- Research Article
- Open access
- Published:
Class-Based Fair Code Allocation with Delay Guarantees for OVSF-CDMA and VSF-OFCDM in Next-Generation Cellular Networks
EURASIP Journal on Wireless Communications and Networking volume 2010, Article number: 738325 (2010)
Abstract
This paper presents a novel class-based fair code allocation (CFCA) protocol to support delay and rate guarantees for real-time flows and to provide fairness for non-real-time flows on the downlink of WCDMA- and VSF-OFCDM-based cellular networks. CFCA not only assigns bandwidth dynamically to different flows but also determines those appropriate OVSF codes whose assignment results in the minimum overhead for code reassignments during dynamic bandwidth allocation. To reduce the overhead of code reassignments, this paper introduces the concept of affinity-mate and enables bandwidth allocation and code placement to interact with each other. A new performance metric, called class-based rate degradation ratio (CRD), is introduced to ensure fairness in providing rate and delay guarantees by measuring the rate degradations of flows based on their traffic types. The simulation results show that code reassignment overhead can be reduced by up to 60% for high network loads. For low network loads, fairness is achieved fully, but for high network loads the average rate requirement is met fairly for 95% of the flows.
1. Introduction
In cellular networks limited radio spectrum is a very important radio resource whose efficient management gets more critical as the bandwidth requirements of new applications increase. A challenging issue in supporting QoS in any wireless cellular network is the time-varying channel conditions due to various types of fading. Employing agile power control alone to counteract variations in channel conditions may cause excessive cochannel interference to other mobile stations in the cell [1]. Also, it is shown in [2] that when compared to fixed-rate power control, adaptive modulation achieves significant throughput advantage. When adaptive modulation is employed instead of power control to counteract the variations in channel conditions, the modulation and coding schemes are varied dynamically based on the varying channel conditions. When channel conditions deteriorate for a user, use of adaptive modulation reduces the data rate achieved by the user because of the use of higher-order modulation and coding scheme. This reduction in data rate impacts the QoS guarantees such as delay and throughput of the user's application. To compensate for the loss in data rate additional bandwidth has to be allocated to the user. Thus, there is a need for dynamic bandwidth allocation. Therefore, an effective dynamic bandwidth allocation algorithm, which dynamically allocates bandwidth with low control signaling overhead to existing mobile users at every time slot based on their channel conditions and delay requirements, is critical in order to meet the QoS requirements and to provide fairness [3]. In this paper, dynamic bandwidth allocation is accomplished by varying the spreading factor assigned to a flow.
Wideband code division multiple access (WCDMA) cellular networks use a CDMA scheme known as OVSF-CDMA [4] to support variable data rates by employing orthogonal variable spreading factor (OVSF) codes. In an OVSF-CDMA-based system, each mobile station is assigned a single OVSF code. Variable data rates are supported by changing the spreading factor (SF). An alternative CDMA scheme known as multicode CDMA (MC-CDMA) [5] assigns multiple codes of the same spreading factor to a mobile station in order to achieve variable data rates. MC-CDMA requires multiple transceivers to support variable data rates. OVSF-CDMA reduces the hardware complexity of the mobile station because it requires only a single transceiver to support variable data rates. However, OVSF-CDMA suffers from the code blocking problem, as explained next.
OVSF codes are generated recursively in a tree fashion, as shown in Figure 1, using Walsh matrices or applying the following rule recursively: code  of level
of level  generates the following two orthogonal codes of level
generates the following two orthogonal codes of level  :
:  and
and  , where
, where  denotes the binary complement of
denotes the binary complement of  ,
,  is the level of the code in the OVSF code tree and
is the level of the code in the OVSF code tree and  is the index of the code at level
is the index of the code at level  , assuming that the root code is at level zero [4, 6]. Any two OVSF codes are orthogonal if and only if one of the two codes is not the ancestor code of the other. For example, in Figure 1 codes
, assuming that the root code is at level zero [4, 6]. Any two OVSF codes are orthogonal if and only if one of the two codes is not the ancestor code of the other. For example, in Figure 1 codes  and
and  are not orthogonal because
are not orthogonal because  is an ancestor code of
is an ancestor code of  and therefore they should not be assigned to two different calls at the same time. When a call is initially admitted, it is assigned an OVSF code with the requested rate by an initial code placement algorithm. Code blocking occurs when there is no corresponding free OVSF code for an incoming call, even though the system has sufficient residual capacity to support it. For example, in Figure 1, a new call requiring an SF = 4 cannot be assigned a code since there is no free code with SF = 4. To mitigate code blocking, an existing call may be reassigned a different OVSF code. For instance, to lift the blocking on
and therefore they should not be assigned to two different calls at the same time. When a call is initially admitted, it is assigned an OVSF code with the requested rate by an initial code placement algorithm. Code blocking occurs when there is no corresponding free OVSF code for an incoming call, even though the system has sufficient residual capacity to support it. For example, in Figure 1, a new call requiring an SF = 4 cannot be assigned a code since there is no free code with SF = 4. To mitigate code blocking, an existing call may be reassigned a different OVSF code. For instance, to lift the blocking on  by freeing
by freeing  , the call of
, the call of  is reassigned with
is reassigned with  , as shown in Figure 1.
, as shown in Figure 1.
Code blocking and reassignment in an OVSF code tree. The filled circle and the crossed circle indicate the assigned and blocked codes, respectively. A free code is indicated by an empty circle. When code  is assigned, it blocks the assignment of its all ancestors and descendants, though its descendants are not shown in this figure. To lift the blocking on
is assigned, it blocks the assignment of its all ancestors and descendants, though its descendants are not shown in this figure. To lift the blocking on  , code
, code  can be freed by assigning
can be freed by assigning  to the call of
to the call of  .
.
Dynamic bandwidth allocation in WCDMA networks involves dynamic assignment of OVSF codes. When dynamic bandwidth allocation is not used, code reassignments are needed to eliminate code blocking only. When dynamic bandwidth allocation is used, code reassignments are needed to dynamically change the data rates assigned to mobile stations as well. The computational overhead can be reduced if the dynamic bandwidth allocation algorithm can easily determine the code to be reassigned for supporting a higher data rate. The control signaling overhead is reduced if fewer number of bits are used to inform the mobile station about the reassigned code. To reduce the code reassignment overhead for a given code, this paper introduces the concept of  -hop affinity-mate to find easily another code with the same or higher rate.
-hop affinity-mate to find easily another code with the same or higher rate.
This paper presents a class-based fair code allocation (CFCA) protocol to support fairness, rate and delay guarantees while allocating codes with low reassignment overhead in WCDMA. CFCA includes three algorithms: class-based code placement (CBP), class-based code replacement (CBR), and dynamic bandwidth allocation (DBA). Algorithm 1 aims to assign each flow a code whose affinity-mate codes can be easily assigned later to the flow in case of stringent delay requirements or poor channel conditions. If the affinity-mate codes of a code are not available, then Algorithm 2 is invoked to assign an appropriate code to the flow that requires a higher-rate code due to poor channel conditions. Both CBP and CBR also undertake reducing the number of code reassignments while eliminating code blocking. Although the existing bandwidth allocation algorithms address rate allocation only without considering code placements and reassignments, Algorithm DBA (see Algorithm 3) enables rate allocation, code allocation and reassignment to interact with each other in order to provide fairness, delay and rate guarantees with low code reassignment overhead.
Algorithm 1: Algorithm CBP.
Input: A new call is admitted to the network because there exists at least one free code to support
the requested data rate. Variable  denotes the maximum
denotes the maximum  in
in  -hop affinity-mate.
-hop affinity-mate.
Output: The new call is assigned a free code with the highest weight  .
.
begin
-
(1)
Let
 denote the number of those free OVSF codes whose SF equals
denote the number of those free OVSF codes whose SF equals  . Label them 1 to
. Label them 1 to  from
fromleft to right.
-
(2)
for
 to
to 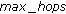 do
do -
(3)
for
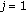 to
to  do
do -
(4)
if(new call is RT (conversational or streaming)) then
-
(5)
if(
 -hop affinity-mate of the free code
-hop affinity-mate of the free code 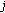 is blocked or being used by an RT call) then
is blocked or being used by an RT call) then -
(6)

-
(7)
else if(
 -hop affinity-mate of the free code
-hop affinity-mate of the free code  is blocked or being used only by NRT calls)
is blocked or being used only by NRT calls)then
-
(8)
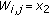
-
(9)
else if(
 -hop affinity-mate of the free code
-hop affinity-mate of the free code 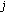 is free) then
is free) then -
(10)
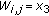
-
(11)
endif
-
(12)
else if(new call is NRT (interactive or background)) then
-
(13)
if(
 -hop affinity-mate of the free code
-hop affinity-mate of the free code  is blocked or being used only by NRT calls) then
is blocked or being used only by NRT calls) then -
(14)
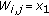
-
(15)
else if(
 -hop affinity-mate of the free code
-hop affinity-mate of the free code  is blocked or being used by an RT call) then
is blocked or being used by an RT call) then -
(16)

-
(17)
else if(
 -hop affinity-mate of the free code
-hop affinity-mate of the free code 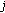 is free) then
is free) then -
(18)

-
(19)
endif
-
(20)
endif
-
(21)
endfor
-
(22)
endfor
-
(23)
The new call is assigned the free code with the highest weight
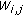 among the
among the  free codes
free codesconsidered at the previous step. If there is more than one code with the highest weight, then
choose the code whose index
 is the smallest to break the tie. Any further ties are broken
is the smallest to break the tie. Any further ties are brokenrandomly.
end
Algorithm 2: Algorithm CBR.
Input: A new call or an existing call that requires a higher-rate code requests a code of SF  . But the
. But the
network does not have a free code of SF  , even though the network has residual capacity to support
, even though the network has residual capacity to support
the call.
Output: An OVSF code of the required SF is freed by reassignment.
Begin
-
(1)
if a new call then
-
(2)
Let
 denote the number of those blocked codes whose SF equals
denote the number of those blocked codes whose SF equals  , and label them from 1 to
, and label them from 1 to  .
. -
(3)
Among the
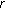 codes determine the codes that have the maximum weight
codes determine the codes that have the maximum weight  for values of
for values of 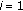
to
 and
and 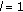 to
to  .
. -
(4)
Determine the code
 that has the least number of busy descendant codes assigned to real-time
that has the least number of busy descendant codes assigned to real-timecalls among the codes with the same maximum weight. Any further ties are broken randomly.
