in Table 2.
Figure 7 depicts load level and load variation for each of the tree scenarios. In each scenario, we have 100% load increment than last scenario. Figure 8 depicts total delay for these three different load conditions. This plot emphasizes that as stations' load grows larger, delays increase boundlessly.
Figure 9 shows delay trends of voice class for three different load situations (with 100% growth rate at each situation). As other two classes exhibited the same trend as the voice class, we avoid showing them in this place.
Figures 10 and 11 show, respectively, Delay-Time trend and Delay-CDF (Cumulative Distribution Function) trend in all three classes under highest load condition (0.005 second). The comparisons simply reveal that higher priority class has greater chance to access the channel.
Now it is time to observe other parameters' effects (like  , TXOP, and AIFS) on EDCA performance. Let us start with
, TXOP, and AIFS) on EDCA performance. Let us start with  . Firstly, we change
. Firstly, we change  in both voice classes simultaneously and equally and observe its changing effects on delay value of all classes. As it is obvious, this changing should have direct influence on voice class delay as well as other class delays. However, the interesting fact is something else. The totals mean delay never changes in these scenarios; but what happens is just a simple tradeoff between classes meaning that higher priority class grasps more chance to transmit while the lower priority class looses it, and hence it starves; but the total mean stays always intact. Figures 12 and 13 are good illustrations to envisage the situation. All parameter is the same as Table 2 but the voice class
in both voice classes simultaneously and equally and observe its changing effects on delay value of all classes. As it is obvious, this changing should have direct influence on voice class delay as well as other class delays. However, the interesting fact is something else. The totals mean delay never changes in these scenarios; but what happens is just a simple tradeoff between classes meaning that higher priority class grasps more chance to transmit while the lower priority class looses it, and hence it starves; but the total mean stays always intact. Figures 12 and 13 are good illustrations to envisage the situation. All parameter is the same as Table 2 but the voice class  that takes three values: 7, 31, and 63.
that takes three values: 7, 31, and 63.
Because the best effort class showed the same trend as video class, we avoid mentioning it here. By aggregating delays in all classes, we reach to below plot that discloses an important fact. The differentiation mechanism has no impact on overall delay improvement but instead is just a simple interclass tradeoff. This is evident from Figure 14 that mean values are equal but depending on many factors we may decrease or increase delay variation (Jitter).
Now we have enough tools in hand to follow our aim, which is our novel adaptive tuning method.
4. Adaptive Method of Tuning Initial Backoff Windows Size
As a starting point in this section, we go over a simple generic definition for throughout; this universal definition is the amount of successfully transmitted payload in a transmission period. Therefore,

This equation is logical and need no more explanation. In order to find an optimized point at which delay is minimized (and consequently throughput maximized), it is necessary to find the maximal point of above equation by taking first derivative and equating it to zero. Therefore,

This could be possible only if  . After derivation and algebraic simplification:
. After derivation and algebraic simplification:

The intersection point at Figure 15 represents the value of  at which Throughput maximized.
at which Throughput maximized.
By further simplification in right hand side of equation, we reach to

Now we merge (14) with (10):

Using this equation we could adaptively compute  as a function of n (each terminal estimation of number of contending stations is not the real number of stations!),
as a function of n (each terminal estimation of number of contending stations is not the real number of stations!),  , and
, and  . This equation constitutes the heart of our recycling flowchart in third stage (Figure 16).
. This equation constitutes the heart of our recycling flowchart in third stage (Figure 16).
4.1. Schematic Diagram
To accomplish our task, we have drawn a schematic cyclic flowchart. Let us proceed through its all stages to derive appropriate practical equations. Up to now, we have derived a suitable equation for third stage (14). Now, its first stage's turn!
4.1.1. Stage I
Let us suppose  to be the number of busy slots observed by an observing station during a period of length B. Therefore, it is logical to infer that the channel busyness probability from this station's perspective would be equal to
to be the number of busy slots observed by an observing station during a period of length B. Therefore, it is logical to infer that the channel busyness probability from this station's perspective would be equal to