-
(5)
else if a real-time call requires code reassignment to meet its delay requirements then
-
(6)
Let
 denote the number of those codes whose SF equals
denote the number of those codes whose SF equals  . Label them from 1 to
. Label them from 1 to  .
. -
(7)
Determine the code
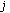 that has the least number of busy descendant codes assigned to real-time
that has the least number of busy descendant codes assigned to real-timecalls. Any further ties are broken randomly.
-
(8)
else if a non-real-time call requires code reassignment to receive fair share of bandwidth then
-
(9)
Let
 denote the number of those codes of
denote the number of those codes of  that are free or assigned or blocked by
that are free or assigned or blocked bynon-real-time calls. If a code of
 is not available, search for a free code of the nearest
is not available, search for a free code of the nearesthigher spreading factor.
-
(10)
Determine the code
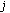 that is assigned to a non-real-time call with the minimum CRD value. Any
that is assigned to a non-real-time call with the minimum CRD value. Anyfurther ties are broken randomly.
-
(11)
endif
-
(12)
Let
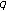 denote the number of calls that are already assigned
denote the number of calls that are already assigned  descendants codes of code
descendants codes of code 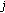 .
. -
(13)
For each call 1 to
 , assign a code using the CBP algorithm, if there are more than one code of
, assign a code using the CBP algorithm, if there are more than one code ofthe required SF
 for the call. If no code is available of the required SF, then call CBR again to
for the call. If no code is available of the required SF, then call CBR again tofree a code of the required SF
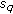 .
. -
(14)
Assign code
 to the new call or to the existing real-time or non-real-time call requesting code
to the new call or to the existing real-time or non-real-time call requesting codereassignments.
end
Algorithm 3: Algorithm DBA.
Input: A WCDMA-based cellular network with limited number of OVSF codes. Every admitted
flow (or call)  is initially assigned an OVSF code, denoted
is initially assigned an OVSF code, denoted  (
( ), and the code
), and the code  (
( ) is
) is
marked "assigned".  is given for every flow
is given for every flow  , and
, and  is common for all flows. count is initially
is common for all flows. count is initially
set to zero.
Output: OVSF codes are assigned to all flows based on their delay and average data rate requirements,
while reducing signaling overhead.
begin
-
(1)
for every frame do
-
(2)
For those flows that have terminated, mark their codes "unassigned".
-
(3)
Assign every flow
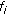 its initial code
its initial code  (
(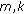 ) even if
) even if  was assigned a different code during
was assigned a different code duringthe transmission of its last frame.
-
(4)
count
 count + 1; for each flow
count + 1; for each flow 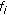 , compute
, compute 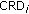 if (count mod
if (count mod 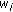 ) = 0.
) = 0. -
(5)
for
 to 3 do
to 3 do -
(6)
if
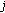 is 0 then
is 0 then -
(7)
class
 "conversational".
"conversational". -
(8)
else if
 is 1 then
is 1 then -
(9)
class
 "streaming".
"streaming". -
(10)
else if
 is 2 then
is 2 then -
(11)
class
 "interactive".
"interactive". -
(12)
else if
 is 3then
is 3then -
(13)
class
 "background".
"background". -
(14)
Let
 equal the number of all those flows of class type.
equal the number of all those flows of class type. -
(15)
while
 and
and  do
do -
(16)
Let
 denote the class flow with the highest CRD value among those class flows that are
denote the class flow with the highest CRD value among those class flows that arenot considered yet in this frame.
-
(17)
if(
 then
then -
(18)
Call ASSIGN_HRC(
 ,
, 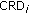 ,
, 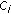 (
(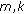 )).
)). -
(19)
else
-
(20)
Use the same code
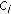 (
( ) of flow
) of flow  in this frame as well.
in this frame as well. -
(21)
endif
-
(22)

-
(23)
endwhile
-
(24)
while
 and
and  do
do -
(25)
Let
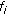 denote the class flow with the highest CRD value among those class flows that
denote the class flow with the highest CRD value among those class flows thatare not considered yet in this frame.
-
(26)
if(
 ) and (Code
) and (Code 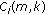 of flow
of flow  are not available due to its assignment to a
are not available due to its assignment to areal-time flow then
-
(27)
Call ASSIGN_HRC (
 ,
,  ,
, 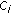 (
( )).
)). -
(28)
else
-
(29)
Use the same code
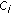 (
( ) of flow
) of flow 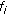 in this frame as well if it is available. Otherwise
in this frame as well if it is available. Otherwiseno code is assigned to flow
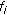 for this frame.
for this frame. -
(30)
endif
-
(31)
-
(32)
endwhile
-
(33)
endfor
-
(34)
endfor
end
This paper also introduces a new performance metric, called class-based rate degradation (CRD), to schedule the code assignments of flows based on their current rate degradation and traffic class. CRD helps meet the delay and rate guarantees for real-time flows and to provide fairness for non-real-time flows. Hence, the main contributions of this paper are fourfold: (i) the code placement algorithm CBP for reducing the overhead significantly for dynamic bandwidth allocation in WCDMA networks, (ii) the code reassignment algorithm CBR for freeing blocked codes if a cellular network has sufficient residual capacity, (iii) the dynamic bandwidth allocation algorithm DBA that uses the proposed CRD metric to provide delay and rate guarantees for real-time traffic, and fair access for non-real-time traffic, and (iv) the concept of  -hop affinity-mate for reducing overhead in code reassignments during dynamic bandwidth allocation.
-hop affinity-mate for reducing overhead in code reassignments during dynamic bandwidth allocation.
While WCDMA-based cellular networks use OVSF codes for channel allocation, variable spreading factor orthogonal frequency code division multiplexing (VSF-OFCDM) has been proposed as the transmission scheme for 4G next-generation cellular networks [7–9]. In VSF-OFCDM, spreading is done both in the time and in the frequency domains. The amount of time and frequency domain spreading can be adapted dynamically based on the data rate requirements and channel conditions of the user. OVSF codes can be used to determine the time domain and frequency domain spreading in VSF-OFCDM systems [10, 11]. The amount of time domain spreading can be varied by varying the allocated time domain OVSF code. This is in turn modifies the amount of frequency domain spreading, which is the number of orthogonal subcarriers used for frequency division multiplexing. Frequency domain spreading gives better BER performance when the number of users using the same time domain code is low. However, when the number of users using the same time domain code increases, intercode interference increases. In order to reduce the intercode interference, users are assigned a descendant code of the previous time domain code of higher spreading factor as the new time domain code. This reduces the number of users using the same time domain code at least by half and thus reduces the intercode interference. In this paper, we present how the presented fair code allocation scheme can be used in 4G VSF-OFCDM systems to pick an OVSF code that offers flexibility in time and frequency domain spreading.
The rest of the paper is organized as follows. Section 2 presents the related work. Section 3 describes the system model. Section 4 presents the CFCA protocol, including the algorithms CBP, CBR, and DBA, along with the CRD metric, and the concept of  -hop affinity-mate. Section 5 presents how the CFCA protocol can be used in VSF-OFCDM systems. Section 6 presents a performance analysis of the CFCA protocol. Simulation results are discussed in Section 7, and the concluding remarks are made in Section 8.
-hop affinity-mate. Section 5 presents how the CFCA protocol can be used in VSF-OFCDM systems. Section 6 presents a performance analysis of the CFCA protocol. Simulation results are discussed in Section 7, and the concluding remarks are made in Section 8.
2. Related Work
Code placement schemes [2, 12–25] assign codes to new and handoff calls in such a way that the probability of call blocking is reduced when code reassignments are not allowed in the system. When code reassignments are allowed in the system, the objective of code replacement schemes [26, 27] is to reduce the number of code reassignments by freeing blocked codes. Existing code placement and replacement algorithms do not consider the impact of the code placement on dynamic bandwidth allocation. They focus only on keeping the code tree as compact as possible so that the number of reassignments that could be needed when a new call arrives is reduced. This is not sufficient, however, for dynamic bandwidth allocation in which the codes of the existing flows may need to be changed because of their poor channel conditions and delay requirements. Therefore, our code placement (CBP) and code reassignment (CBR) algorithms allocate codes to flows by considering the possibility of assigning higher rate codes to the flows when channel conditions are poor or the flows have difficulties in meeting their delay requirements. That is, when CBP or CBR assigns a code to a flow, it ensures that the flow could be reassigned a higher-rate code with a low cost of signaling overhead.
Dynamic bandwidth allocation to support the QoS and fairness in WCDMA wireless cellular networks is studied in [3, 28–34]. Most of the existing bandwidth allocation algorithms ignore the signaling overhead in dynamic bandwidth allocation. In [3, 34], some methods for reducing the signaling overhead are discussed, though the methods in [3] consider the multicode model. In addition, only bursty traffic is considered in [34]. But, when real-time traffic is continuous and non-real-time traffic is bursty, an idle non-real-time flow can accumulate credits and subsequently can receive a higher priority in scheduling. This can affect adversely the rate allocated to continuous real-time traffic, which may result in higher delay for real-time packets. However, this paper considers fairness and QoS guarantees for admitted calls of both continuous and bursty real-time and non-real-time traffic. In [33], a joint power and rate adaptation scheme is presented to meet the QoS requirements of traffic belonging to various traffic classes. In [30], a credit-based bandwidth allocation scheme to ensure fairness and minimum rate guarantees under varying channel conditions is presented. In [31], a threshold-based scheme is described to dynamically change the code assigned to a call so that the delay performance of the high QoS traffic is improved. In [32], a packet scheduling scheme for continuously backlogged traffic is presented. However, in [28, 30–33], only a general bandwidth allocation problem is addressed without addressing code allocation and signaling overhead during dynamic bandwidth allocation. Signaling overhead is the number of bits of control information required to inform the receivers of the mobile stations about the OVSF codes assigned to them during dynamic bandwidth allocation.
In [12–15], the authors address the code assignment and reassignment problem so that the overhead of code reassignments is reduced while admitting a new or a hand-off call. However, they do not consider the impact of code placement and replacement on dynamic bandwidth allocation. Dynamic bandwidth allocation addresses the code assignment problem every time slot for existing calls so that their delay and rate requirements are met, as described in [3, 28, 34]. Hence, no existing work addresses code placement and replacement together with dynamic bandwidth allocation for OVSF-CDMA-based systems. In addition, in 3G networks, the assignment of bandwidth (or code) and power to a non-real-time flow would affect and constrain the power and bandwidth that can be assigned to a real-time flow during dynamic bandwidth allocation. As stated in [34, 35], although non-real-time flows do not have a strict delay bound, it is not desirable either to have too long service times for them. Service providers should provide "enough" bandwidth for all users, leading to more subscribers it can serve, and more revenue they can earn. Therefore, it is necessary to consider the scheduling of non-real-time traffic along with real-time traffic so that non-real-time flows do not get starved for extended periods of time. This paper proposes the CFCA protocol to address all these issues together in WCDMA networks.
3. System Model
We consider  flows (or calls),
flows (or calls),  , within a single cell of a WCDMA-based cellular network, where the terms "flow" and "call" are used interchangeably to mean a stream of packets. Any call that is admitted into the system is referred to as a new call regardless of whether it is a hand-off call or is initiated in the current cell. The flows transmit data through wireless channels separated by OVSF codes. Each downlink channel is time slotted such that each time slot is equal to a 10-millisecond WCDMA frame. Control signals such as the transmit power control and rate information are time-multiplexed with the user data in each time slot. We use the control header to transmit the identity of the assigned OVSF code. The code allocations and reassignments are done by a dynamic bandwidth scheduler, based on the power and code resources, the number of traffic flows, and the feedback about the quality of the channels.
, within a single cell of a WCDMA-based cellular network, where the terms "flow" and "call" are used interchangeably to mean a stream of packets. Any call that is admitted into the system is referred to as a new call regardless of whether it is a hand-off call or is initiated in the current cell. The flows transmit data through wireless channels separated by OVSF codes. Each downlink channel is time slotted such that each time slot is equal to a 10-millisecond WCDMA frame. Control signals such as the transmit power control and rate information are time-multiplexed with the user data in each time slot. We use the control header to transmit the identity of the assigned OVSF code. The code allocations and reassignments are done by a dynamic bandwidth scheduler, based on the power and code resources, the number of traffic flows, and the feedback about the quality of the channels.
We are interested in the downlink control of transmissions in such a way that the flows meet fairly the delay and rate requirements. To achieve this, the rate allocated to a mobile station is dynamically varied by adjusting the spreading factor of the assigned OVSF code [36]. To ensure successful reception of the packetized data at a mobile station (MS), there is a limit on the achieved bit error rate (BER). Depending on the spreading factor, modulation and coding scheme used, a target  should be achieved at the MS so that the limit on BER is not exceeded.
should be achieved at the MS so that the limit on BER is not exceeded.  represents the ratio of energy-per-bit (
represents the ratio of energy-per-bit ( ) to interference power spectral density (
) to interference power spectral density ( ). Based on the channel state feedback received from the MS and the spreading factor used, the BS adjusts the power, modulation and coding used for a flow to meet the target
). Based on the channel state feedback received from the MS and the spreading factor used, the BS adjusts the power, modulation and coding used for a flow to meet the target  . But, in order not to introduce any additional intercell interference to other cells, the total power at the BS is constrained. As a result, the power requirements of all the flows may not be met at some instances. In this case, flows are served in their priority order as long as the total transmit power constraint of the BS is not violated.
. But, in order not to introduce any additional intercell interference to other cells, the total power at the BS is constrained. As a result, the power requirements of all the flows may not be met at some instances. In this case, flows are served in their priority order as long as the total transmit power constraint of the BS is not violated.
The third generation (3G) universal mobile telecommunications system (UMTS) describes four traffic types (or QoS classes), namely, conversational (e.g., voice), streaming (e.g., streaming video), interactive (e.g., web browsing) and background (e.g., email). In the proposed code placement and replacement algorithms, the conversational and streaming classes are referred to as the real-time (RT) class and interactive and background classes are referred to as the non-real-time (NRT) class. The four traffic classes of WCDMA are distinguished by the proposed dynamic bandwidth allocation algorithm according to their priorities; that is, conversational traffic is considered first, then streaming, followed by interactive and background traffic classes.
For simplicity, we assume a two-state channel model, according to which the channel can be either in normal state or poor state. Under normal channel conditions, the flow can achieve a data rate equal to its average requested data rate using the OVSF code assigned to it at admission. Under poor channel conditions, a flow still receives data with the same power of transmission, but at a lower rate because of the use of a lower modulation level and lower coding rate. To achieve the average data rate, we assign a higher rate (lower SF) code for real-time flows under poor channel conditions. As shown in [37], for higher spreading factors (SF ≥ 32), the additional power needed to achieve the same BER while moving from  to
to  is of the order of 0.5 dB. The admission control scheme presented in Section 4 ensures that this additional power is always available for all admitted real-time flows under poor channel conditions. It should be noted that the additional power needed to achieve the same BER without changing the SF, modulation and coding scheme is relatively high and is of the order of 3 dB as shown in [38].
is of the order of 0.5 dB. The admission control scheme presented in Section 4 ensures that this additional power is always available for all admitted real-time flows under poor channel conditions. It should be noted that the additional power needed to achieve the same BER without changing the SF, modulation and coding scheme is relatively high and is of the order of 3 dB as shown in [38].
We use a simplified  model as the channel model. In a WCDMA network, the
model as the channel model. In a WCDMA network, the  achieved at the mobile
achieved at the mobile  is expressed as
is expressed as


where  is the
is the  requirement of
requirement of  th flow assuming a spreading factor of
th flow assuming a spreading factor of  and modulation and coding scheme
and modulation and coding scheme  ,
,  is the instantaneous power allocated to flow
is the instantaneous power allocated to flow  by base station
by base station  at time
at time  ,
,  is the instantaneous data rate allocated to flow
is the instantaneous data rate allocated to flow  at time
at time  ,
,  is the power loss on the path from base station
is the power loss on the path from base station  to mobile
to mobile  at time
at time  ,
,  is the total power budget of the base station on the downlink,
is the total power budget of the base station on the downlink,  is the instantaneous transmit power of the base station on the downlink for all existing flows at time
is the instantaneous transmit power of the base station on the downlink for all existing flows at time  ,
,  is the noise power spectral density,
is the noise power spectral density,  is the intercell interference at mobile
is the intercell interference at mobile  at time
at time  ,
,  is the chip rate,
is the chip rate,  is the own-cell orthogonality factor (typically ranges between 0.4 and 0.9), and
is the own-cell orthogonality factor (typically ranges between 0.4 and 0.9), and  is the spreading factor of the code assigned to flow
is the spreading factor of the code assigned to flow  at time
at time  .
.  is the product of distance-based path loss, slow fading (shadowing), and fast fading (multipath) on the wireless channel from BS
is the product of distance-based path loss, slow fading (shadowing), and fast fading (multipath) on the wireless channel from BS  to MS
to MS  . Path loss
. Path loss  is computed as a function of distance
is computed as a function of distance  as given in (4), where
as given in (4), where  is the path loss exponent. Slow fading,
is the path loss exponent. Slow fading,  is considered to be log-normally distributed around the distance-based path loss
is considered to be log-normally distributed around the distance-based path loss  with zero mean and standard deviation. Fast fading,
with zero mean and standard deviation. Fast fading,  is generated using a Rayleigh fading distribution with zero mean and standard deviation. Hence,
is generated using a Rayleigh fading distribution with zero mean and standard deviation. Hence,  and
and  can be written as
can be written as


4. Class-Based Fair Code Allocation (CFCA) Protocol
This section presents our class-based fair code allocation (CFCA) protocol to assign the appropriate OVSF codes to the traffic flows based on their delay and data rate requirements, channel conditions, and fairness. The objectives of the CFCA are as follows: (i) to assign bandwidth fairly to real-time flows so that their rate and delay requirements are met, (ii) to assign fairly the residual bandwidth among non-real-time flows, and (iii) to reduce the overhead for code reassignments in dynamic bandwidth allocation. CFCA uses three main algorithms, and the list of notations used by these algorithms is shown in Table 1.
CFCA admits a new real-time call to the network if the total network capacity and base station power budget is always capable of supporting all the existing real-time flows under poor channel conditions at which they need higher rate codes. Therefore, there is a constraint on the number of admitted real-time flows to help meet the delay guarantees of real-time flows in the presence of poor channel conditions. It should be noted that a poor channel condition implies a channel state at which a mobile station is still able to receive data with the same power of transmission, but at a lower rate because of the use of lower modulation level and lower coding rate. The acceptable poor channel condition at any location in a coverage area is determined by the cellular service providers by considering path loss, fading, and worst case inter- and intracell interference. Service providers can then use the acceptable poor channel condition as a constraint in determining the optimal locations of base stations in a given coverage area. For example, in [39, 40], the authors propose optimization models for base station locations considering the signal-to-noise ratio as the quality measure. In [41], the authors propose models for base station location so that the quality of service constraints is satisfied. Once a service provider plans his network for a given poor channel condition, the aim of the CFCA protocol is to provide QoS guarantees to those real-time flows that can at least maintain this poor channel condition by just making use of the power and code resources used to determine their admission.
When a flow  is admitted, there are two bandwidth requirements for flow
is admitted, there are two bandwidth requirements for flow  :
:  and
and  .