By the second order approximation of  term using Newton's equation, it turns possible to simplify above equation as
term using Newton's equation, it turns possible to simplify above equation as

By further simplification of this equation and arranging  as a function of
as a function of  and
and  and Coupling it with (10) below equation is obtained:
and Coupling it with (10) below equation is obtained:

This is a simple, linear, and effective equation and permits each station to estimate the number of contending terminal every time required. In cases of small busyness probability, (light contention)  is a suitable and tight approximation for
is a suitable and tight approximation for  ; thus, a linear equation with least difficulty in computations is obtained. As
; thus, a linear equation with least difficulty in computations is obtained. As  and
and  are closely equal, we could apply them interchangeably.
are closely equal, we could apply them interchangeably.
4.1.2. Stage II
In order to avoid rapid and undesirable changes in  , which arise from incorrect estimation of
, which arise from incorrect estimation of  or
or  by stations, we devised an effective solution with less error that could furnish network with larger stability and persistency. To that end, we utilize a buffer to save several consecutive
by stations, we devised an effective solution with less error that could furnish network with larger stability and persistency. To that end, we utilize a buffer to save several consecutive  values. Then, by applying a weighted normalization routine to these consecutive values, an implicit stabilizer is formed:
values. Then, by applying a weighted normalization routine to these consecutive values, an implicit stabilizer is formed:

Clearly,  and q are both constant values that are tunable depending on requirements. The larger
and q are both constant values that are tunable depending on requirements. The larger  results in more variable and instantaneous
results in more variable and instantaneous  and hence an unreliable behavior with greater variations, but with swifter acting accomplished. Despite that, the smaller
and hence an unreliable behavior with greater variations, but with swifter acting accomplished. Despite that, the smaller  value leads to stable
value leads to stable  behavior with little variation and slow movements.
behavior with little variation and slow movements.
4.1.3. Stage III
At this stage we apply (15) to adaptively compute  as a function of
as a function of  (which is an estimation of channel traffic). Finally, this initial window value will be exploited by stations for next transmissions.
(which is an estimation of channel traffic). Finally, this initial window value will be exploited by stations for next transmissions.
4.1.4. Stage IV
As long as  value stays constant during backoff periods, we may expect trivial performance improvement when working in adaptive tuning mode. To achieve better improvements, it is better to tune
value stays constant during backoff periods, we may expect trivial performance improvement when working in adaptive tuning mode. To achieve better improvements, it is better to tune  at each stage according to an appropriate logic. We have verified the fitness of below set of equations (20) and a comparison done with a scenario in which
at each stage according to an appropriate logic. We have verified the fitness of below set of equations (20) and a comparison done with a scenario in which  stayed static. The comparison proved a sensible improvement in all quantities when dynamically tuning
stayed static. The comparison proved a sensible improvement in all quantities when dynamically tuning  . For clarification, imagine below axis (Figure 17) that divided into separate divisions by straight lines. Each part is a backoff period during which a packet will be transmitted successfully after several trials. In addition,
. For clarification, imagine below axis (Figure 17) that divided into separate divisions by straight lines. Each part is a backoff period during which a packet will be transmitted successfully after several trials. In addition,  shows the mean variation of
shows the mean variation of  during
during  last periods. We are interested to find
last periods. We are interested to find  for next period based on most recent
for next period based on most recent  (namely,
(namely,  ). Thus, we follow these equations:
). Thus, we follow these equations:

As it is evident, our goal from exploiting several summations in this set of equations is to have a smoother  as far as possible. The principal philosophy behind using the right hand side equation is that, upon an abrupt change in
as far as possible. The principal philosophy behind using the right hand side equation is that, upon an abrupt change in  of previous stage, the
of previous stage, the  increases automatically to provide more dependency on exactly former
increases automatically to provide more dependency on exactly former  rather than farther ones (refer to equation
rather than farther ones (refer to equation ).
).
Finally, when there was no variation in last stage of  ,
,  remains almost unchanged. We release further explanation at this point.
remains almost unchanged. We release further explanation at this point.
5. Simulation Results
In this section, we present simulation results of adaptive tuning method proposed in last section. Again, all results are achieved by applying network parameters mentioned in Tables 1 and 2. In addition, all traffic generation parameters are the same as what mentioned in Section 3.2 except interarrival time that is set to be 0.005 s in these set of simulations.
We evaluated several performance measures like Delay (Media access delay), Jitter, Throughput, Retransmission Attempts, and utilization to support our claims as strong as possible. We compare our proposed scheme with common EDCA in IEEE 802.11e. First, let us go over delay. Figure 18 shows the superiority of adaptive scheme against EDCA for total delay parameter.
Since Jitter (Delay Variation) is premier parameter in telecommunication than absolute delay, Figure 19 demonstrates how in addition to gaining smaller delay, even smaller jitter is achieved in adaptive method. In fact, the narrower picked PDF is the evident to this claim.
Another important parameter is total retransmission attempt. It is the total number of retransmission attempts until either a packet is successfully transmitted or it is discarded (because of reaching short or long retry limit). Figure 20 shows this parameter lessened considerably because collision probability is minor in adaptive method.
Utilization is the measure of the consumption to date of available channel bandwidth. This quantity ranges between 0–100 where a value of 100.0 would indicate full usage. Figure 21 presents utilization improvement for three classes.
At last, Throughput results presented in Figure 22, which is the total data traffic in bits/sec are successfully received and forwarded to the higher layer by each access category of the WLAN MAC. Here, we only present total throughput because we are interested to know how  -ATM affect overall system performance. This figure shows that total throughput increases in adaptive method. The underneath reason is the decreased collision probability that have direct influence on decreasing the number of packets dropped due to retry threshold exceeding and ones dropped due to overflow. Hence, throughput increases.
-ATM affect overall system performance. This figure shows that total throughput increases in adaptive method. The underneath reason is the decreased collision probability that have direct influence on decreasing the number of packets dropped due to retry threshold exceeding and ones dropped due to overflow. Hence, throughput increases.
6. Conclusion
In this paper, we presented a novel adaptive tuning method. We proved that applying this method on MAC layer of 802.11 family networks improves network performance and stability in a sensible manner. Early in this paper, we have established a simple set of simulations on 802.11e networks to give readers a wider perspective of what followed latter. Then simulation results of our adaptive method are presented and compared with simple legacy EDCA results. The comparisons demonstrated that delay, throughput, retransmission attempt, and utilization were all positively impacted when applying it in backoff procedure of EDCA. These are all network quantities that could be considered. The differences between results were far enough to decisively vote to suitability of this method.
In the coming paper, we proposed a new QoS improving method based on prioritization. We showed that it is possible to combine  -ATT and differentiation methods in order to achieve better QoS in 802.11e networks.
-ATT and differentiation methods in order to achieve better QoS in 802.11e networks.
References
Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications IEEE standards 802.11, January 1997