.  is the bandwidth needed for flow
is the bandwidth needed for flow  under normal channel conditions, whereas
under normal channel conditions, whereas  is the bandwidth needed for flow
is the bandwidth needed for flow  under poor channel conditions.
under poor channel conditions.  represents the spreading factor (SF) required to meet at least the average data rate of flow
represents the spreading factor (SF) required to meet at least the average data rate of flow  under normal channel conditions at which a high-order modulation and coding scheme is used.
under normal channel conditions at which a high-order modulation and coding scheme is used.  represents the spreading factor (SF) required to meet the average data rate of flow
represents the spreading factor (SF) required to meet the average data rate of flow  under poor channel conditions at which a lower-order modulation and coding scheme is used.
under poor channel conditions at which a lower-order modulation and coding scheme is used.  is greater than
is greater than  and, therefore,
and, therefore,  requires a higher-rate code (code of lower SF) than the code needed by
requires a higher-rate code (code of lower SF) than the code needed by  . The total bandwidth needed by all real-time flows under poor channel conditions cannot exceed the total network capacity. Thus, a new real-time call
. The total bandwidth needed by all real-time flows under poor channel conditions cannot exceed the total network capacity. Thus, a new real-time call  is admitted if (5) holds:
is admitted if (5) holds:

where  are the existing real-time flows, and
are the existing real-time flows, and  is the SF required to meet the data rate of flow
is the SF required to meet the data rate of flow  under poor channel conditions for
under poor channel conditions for  . As for the non-real-time flows, CFCA admits a new non-real-time flow if the total bandwidth requirements of all existing real-time and non-real-time flows under normal channel conditions are less than the total network capacity. Assuming that
. As for the non-real-time flows, CFCA admits a new non-real-time flow if the total bandwidth requirements of all existing real-time and non-real-time flows under normal channel conditions are less than the total network capacity. Assuming that  is the number of all existing flows (real-time and non-real-time) in the network, a new non-real-time flow
is the number of all existing flows (real-time and non-real-time) in the network, a new non-real-time flow  is admitted if (6) holds:
is admitted if (6) holds:

where  is the SF required to meet the data rate of flow
is the SF required to meet the data rate of flow  under normal channel conditions. This paper assumes that a higher-level modulation and a higher-rate coding scheme are used under normal channel conditions. When channel conditions become poor, both modulation level and coding rate are reduced [42]. For instance, under normal channel conditions, let us assume that the modulation level is 8 (64 QAM) and coding rate is 1/2. When the channel conditions become poor, the modulation level can be lowered to 4 (16 QAM) or 2 (QAM), while the coding rate could be reduced from 1/2 to 1/3 to meet the required
under normal channel conditions. This paper assumes that a higher-level modulation and a higher-rate coding scheme are used under normal channel conditions. When channel conditions become poor, both modulation level and coding rate are reduced [42]. For instance, under normal channel conditions, let us assume that the modulation level is 8 (64 QAM) and coding rate is 1/2. When the channel conditions become poor, the modulation level can be lowered to 4 (16 QAM) or 2 (QAM), while the coding rate could be reduced from 1/2 to 1/3 to meet the required  . To compensate for the loss in data rate under poor channel conditions, we assign a higher rate code of lower SF that will run with lower modulation level and coding rate. In [42], the authors show how the achieved data rate can be modified by changing the modulation and coding scheme.
. To compensate for the loss in data rate under poor channel conditions, we assign a higher rate code of lower SF that will run with lower modulation level and coding rate. In [42], the authors show how the achieved data rate can be modified by changing the modulation and coding scheme.
Therefore, to ensure the availability of a higher rate code of lower SF for real-time flows under poor channel conditions, the following equations should also hold before admitting a new real-time flow. In these equations, we consider only the power required to use a higher rate code of spreading factor  instead of the normal rate code of spreading factor
instead of the normal rate code of spreading factor  . The additional power needed to use a higher rate code is constant and depends only on the amount of reduction in the SF and does not depend on the channel conditions. Based on the analysis in [43], we can first express (2) as an inequality:
. The additional power needed to use a higher rate code is constant and depends only on the amount of reduction in the SF and does not depend on the channel conditions. Based on the analysis in [43], we can first express (2) as an inequality:

Since this equation is evaluated only at the time of admission for each flow, we can eliminate  as a parameter and replace
as a parameter and replace  with
with  to represent the sum of transmit power assigned to all real-time flows at admission. Equation (7) implies that
to represent the sum of transmit power assigned to all real-time flows at admission. Equation (7) implies that



where  is the power requirement of flow
is the power requirement of flow  under poor channel conditions when an SF of
under poor channel conditions when an SF of  is used. Before the base station admits a new real-time flow
is used. Before the base station admits a new real-time flow  , the base station first ensures that the sum of
, the base station first ensures that the sum of  ,
,  of existing real-time flows and
of existing real-time flows and  of the new flow does not exceed
of the new flow does not exceed  shown in (10).
shown in (10).
From (9) and (10), it follows that


Since  is a positive quantity, the following feasibility constraint should be met:
is a positive quantity, the following feasibility constraint should be met:

A real-time flow  is admitted only if (5), (9), and (10) together hold. Similarly, a new non-real-time flow
is admitted only if (5), (9), and (10) together hold. Similarly, a new non-real-time flow  is admitted only if the following (14) and (15) hold along with (6):
is admitted only if the following (14) and (15) hold along with (6):


where  are the existing real-time and non-real-time flows,
are the existing real-time and non-real-time flows,  is the SF required to meet the data rate of flow
is the SF required to meet the data rate of flow  under normal channel conditions for
under normal channel conditions for  ,
,  is the power requirement of flow
is the power requirement of flow  under normal channel conditions, and
under normal channel conditions, and  is the sum of transmit power assigned to all flows at admission.
is the sum of transmit power assigned to all flows at admission.
CFCA is implemented in four steps as shown in Table 2. In Step 1 of CFCA, the SF of a new call is determined. A real-time call is admitted depending on whether (5), (9), and (10) hold or not. Similarly, a non-real-time call is admitted depending on whether (6), (14), and (15) hold or not. It should be noted that the SF required under poor channel conditions ( ) is only used to determine the admissibility of a real-time call in Step 1 of the CFCA protocol using (5). Once it has been determined that enough code resources meet the rate requirements of a real-time call even under poor channel conditions, only a code whose SF is equal to that required under normal channel conditions (
) is only used to determine the admissibility of a real-time call in Step 1 of the CFCA protocol using (5). Once it has been determined that enough code resources meet the rate requirements of a real-time call even under poor channel conditions, only a code whose SF is equal to that required under normal channel conditions ( ) is assigned to a real-time call. During the life time of a call, if the channel conditions become poor, then a higher rate (of lower SF
) is assigned to a real-time call. During the life time of a call, if the channel conditions become poor, then a higher rate (of lower SF  ) code is assigned to meet the delay requirements of a real-time call. In the second step of CFCA, if a free code of the required spreading factor is not available even though the system has enough capacity to support the new call, algorithm CBR is invoked to free a code of the required spreading factor. The code that is made free is then assigned to the new call. In the third step, when a new call arrives, it is assigned an OVSF code of the required spreading factor using the CBP algorithm. In the fourth step, the call can use its initial code that is assigned by the CBP and CBR algorithms or a higher-rate code, and this decision is made every time slot by the DBA algorithm. When a higher-rate code is used, the mobile station is informed about the higher-rate code using control channel signaling. We use in-band control channel signaling mode [26], the control header is decoded by the mobile station using the initially assigned code. If the control header has control information suggesting the use of a different higher-rate code to decode the data segment, the data segment is decoded using the higher rate code. In the next frame, the control header is again decoded using the initially assigned code and the process continues. The CFCA protocol uses the concept of
) code is assigned to meet the delay requirements of a real-time call. In the second step of CFCA, if a free code of the required spreading factor is not available even though the system has enough capacity to support the new call, algorithm CBR is invoked to free a code of the required spreading factor. The code that is made free is then assigned to the new call. In the third step, when a new call arrives, it is assigned an OVSF code of the required spreading factor using the CBP algorithm. In the fourth step, the call can use its initial code that is assigned by the CBP and CBR algorithms or a higher-rate code, and this decision is made every time slot by the DBA algorithm. When a higher-rate code is used, the mobile station is informed about the higher-rate code using control channel signaling. We use in-band control channel signaling mode [26], the control header is decoded by the mobile station using the initially assigned code. If the control header has control information suggesting the use of a different higher-rate code to decode the data segment, the data segment is decoded using the higher rate code. In the next frame, the control header is again decoded using the initially assigned code and the process continues. The CFCA protocol uses the concept of  -hop affinity-mate to keep the control channel signaling overhead low when higher rate codes are assigned to calls.
-hop affinity-mate to keep the control channel signaling overhead low when higher rate codes are assigned to calls.
Before presenting the algorithms CBP, CBR, and DBA, we now introduce the definitions for CRD and  -hop affinity-mate next. We consider the last
-hop affinity-mate next. We consider the last  time slots of flow
time slots of flow  , each of which corresponds to a frame transmission time. We assume that
, each of which corresponds to a frame transmission time. We assume that  time slots constitute a window, so that
time slots constitute a window, so that  time slots have
time slots have  windows. Let
windows. Let  denote the average rate that flow
denote the average rate that flow  receives over a window, while
receives over a window, while  denotes the requested average rate. The value of
denotes the requested average rate. The value of  depends on the modulation and coding scheme used. For example, for a symbol rate of 100 symbols per second, QPSK modulation scheme (BPS = 2) and 1/2 convolutional coding (CR = 1/2) give an information bit rate of 100 bits per second. On the other hand 64-QAM modulation scheme (BPS = 6) and 3/4 turbo coding (CR = 3/4) give an information bit rate of 450 bits.
depends on the modulation and coding scheme used. For example, for a symbol rate of 100 symbols per second, QPSK modulation scheme (BPS = 2) and 1/2 convolutional coding (CR = 1/2) give an information bit rate of 100 bits per second. On the other hand 64-QAM modulation scheme (BPS = 6) and 3/4 turbo coding (CR = 3/4) give an information bit rate of 450 bits.
Definition 1 (class-based rate degradation (CRD)).
 represents the average rate degradation for which flow
represents the average rate degradation for which flow  experiences over the last
experiences over the last  time slots consisting of
time slots consisting of  windows during which it receives less rate than the requested average data rate
windows during which it receives less rate than the requested average data rate  .
.  is expressed as
is expressed as

 (i.e., CRD of flow
(i.e., CRD of flow  ) basically refers to the ratio of (
) basically refers to the ratio of ( ) to
) to  over
over  windows, when
windows, when  . The value of
. The value of  is the same for all types of flows, whereas the window size
is the same for all types of flows, whereas the window size  gets larger as the class priority of flows decreases. The value of
gets larger as the class priority of flows decreases. The value of  depends on the minimum time interval during which average rate requirements of non-real-time flows must be met. On the other hand,
depends on the minimum time interval during which average rate requirements of non-real-time flows must be met. On the other hand,  is determined based on the delay requirements of
is determined based on the delay requirements of  to indicate the number of consecutive time slots that flow
to indicate the number of consecutive time slots that flow  can tolerate its data rate to be lower than average data rate. In Figure 2, the value of
can tolerate its data rate to be lower than average data rate. In Figure 2, the value of  is chosen as 20 because it is the minimum time interval during which the average rate requirement of the non-real-time flow must be met. The
is chosen as 20 because it is the minimum time interval during which the average rate requirement of the non-real-time flow must be met. The  time slots consist of
time slots consist of  distinct windows, each having
distinct windows, each having  time slots.
time slots.  is computed as follows: (a) for each window
is computed as follows: (a) for each window  from
from  = 1 to
= 1 to  , compute the average
, compute the average  for all rates
for all rates  over
over  time slots, where
time slots, where  refers to the received data rate at time slot
refers to the received data rate at time slot  , (b) determine the minimum of
, (b) determine the minimum of  and
and  to find out whether
to find out whether  is below the requested average rate
is below the requested average rate  , (c) compute the window rate degradation, denoted by
, (c) compute the window rate degradation, denoted by  , for window
, for window  by subtracting the minimum of
by subtracting the minimum of  and
and  from
from  and then by dividing the resultant by
and then by dividing the resultant by  (i.e.,
(i.e.,  ), and (d) finally find the average of all
), and (d) finally find the average of all  windows' degradations and then call it
windows' degradations and then call it  . At a given time slot,
. At a given time slot,  is determined based on the received rates of the flow at the last
is determined based on the received rates of the flow at the last  time slots. The window sizes of all the flows in a traffic class are the same, and depend on the priority of their traffic class in the sense that a higher priority traffic class has a lower-size window. That is, if
time slots. The window sizes of all the flows in a traffic class are the same, and depend on the priority of their traffic class in the sense that a higher priority traffic class has a lower-size window. That is, if  ,
,  ,
,  , and
, and  denote the window sizes of the conversational, streaming, interactive, and background traffic classes, respectively, then it follows that:
denote the window sizes of the conversational, streaming, interactive, and background traffic classes, respectively, then it follows that:  . Figure 2 shows how
. Figure 2 shows how  is computed. Note that
is computed. Note that  is computed by (16) in a sliding window manner with a period of
is computed by (16) in a sliding window manner with a period of  time slots. This implies that, for flow
time slots. This implies that, for flow  ,
,  is computed after every
is computed after every  time slot. CRD is somewhat similar to Degradation Ratio (DR) in [44] that determines whether a new call can be admitted by degrading the rates of existing flows.
time slot. CRD is somewhat similar to Degradation Ratio (DR) in [44] that determines whether a new call can be admitted by degrading the rates of existing flows.
The data rates of a flow that are achieved within 20 time slots are the average data rate  in slot 1, the data rate
in slot 1, the data rate  in slots 2 to 6, no data transmission in slots 7 to 8, and the average rate
in slots 2 to 6, no data transmission in slots 7 to 8, and the average rate  or more in slots 9 to 20. (a) If the flow is a real-time (RT) flow with a window size of
or more in slots 9 to 20. (a) If the flow is a real-time (RT) flow with a window size of  over
over  time slots, then
time slots, then  is the average of the window rate degradations
is the average of the window rate degradations  ,
,  ,
,  , and
, and  . That is,
. That is,  is
is  . (b) If the flow is a non-real-time (NRT) flow with a window size of
. (b) If the flow is a non-real-time (NRT) flow with a window size of  over
over  time slots, then CRD equals zero.
time slots, then CRD equals zero.
This paper uses CRD to support delay requirements of real-time traffic by ensuring that the average requested rate is met at variable window sizes of frames. That is, if a flow is more delay sensitive, then the window size during which the requested average rate should be met is made smaller in the computation of CRD. In order to determine whether a flow meets the delay and rate requirements, we employ CRD for all flows and traffic types as described earlier. The value of  for flow
for flow  ranges from 0 to 1 to indicate "no degradation" and "maximum degradation", respectively. Specifically, if
ranges from 0 to 1 to indicate "no degradation" and "maximum degradation", respectively. Specifically, if  equals zero, then flow
equals zero, then flow  meets its both delay and rate requirements. However, if
meets its both delay and rate requirements. However, if  is greater than zero, it indicates that flow
is greater than zero, it indicates that flow  has experienced a degradation in rate and delay requirements, and the
has experienced a degradation in rate and delay requirements, and the  value represents the amount of degradation. In [44] the objective of the degradation metric is to intentionally degrade the QoS of existing flows in order to admit new flows. However, the objective of this paper is to support the rate and delay guarantees by keeping the degradations at a low value.
value represents the amount of degradation. In [44] the objective of the degradation metric is to intentionally degrade the QoS of existing flows in order to admit new flows. However, the objective of this paper is to support the rate and delay guarantees by keeping the degradations at a low value.
The authors in [3, 34] present scheduling algorithms to dynamically assign OVSF codes to mobile users on a timeslot-by-timeslot basis based on a credit-based mechanism. A credit-based mechanism assigns credits to a flow every time slot based on its requested average rate and deletes credits from a flow every time slot based on the rate allocated to that flow. Flows with higher credits have higher priority in scheduling and code allocation. The algorithms provide average data rate guarantee for bursty data traffic. Though the algorithms can be used for real-time traffic, it is more appropriate for non-real-time traffic because of the following issue. When there exist more than one flow with the same traffic type, these flows are scheduled based on their CRD values such that the flow with the highest CRD value is scheduled first to prevent it from having further degradation. In addition, to help reduce the degradation of a flow with high CRD value, our algorithm DBA attempts to increase the data rate of the flow above the requested average rate to meet the delay requirements. Increasing the rate requires the assignment of a higher rate code. The CFCA protocol uses the concept of  -hop affinity-mate whose definition is presented next, to keep the overhead during the assignment of higher-rate code low.
-hop affinity-mate whose definition is presented next, to keep the overhead during the assignment of higher-rate code low.
Definition 2 ( -hop affinity-mate).
-hop affinity-mate).
Two OVSF codes are referred to as  -hop affinity-mates if one of the following two conditions holds: (i) their nearest ancestor has the distance of exactly
-hop affinity-mates if one of the following two conditions holds: (i) their nearest ancestor has the distance of exactly  hops to one of them and the distance of at most
hops to one of them and the distance of at most  hops to the other one, or (ii) one of the codes is the ancestor of the other one and the distance between them equals
hops to the other one, or (ii) one of the codes is the ancestor of the other one and the distance between them equals  hops, where a hop corresponds to an edge in the OVSF code tree.
hops, where a hop corresponds to an edge in the OVSF code tree.
The first part of the definition basically says that two codes are  -hop affinity-mates only if none of the two codes is at a distance greater than
-hop affinity-mates only if none of the two codes is at a distance greater than  hops from their common ancestor and at least one of the two codes is at a distance of
hops from their common ancestor and at least one of the two codes is at a distance of  hops from their common ancestor. Table 3 shows a table for the 1-hop, 2-hop, and 3-hop affinity-mates of all the codes in the code tree illustrated in Figure 1. Because the lowest SF in WCDMA is 4, the codes
hops from their common ancestor. Table 3 shows a table for the 1-hop, 2-hop, and 3-hop affinity-mates of all the codes in the code tree illustrated in Figure 1. Because the lowest SF in WCDMA is 4, the codes  ,
,  , and
, and  are not included in the table. In determining the code to be assigned to a new call, the CBP algorithm in Step 3 of the CFCA protocol chooses the code that has the best
are not included in the table. In determining the code to be assigned to a new call, the CBP algorithm in Step 3 of the CFCA protocol chooses the code that has the best  -hop affinity-mate of
-hop affinity-mate of  times higher rate. If more than one free code with the best 1-hop affinity-mate is available, CBP attempts to find a code with the best 2-hop affinity-mate and so on until
times higher rate. If more than one free code with the best 1-hop affinity-mate is available, CBP attempts to find a code with the best 2-hop affinity-mate and so on until  -hops. The determination of the best
-hops. The determination of the best  -hop affinity-mate is explained in the next section.
-hop affinity-mate is explained in the next section.
 -hop affinity-mates and data rates of some codes shown in Figure 1, for
-hop affinity-mates and data rates of some codes shown in Figure 1, for  , where
, where  represents the data rate of any code with SF = 8. The affinity-mates of any other code can be determined similarly. This table is stored at the base station for determining the affinity-mate codes faster.
represents the data rate of any code with SF = 8. The affinity-mates of any other code can be determined similarly. This table is stored at the base station for determining the affinity-mate codes faster.4.1. Class-Based Code Placement (CBP) Algorithm
When a new call arrives, there may be more than one free code that could be assigned to the call. To choose the free code that can cause the minimal overhead of code reassignments in case of poor channel conditions, we introduce the concept of weight for free codes as follows. For a new call of traffic type  , a free code
, a free code  with
with  and rate
and rate  , and its
, and its  -hop affinity-mate code with the data rate of
-hop affinity-mate code with the data rate of  , the weight
, the weight  of the code
of the code  is determined by a number
is determined by a number  depending on the traffic type
depending on the traffic type  and the status (e.g., free, busy with a real-time call, or busy with a non-real-time call) of the
and the status (e.g., free, busy with a real-time call, or busy with a non-real-time call) of the  -hop affinity-mate code, for
-hop affinity-mate code, for  and
and  . When the new call is a real-time call, the most desirable free code is the one whose
. When the new call is a real-time call, the most desirable free code is the one whose  -hop affinity-mate code is free (lines 9-10), so that the call may be reassigned easily the free affinity-mate code of higher rate to meet its delay and rate requirements. The second most desirable free code is the one whose affinity-mate code is currently being used by a non-real-time call (lines 7-8) because the real-time call may be assigned the affinity-mate of higher rate that is currently being used by a non-real-time call when the real-time call requires a higher data rate. When the new call is a non-real-time call, the most desirable free code is again the one whose affinity-mate code is free (lines 17-18) because the call may be assigned the higher rate affinity-mate to increase its rate. But, the second most desirable free code is the one whose affinity-mate code is currently being used by a real-time call (lines 15-16) because the real-time call can use the codes assigned to this non-real-time call to improve its rate. If there are more than one free code with the same highest weight, the code with the smallest index
-hop affinity-mate code is free (lines 9-10), so that the call may be reassigned easily the free affinity-mate code of higher rate to meet its delay and rate requirements. The second most desirable free code is the one whose affinity-mate code is currently being used by a non-real-time call (lines 7-8) because the real-time call may be assigned the affinity-mate of higher rate that is currently being used by a non-real-time call when the real-time call requires a higher data rate. When the new call is a non-real-time call, the most desirable free code is again the one whose affinity-mate code is free (lines 17-18) because the call may be assigned the higher rate affinity-mate to increase its rate. But, the second most desirable free code is the one whose affinity-mate code is currently being used by a real-time call (lines 15-16) because the real-time call can use the codes assigned to this non-real-time call to improve its rate. If there are more than one free code with the same highest weight, the code with the smallest index  is chosen. Any further ties are broken randomly.
is chosen. Any further ties are broken randomly.
Example 1.