Chhaya MS, Gupta S: Performance modeling of asynchronous data transfer methods of IEEE 802.11 MAC protocol. Wireless Networks 1997, 3(3):217-234. 10.1023/A:1019109301754
Kumar A, Altman E, Miorandi D, Goyal M: New insights from a fixed-point analysis of single cell IEEE 802.11 WLANs. IEEE/ACM Transactions on Networking 2007, 15(3):588-601.
Tay YC, Chua KC: A capacity analysis for the IEEE 802.11 MAC protocol. Wireless Networks 2001, 7(2):159-171. 10.1023/A:1016637622896
Deng J, Chang R-S: A priority scheme for IEEE 802.11 DGF access method. IEICE Transactions on Communications 1999, E82-B(1):96-102.
Xiao Y: A simple and effective priority scheme for IEEE 802.11. IEEE Communications Letters 2003, 7(2):70-72. 10.1109/LCOMM.2002.808370
Veres A, Campbell AT, Barry M, Sun L-H: Supporting service differentiation in wireless packet networks using distributed control. IEEE Journal on Selected Areas in Communications 2001, 19(10):2081-2093. 10.1109/49.957321
Aad I, Castelluccia C: Differentiation mechanisms for IEEE 802.11. Proceedings of the 20th Annual Joint Conference on the IEEE Computer and Communications Societies (INFOCOM '01), April 2001, Anchorage, Alaska, USA 1: 209-218.
Pallot X, Miller LE: Implementing message priority policies over an 802.11 Based mobile ad hoc network. Proceedings of Military Communications Conference (Milcom '01), October 2001, McLean, Va, USA 2: 860-864.
IEEE 802.11e WG : Medium Access Control (MAC) Enhancements for Quality of Service. IEEE 802.11e/D2.0, November 2001
Mangold S, Choi S, May P, Kein O, Hiertz G, Stibor L: IEEE 802.11e Wireless LAN for quality of service. Proceedings of European Wireless, 2002, Florence, Italy 32-39.
Xiao Y: IEEE 802.11 E: QoS provisioning at the MAC layer. IEEE Wireless Communications 2004, 11(3):72-79. 10.1109/MWC.2004.1308952
Xiao Y, Li H, Choi S: Protection and guarantee for voice and video traffic in IEEE 802.11e wireless LANs. Proceedings of the 23rd Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM '04), March 2004, Hong Kong 3: 2152-2162.
Cali F, Conti M, Gregori E: IEEE 802.11 protocol: design and performance evaluation of an adaptive backoff mechanism. IEEE Journal on Selected Areas in Communications 2000, 18(9):1774-1786. 10.1109/49.872963
Weinmiller J, Woesner H, Ebert J-P, Wolisz A: Modified backoff algorithms for DFWMAC's distributed coordination function. Proceedings of the 2nd ITG Fachtagung Mobile Kommunikation, September 1995, Neu-Ulm, Germany 363-370.
Cali F, Conti M, Gregori E: Dynamic tuning of the IEEE 802.11 protocol to achieve a theoretical throughput limit. IEEE/ACM Transactions on Networking 2000, 8(6):785-799. 10.1109/90.893874
Bianchi G: Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal on Selected Areas in Communications 2000, 18(3):535-547. 10.1109/49.840210
Ziouva E, Antonakopoulos T: CSMA/CA performance under high traffic conditions: throughput and delay analysis. Computer Communications 2002, 25(3):313-321. 10.1016/S0140-3664(01)00369-3
Opnet Modeler http://www.opnet.com/
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License (https://creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Tadayon, N., Zokaei, S. Introducing an Adaptive Method to Tune Initial Backoff Window (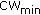 -ATM) in IEEE 802.11 Wireless Networks.
J Wireless Com Network 2010, 323598 (2010). https://doi.org/10.1155/2010/323598
-ATM) in IEEE 802.11 Wireless Networks.
J Wireless Com Network 2010, 323598 (2010). https://doi.org/10.1155/2010/323598
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1155/2010/323598




 is (the lower the value of
is (the lower the value of  ), the better two curves fit each other.
), the better two curves fit each other.
 ) Left figure shown DCF with AIFS = 34
) Left figure shown DCF with AIFS = 34  s,
s,  ,
,  ; (
; ( ) Right figure shown EDCA with AIFS [AC]
) Right figure shown EDCA with AIFS [AC]  34
34  s,
s,  [AC] = 0–255.
[AC] = 0–255.






 value.
value.

 .
.

 has no sensible impact on Overall Delay although each class delay is affected differently.
has no sensible impact on Overall Delay although each class delay is affected differently.



 Tuning.
Tuning.

 -ATM in comparison with EDCA.
-ATM in comparison with EDCA.
 -ATM.
-ATM.
 -ATM and basic EDCA method. Also this parameter lessened considerably because collision probability is minor in
-ATM and basic EDCA method. Also this parameter lessened considerably because collision probability is minor in  -ATM.
-ATM.
 -ATM). Video and best effort class utilization improved (Lessened) but voice class utilization slightly increased.
-ATM). Video and best effort class utilization improved (Lessened) but voice class utilization slightly increased.