In Figure 3(a), an OVSF code subtree is shown such that the code  refers to an OVSF code with
refers to an OVSF code with  and the data rate of
and the data rate of  , for
, for  . Let
. Let  ,
,  , and
, and  . The OVSF code subtree is assumed to have initially a single RT call, namely, Call 1, that is assigned code
. The OVSF code subtree is assumed to have initially a single RT call, namely, Call 1, that is assigned code  . When a new NRT call, namely, Call 2, requiring a code with
. When a new NRT call, namely, Call 2, requiring a code with  is admitted to the network, there are three free codes with SF = 4:
is admitted to the network, there are three free codes with SF = 4:  ,
,  , and
, and  . Algorithm CBP determines the weights
. Algorithm CBP determines the weights  (lines 12–20) of the three free codes as 2, 3, and 3, respectively. Because the free codes
(lines 12–20) of the three free codes as 2, 3, and 3, respectively. Because the free codes  and
and  have the same weight
have the same weight  , we need to determine their
, we need to determine their  values to try to choose a code with a higher weight. But, their
values to try to choose a code with a higher weight. But, their  values happen to be the same as well and, therefore, CBP chooses
values happen to be the same as well and, therefore, CBP chooses  randomly to break the tie (line 23). Now, a new RT call (Call 3) requiring an SF = 8 is admitted to the network. There are five free codes,
randomly to break the tie (line 23). Now, a new RT call (Call 3) requiring an SF = 8 is admitted to the network. There are five free codes,  to
to  . Algorithm CBP determines the weights
. Algorithm CBP determines the weights  (lines 4–11) of the five free codes as 1, 3, 3, 3, and 3, respectively. CBP computes the
(lines 4–11) of the five free codes as 1, 3, 3, 3, and 3, respectively. CBP computes the  values of codes
values of codes  to
to  as 1, 1, 2, and 2, respectively, and then chooses one of
as 1, 1, 2, and 2, respectively, and then chooses one of  and
and  randomly (line 23). A new RT call (Call 4) requiring an
randomly (line 23). A new RT call (Call 4) requiring an  is assigned code
is assigned code  as it is the only code available with that SF. Now, a new RT call (Call 5) is assigned code
as it is the only code available with that SF. Now, a new RT call (Call 5) is assigned code  since it has a higher
since it has a higher  over the code
over the code  (note that
(note that  and
and  have the same value of
have the same value of  ). Figure 3(b) illustrates how dynamic code allocation can be implemented when Call 1 and Call 5 experience poor channel conditions. In this case, Call 1 and Call 5 are assigned the higher rate codes
). Figure 3(b) illustrates how dynamic code allocation can be implemented when Call 1 and Call 5 experience poor channel conditions. In this case, Call 1 and Call 5 are assigned the higher rate codes  and
and  , respectively, to compensate the data rate decline due to deteriorating channel conditions.
, respectively, to compensate the data rate decline due to deteriorating channel conditions.
An example for showing the operation of Algorithm CBP over an OVSF code subtree, where the code  refers to an OVSF code with
refers to an OVSF code with  and the data rate of
and the data rate of  , for
, for  . Let
. Let  ,
,  , and
, and  . (a) The OVSF code subtree is assumed to have initially a single real-time (RT) call, namely, Call 1, that is assigned code
. (a) The OVSF code subtree is assumed to have initially a single real-time (RT) call, namely, Call 1, that is assigned code  . When a new non-real-time (NRT) call, namely, Call 2, requiring a code with
. When a new non-real-time (NRT) call, namely, Call 2, requiring a code with  is admitted to the network, there are three free codes with
is admitted to the network, there are three free codes with  :
:  ,
,  , and
, and  . Algorithm CBP determines the weights
. Algorithm CBP determines the weights  (lines 12–20) of the three free codes as 2, 3, and 3, respectively. Because the free codes
(lines 12–20) of the three free codes as 2, 3, and 3, respectively. Because the free codes  and
and  have the same weight
have the same weight  , we need to determine their
, we need to determine their  values to try to choose a code with a higher weight. But, their
values to try to choose a code with a higher weight. But, their  values happen to be the same as well and, therefore, CBP chooses
values happen to be the same as well and, therefore, CBP chooses  randomly to break the tie (line 23). The initial assignments of codes to calls 3, 4, and 5 are done similarly. (b) When calls 1 and 5 experience poor channel conditions during dynamic bandwidth allocation, they are assigned the higher rate codes
randomly to break the tie (line 23). The initial assignments of codes to calls 3, 4, and 5 are done similarly. (b) When calls 1 and 5 experience poor channel conditions during dynamic bandwidth allocation, they are assigned the higher rate codes  , and
, and  , respectively, to compensate the data rate decline due to deteriorating channel conditions.
, respectively, to compensate the data rate decline due to deteriorating channel conditions.
4.2. Class-Based Code Reassignment (CBR) Algorithm
The objective of the CBR algorithm is to find and free the most desirable code (as mentioned in Section 4.1), when a new or existing call needs code reassignments. To achieve this, the CBR algorithm performs reassignments under three cases, namely, to assign code to a new call, a real-time call requesting a higher-rate code, and a non-real-time call to ensure fairness. Lines 1 to 4 handle the first case, where a new call requiring an SF of  requires code reassignments because of code blocking. On line 2, all blocked codes of required SF
requires code reassignments because of code blocking. On line 2, all blocked codes of required SF  are found. On line 3, the algorithm first finds all the codes of SF
are found. On line 3, the algorithm first finds all the codes of SF  that have the maximum weight
that have the maximum weight  as defined in the CBP algorithm. On line 4, the algorithm then finds the code
as defined in the CBP algorithm. On line 4, the algorithm then finds the code  that has the least number of descendant codes that are assigned to real-time calls. This leads the number of reassignments to be low for real-time calls. Lines 5 to 7 handle the second case, where a code for reassignment is chosen when a real-time call needs to increase its data rate and when none of its
that has the least number of descendant codes that are assigned to real-time calls. This leads the number of reassignments to be low for real-time calls. Lines 5 to 7 handle the second case, where a code for reassignment is chosen when a real-time call needs to increase its data rate and when none of its  -hop affinity-mate is available. In this case, a code that is assigned or blocked by only non-real-time calls is reassigned so that the other real-time calls are not affected by this reassignment. If there are more than one code available for reassignment, code
-hop affinity-mate is available. In this case, a code that is assigned or blocked by only non-real-time calls is reassigned so that the other real-time calls are not affected by this reassignment. If there are more than one code available for reassignment, code  that has the least number of descendant codes that are assigned to real-time calls is chosen for reassignment. Lines 8 to 10 handle the third case, where code reassignments are performed to ensure fairness in bandwidth allocation for non-real-time calls. In this case, a non-real-time call with a high CRD value is assigned the code of a non-real-time call with a low CRD value. The busy descendant codes of code
that has the least number of descendant codes that are assigned to real-time calls is chosen for reassignment. Lines 8 to 10 handle the third case, where code reassignments are performed to ensure fairness in bandwidth allocation for non-real-time calls. In this case, a non-real-time call with a high CRD value is assigned the code of a non-real-time call with a low CRD value. The busy descendant codes of code  are then freed by doing code reassignments on lines 12-13, and finally the code
are then freed by doing code reassignments on lines 12-13, and finally the code  is assigned to the incoming call on line 14. Figure 4 shows an example for the operation of Algorithm CBR.
is assigned to the incoming call on line 14. Figure 4 shows an example for the operation of Algorithm CBR.
An example for showing the operation of CBR Algorithm. (a) It is assumed that codes  ,
,  ,
,  , and
, and  are already assigned to the NRT, NRT, RT, and RT calls, respectively. When a new RT call arrives and requests an
are already assigned to the NRT, NRT, RT, and RT calls, respectively. When a new RT call arrives and requests an  , the NRT call assigned to code
, the NRT call assigned to code  is reassigned to code
is reassigned to code  as shown by arrow (i), and code
as shown by arrow (i), and code  can now be assigned to the new call (lines 1–4). (b) It is assumed that all codes except
can now be assigned to the new call (lines 1–4). (b) It is assumed that all codes except  are already assigned some RT and NRT calls, and that the call that is assigned
are already assigned some RT and NRT calls, and that the call that is assigned  needs a higher rate code to meet its delay requirements. Arrow (ii) shows that the RT call of code
needs a higher rate code to meet its delay requirements. Arrow (ii) shows that the RT call of code  is reassigned a new code
is reassigned a new code  (lines 5–7). NRT call assigned to code
(lines 5–7). NRT call assigned to code  will not receive any code assignment for the current frame. In case, an NRT flow assigned to code
will not receive any code assignment for the current frame. In case, an NRT flow assigned to code  requires a fair share of the bandwidth, reassignments are performed as shown by arrow (iii). The NRT call assigned to code
requires a fair share of the bandwidth, reassignments are performed as shown by arrow (iii). The NRT call assigned to code  is assigned the code
is assigned the code  assigned to another NRT call whose CRD value is low (lines 8–10).
assigned to another NRT call whose CRD value is low (lines 8–10).
4.3. Dynamic Bandwidth Allocation (DBA) Algorithm
Before describing the algorithm DBA, we first explain the CRD threshold for non-real-time flows. CRD threshold, denoted by  , refers to the maximum amount of rate degradation that a non-real-time flow can tolerate because of a real-time flow assigned to one of its
, refers to the maximum amount of rate degradation that a non-real-time flow can tolerate because of a real-time flow assigned to one of its  -hop affinity-mates. The DBA algorithm does not allow a non-real-time flow to use a code other than the
-hop affinity-mates. The DBA algorithm does not allow a non-real-time flow to use a code other than the  -hop affinity-mate codes if
-hop affinity-mate codes if  . However, if
. However, if  becomes greater than
becomes greater than  , any code can be assigned to a non-real-time flow to ensure a fairness bound in rate assignment.
, any code can be assigned to a non-real-time flow to ensure a fairness bound in rate assignment.
Lines 14 to 23 of the DBA algorithm assign codes to real-time flows by first considering conversational flows only and then streaming flows. On line 16, a real-time flow  with the highest CRD value is picked up. If
with the highest CRD value is picked up. If  of flow
of flow  is greater than zero, the flow is assigned a higher rate code by calling procedure
is greater than zero, the flow is assigned a higher rate code by calling procedure  . Thus, when the difference between the network capacity and the total aggregate capacity of the real-time flows is more than the new rate requirement of flow
. Thus, when the difference between the network capacity and the total aggregate capacity of the real-time flows is more than the new rate requirement of flow  , lines 17 and 18 of the algorithm ensure that the delay requirement of a flow is always met. Lines 24 to 32 of the algorithm assign codes to non-real-time flows. On line 26, if a non-real-time flow with a high CRD value has its CRD value greater than 0, and if its code
, lines 17 and 18 of the algorithm ensure that the delay requirement of a flow is always met. Lines 24 to 32 of the algorithm assign codes to non-real-time flows. On line 26, if a non-real-time flow with a high CRD value has its CRD value greater than 0, and if its code  is not available due to its assignment to a real-time flow, procedure
is not available due to its assignment to a real-time flow, procedure  (see Algorithm 4) is called to improve the CRD value of the flow. This step ensures fairness among non-real-time flows. The basic idea behind procedure
(see Algorithm 4) is called to improve the CRD value of the flow. This step ensures fairness among non-real-time flows. The basic idea behind procedure  is to first increase rate of the flow by assigning a higher-rate affinity-mate code (lines 1 to 5) and then to assign a higher rate non-affinity-mate code if an affinity-mate code is not available (6 to 14).
is to first increase rate of the flow by assigning a higher-rate affinity-mate code (lines 1 to 5) and then to assign a higher rate non-affinity-mate code if an affinity-mate code is not available (6 to 14).
Algorithm 4: Procedure ASSIGN_HRC.
Procedure ASSIGN_HRC( ,
,  ,
,  )
)
Input: A flow  with
with  and
and  . The
. The  -hop affinity-mate codes of
-hop affinity-mate codes of  are known for
are known for
 . The CRD threshold for non-real-time traffic is denoted by CRDth.
. The CRD threshold for non-real-time traffic is denoted by CRDth.
Output: Flow  is assigned a higher rate code.
is assigned a higher rate code.
begin
-
(1)
for
 to
to  do
do -
(2)
Compute
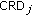 for all flows assigned to
for all flows assigned to  -hop affinity-mate codes of
-hop affinity-mate codes of 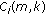 .
. -
(3)
if there exists an available
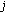 -hop affinity-mate of the required rate that is not assigned to a
-hop affinity-mate of the required rate that is not assigned to areal-time call code for which
 then
then -
(4)
Assign this
 -hop affinity-mate code to flow
-hop affinity-mate code to flow  . Exit ASSIGN HRC.
. Exit ASSIGN HRC. -
(5)
endfor
-
(6)
if(none of the above affinity-mate codes are available) and (flow
 is real-time) and (the residual
is real-time) and (the residualnetwork capacity can support the average rate of flow
 ) then
) then -
(7)
Call CBR to assign a free code to
 by doing code reassignments among non-real-time flows,
by doing code reassignments among non-real-time flows,so that
 is reduced.
is reduced. -
(8)
else if(flow
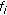 is non-real-time) and (code
is non-real-time) and (code 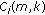 of flow
of flow 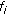 is not available) and (there is residual
is not available) and (there is residualnetwork capacity left) then
-
(9)
if(
 ) then
) then -
(10)
Call CBR to assign a free code to
 by doing code reassignments among non-real-time flows,
by doing code reassignments among non-real-time flows,so that
 is reduced.
is reduced. -
(11)
endif
-
(12)
else
-
(13)
Use the same code
 of flow
of flow 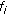 in this frame as well if it is available. Otherwise no code
in this frame as well if it is available. Otherwise no codeis assigned to flow
 for this frame.
for this frame. -
(14)
endif
end
5. Class-Based Fair Code Allocation (CFCA) Protocol for OFCDM-Based 4G Wireless Systems
Variable spreading factor orthogonal frequency division multiplexing (VSF-OFCDM) has been proposed as the air interface by NTT-DoCoMo [7] for 4G broadband cellular networks. 4G networks are expected to support data rates of up to 100 Mbps for vehicular users and up to 5 Gbps for pedestrian users. VSF-OFCDM uses two-dimensional spreading of data bits over frequency and time domains to control the multicode interference while taking advantage of the frequency diversity gain [7–11]. Basically, in VSF-OFCDM, each data symbol of call  is first spread over the time domain using a time domain spreading code
is first spread over the time domain using a time domain spreading code  of spreading factor
of spreading factor  and then each time domain symbol is spread over
and then each time domain symbol is spread over  orthogonal subcarriers in the frequency domain. The overall spreading factor, SF, used to spread each call's data symbol is therefore given as
orthogonal subcarriers in the frequency domain. The overall spreading factor, SF, used to spread each call's data symbol is therefore given as  .
.
Increasing time domain spreading reduces intrauser multicode interference, whereas increasing frequency domain spreading increases frequency diversity. Thus a trade-off between reduction of multicode interference and increased frequency domain spreading can be achieved by varying  and
and  . Especially, when the number of users using the same time domain code increases, the loss in signal quality due to multi-code interferece exceeds the gain in signal quality achieved through frequency diversity gain. For example,as shown in Figure 5, OVSF code tree can be used to allocate the time domain and frequency domain spreading codes to calls for two dimensional spreading. Calls A, B, and C are assigned OVSF codes
. Especially, when the number of users using the same time domain code increases, the loss in signal quality due to multi-code interferece exceeds the gain in signal quality achieved through frequency diversity gain. For example,as shown in Figure 5, OVSF code tree can be used to allocate the time domain and frequency domain spreading codes to calls for two dimensional spreading. Calls A, B, and C are assigned OVSF codes  ,
,  , and
, and  , respectively. In Figure 5(a), calls A and B use code
, respectively. In Figure 5(a), calls A and B use code  as the time domain spreading code. In order to satisfy the requirement
as the time domain spreading code. In order to satisfy the requirement  , the frequency domain spreading codes of A and B are
, the frequency domain spreading codes of A and B are  and
and  , respectively. The frequency domain codes are determined by considering the time domain code as the root code of the OVSF tree as shown by the dotted triangle in the figure. In Figure 5(b), calls A and B use codes
, respectively. The frequency domain codes are determined by considering the time domain code as the root code of the OVSF tree as shown by the dotted triangle in the figure. In Figure 5(b), calls A and B use codes  and
and  as the time domain codes, respectively. This increases time domain spreading and also reduces intrauser multicode interference as the time domain codes are used by only one call. The frequency domain codes are again determined by considering the time domain codes as the root codes and they would be
as the time domain codes, respectively. This increases time domain spreading and also reduces intrauser multicode interference as the time domain codes are used by only one call. The frequency domain codes are again determined by considering the time domain codes as the root codes and they would be  and
and  for calls A and B, respectively. The constraints on OVSF code assignment in VSF-OFCDM would be as follows: (i) each call
for calls A and B, respectively. The constraints on OVSF code assignment in VSF-OFCDM would be as follows: (i) each call  should be assigned an exclusive OVSF code
should be assigned an exclusive OVSF code  of spreading factor
of spreading factor  ; (ii) the time domain code
; (ii) the time domain code  of call
of call  should not be the ancestor of the time domain code,
should not be the ancestor of the time domain code,  of any other call
of any other call  ; however,
; however,  code of two or more users can be the same, (iii) the frequency domain spreading factor
code of two or more users can be the same, (iii) the frequency domain spreading factor  is determined so that
is determined so that  .
.
Once an OVSF code of spreading factor  is assigned,
is assigned,  and
and  can be varied as long as constraint (ii) is satisfied. However, just varying
can be varied as long as constraint (ii) is satisfied. However, just varying  is not sufficient to meet rate and delay requirements of users experiencing poor channel conditions. Hence in this case, the assigned OVSF code of spreading factor
is not sufficient to meet rate and delay requirements of users experiencing poor channel conditions. Hence in this case, the assigned OVSF code of spreading factor  has to be varied just like in the case of WCDMA. In the following subsections we will show how CFCA protocol can be used with VSF-OFCDM-based 4G systems to provide delay and rate guarantees under time varying channel conditions.
has to be varied just like in the case of WCDMA. In the following subsections we will show how CFCA protocol can be used with VSF-OFCDM-based 4G systems to provide delay and rate guarantees under time varying channel conditions.
5.1. Class-Based Code Placement for VSF-OFCDM
As shown in Section 4.1, the basic idea behind algorithm CBP is to choose a free code for a new call that can cause the minimal overhead of code reassignments in case of poor channel conditions. Algorithm CBP accomplishes this by assigning an RT call a code adjacent to a free code or a code assigned to an NRT call. This is useful even in the case of VSF-OFCDM systems, because when a higher-rate code is assigned to an RT call during poor channel conditions, the intrauser multicode interference will also be reduced as the NRT calls assigned to the affinity-mate codes will not share the time domain code used by the RT call. Algorithm VSF-OFCDM-CBP enhances algorithm CBP by also choosing the time domain code and frequency domain code for the new call. The time and frequency domain codes are chosen so that the call can take advantage of frequency diversity gain while keeping the intrauser multicode interference low on the time domain code as shown in Algorithm VSF-OFCDM-CBP in Algorithm 5.
Algorithm 5: Algorithm VSF-OFCDM-CBP.
Input: A new call is admitted to the network because there exists at least one free code to support the
requested data rate.
Output: The new call is assigned a free code  . The time domain code
. The time domain code  and the frequency
and the frequency
domain code  are also determined for the call.
are also determined for the call.
begin
-
(1)
Call Algorithm CBP to determine a candidate code
 of
of 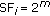 for call
for call  .
. -
(2)
if(an ancestor code of
 is already being used as a time domain code for some other call)
is already being used as a time domain code for some other call)then
-
(3)
Determine the ancestor code
 of code
of code 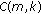 such that it is already used as a time domain
such that it is already used as a time domaincode for some other call.
-
(4)
else
-
(5)
Determine the ancestor code
 of code
of code  such that none of the descendants of
such that none of the descendants of 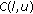
are being used as a time domain code for any other call.
-
(6)
endif
-
(7)
Let
 be the time domain code.
be the time domain code.  .
. -
(8)
Compute the load L on the time domain code
 .
. -
(9)
while(
 and
and  ) do
) do -
(10)
Let
 be the number of calls using
be the number of calls using  as the time domain code. Label them 1 to
as the time domain code. Label them 1 to  from left
from leftto right.
-
(11)
for
 to r do
to r do -
(12)
 .
. -
(13)
 .
. -
(14)
endfor
-
(15)
Determine the descendant code of code
 that can be the new time domain code for call i,
that can be the new time domain code for call i,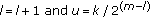 .
. -
(16)
Recompute the load
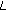 on the new time domain code
on the new time domain code 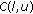 .
. -
(17)
endwhile
-
(18)
Assign
 as the time domain code
as the time domain code  for call
for call  . Determine the frequency domain code
. Determine the frequency domain code for call
for call  so that
so that 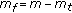 and
and 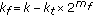
end
Algorithm VSF-OFCDM-CBP first calls algorithm CBP to assign an available free code  for call
for call  on line 1. On lines 2 to 18, the time domain and frequency domain codes are determined. On lines 2 and 3, an initial assignment of time domain code is made so that it is an ancestor code of
on line 1. On lines 2 to 18, the time domain and frequency domain codes are determined. On lines 2 and 3, an initial assignment of time domain code is made so that it is an ancestor code of  that is either already used as a time domain code for some other call. If there is no such ancestor code that is already used as a time domain code for other calls, then on line 5, an ancestor code that does not have any descendant codes already used as time domain codes is used as a time domain code. This is done so that the constraint (ii) mentioned above that the time domain code
that is either already used as a time domain code for some other call. If there is no such ancestor code that is already used as a time domain code for other calls, then on line 5, an ancestor code that does not have any descendant codes already used as time domain codes is used as a time domain code. This is done so that the constraint (ii) mentioned above that the time domain code  of call
of call  should not be the ancestor of the time domain code
should not be the ancestor of the time domain code  of any other call
of any other call  is satisfied.
is satisfied.
On lines 7 to 17, the load  on the time domain code is checked to see that the intra user multicode interference does not exceed the threshold
on the time domain code is checked to see that the intra user multicode interference does not exceed the threshold  . If
. If  exceeds the threshold, the time domain spreading is increased to reduce the intra user multicode interference. On lines 10 to 14, the time domain spreading factor of any other calls using code
exceeds the threshold, the time domain spreading is increased to reduce the intra user multicode interference. On lines 10 to 14, the time domain spreading factor of any other calls using code  as the time domain code is also reduced. This is repeated until either the load
as the time domain code is also reduced. This is repeated until either the load  is less than the
is less than the  or the time domain spreading factor cannot be increased any further. The load
or the time domain spreading factor cannot be increased any further. The load  can be a simple function of the number of calls using the same time domain code.
can be a simple function of the number of calls using the same time domain code.
5.2. Class-Based Code Replacement for VSF-OFCDM
This is similar to the CBR algorithm for WCDMA networks except that whenever a code is reassigned, the time domain code has to be determined in a similar fashion as done in the Algorithm CBP-VSF-OFCDM.
5.3. Dynamic Bandwidth Allocation for VSF-OFCDM
The algorithm proposed for WCDMA networks is used without any modifications. Any changes to the time domain and frequency domain spreading are done by the VSF-OFCDM-CBP and CBR algorithms. Whenever the DBA algorithm assigns a higher-rate code, the number of users sharing the time domain code decreases as some of the NRT calls assigned to affinity-mate codes will not be scheduled. This not only reduces frequency diversity gain but also reduces intrauser multicode interference.
6. Performance Analysis
When channel conditions are normal during the whole data transmission, all real-time flows meet their delay requirements because the code placement algorithm CBP assigns those codes that provide  . However, when channel conditions deteriorate, the instantaneous data rate of flow
. However, when channel conditions deteriorate, the instantaneous data rate of flow  may drop to data rates below
may drop to data rates below  . Let
. Let  denote the lowest data rate that real-time flow
denote the lowest data rate that real-time flow  can achieve under poor channel conditions using OVSF code
can achieve under poor channel conditions using OVSF code  . Transmission of data at this lower data rate under poor channel conditions is made possible through the use of adaptive modulation and coding schemes. But, lowering the data rate may lead to delay violations. A higher rate code can achieve a data rate of
. Transmission of data at this lower data rate under poor channel conditions is made possible through the use of adaptive modulation and coding schemes. But, lowering the data rate may lead to delay violations. A higher rate code can achieve a data rate of  under poor channel conditions because of the reduction in spreading factor. Therefore, the algorithm DBA aims to meet the delay guarantee of each real-time flow by assigning a higher data rate OVSF code under poor channel conditions.
under poor channel conditions because of the reduction in spreading factor. Therefore, the algorithm DBA aims to meet the delay guarantee of each real-time flow by assigning a higher data rate OVSF code under poor channel conditions.
Lemma 1.
Consider a real-time flow  with the average data rate
with the average data rate  , the poor-channel data rate
, the poor-channel data rate  , and
, and  . Assume that when flow
. Assume that when flow  is admitted to the network, it is assigned initially a code supporting the data rate
is admitted to the network, it is assigned initially a code supporting the data rate  under normal channel conditions, which is sufficient to meet the deadline guarantee of
under normal channel conditions, which is sufficient to meet the deadline guarantee of  . When the data rate of flow
. When the data rate of flow  later drops to
later drops to  due to poor channel conditions, the algorithm DBA can still meet the delay guarantee of flow
due to poor channel conditions, the algorithm DBA can still meet the delay guarantee of flow  , provided that the channel conditions are not worse than the expected poor channel conditions in Step 1 of CFCA.
, provided that the channel conditions are not worse than the expected poor channel conditions in Step 1 of CFCA.
Proof.
See the appendix.
As for the non-real-time flows, when the admitted real-time flows do not experience poor channel conditions, CFCA allows the residual network capacity to be used fairly by non-real-time flows. The following lemma indicates that the fairness bound among non-real-time flows is derived by showing that the CRD difference, denoted by CRDdiff, of any two non-real-time flows is bounded by CRDth.
Lemma 2.
Consider  continuously backlogged non-real-time flows,
continuously backlogged non-real-time flows,  , for
, for  . The algorithm DBA guarantees that the difference between the CRD values of any two non-real-time flows
. The algorithm DBA guarantees that the difference between the CRD values of any two non-real-time flows  and
and  with the same channel conditions does not exceed a positive constant CRDth, that is,
with the same channel conditions does not exceed a positive constant CRDth, that is,  .
.
Proof.
See the appendix.
7. Simulation Results
This section presents the simulation results for the performance of the CFCA protocol using a simulator written in  . The simulation environment consists of 100 mobiles uniformly distributed in a cell of radius 3000 meters. Multiple simulation runs are done for a duration of 5000 frames. The call arrival rate follows the Poisson distribution with a mean arrival rate of 1 to 10 calls per second. The traffic types of the calls are generated using a uniform distribution so that there are equal number of calls for each traffic class (conversational class 0 to background class 3). The requested average rate of calls is uniformly distributed between 75 and 1200 Kbps. The call holding time is exponentially distributed with a mean holding time of 10 seconds (i.e., 1000 frames for a frame time of 10 milliseconds). During the call holding time, a number of packets are generated using an exponential distribution with mean packet size of 500 bits.
. The simulation environment consists of 100 mobiles uniformly distributed in a cell of radius 3000 meters. Multiple simulation runs are done for a duration of 5000 frames. The call arrival rate follows the Poisson distribution with a mean arrival rate of 1 to 10 calls per second. The traffic types of the calls are generated using a uniform distribution so that there are equal number of calls for each traffic class (conversational class 0 to background class 3). The requested average rate of calls is uniformly distributed between 75 and 1200 Kbps. The call holding time is exponentially distributed with a mean holding time of 10 seconds (i.e., 1000 frames for a frame time of 10 milliseconds). During the call holding time, a number of packets are generated using an exponential distribution with mean packet size of 500 bits.
A simplified  model as given in (2) is used as the channel model. Intracell orthogonality factor is set to 0.4. Path loss
model as given in (2) is used as the channel model. Intracell orthogonality factor is set to 0.4. Path loss  is computed as a function of distance
is computed as a function of distance  as given in (4), where
as given in (4), where  is chosen as 4. Slow fading,
is chosen as 4. Slow fading,  is considered to be log-normally distributed around the distance based path loss
is considered to be log-normally distributed around the distance based path loss  with zero mean and a standard deviation of 8 dB. A random way-point mobility model is used. Fast fading,
with zero mean and a standard deviation of 8 dB. A random way-point mobility model is used. Fast fading,  is generated using a Rayleigh fading distribution with zero mean and a standard deviation of 12 dB. The value of
is generated using a Rayleigh fading distribution with zero mean and a standard deviation of 12 dB. The value of  in (16) is chosen as 20 frames, and the values of
in (16) is chosen as 20 frames, and the values of  for the four traffic classes are made equal to 2, 5, 10, and 20, respectively. CRDth is set equal to 0.4 for the purpose of simulations. The value of
for the four traffic classes are made equal to 2, 5, 10, and 20, respectively. CRDth is set equal to 0.4 for the purpose of simulations. The value of  in
in  -hop affinity-mate is set to 3.
-hop affinity-mate is set to 3.
For the purpose of comparison with the CFCA protocol, we choose four other schemes that are distinguishable from the CFCA protocol in the choice of the code placement algorithm and/or the dynamic bandwidth allocation algorithm. We call the first scheme the first come first served (FCFS). The FCFS scheme makes use of the leftmost first code (LFC) placement algorithm that assigns the leftmost available free code to a new call. The FCFS scheme serves the flows during dynamic bandwidth allocation in the order of their arrival; that is, there is no special mechanism neither to increase the data rate of flows experiencing delay violations nor to prioritize the flows based on fairness conditions. The second scheme is called as the (CFC-DBA) scheme, and as the name implies, this scheme makes use of the crowded first code placement algorithm presented in [14] and uses the DBA algorithm proposed in this paper to prioritize and schedule the flows dynamically. However, the DBA algorithm in the (CFC-DBA) scheme chooses an arbitrary code to increase the bandwidth allocation instead of a higher-rate code that is not an  -hop affinity-mate.
-hop affinity-mate.
The third scheme we used for comparison is scheme 3 of the dynamic bandwidth allocation algorithm presented in [3]. We have chosen scheme 3 of [3] because of its better performance results over the schemes 1 and 2 presented in [3]. We call this scheme CHAU in this paper. This scheme uses a credit-based scheme to prioritize real-time and non-real-time flows. The dynamic bandwidth allocation presented in [3] tries to assign a flow with the highest priority (credit) a code to meet its requested peak rate, which is greater than the requested average rate of the flow. If a code of the requested peak rate is not available, a descendant code of highest possible rate is assigned. As a result, a flow with lower priority may not get a code assignment in a given time slot. The fourth scheme we used for comparison is the one presented in [34]. We call this scheme KAM. In this scheme, flows are again prioritized using a credit-based scheme and flows with highest priority are assigned higher rate ancestor codes as long as they have back logged data greater than the rate supported by the higher-rate code and enough credits equivalent to the credits corresponding to the higher-rate code.
In the simulations we assume that (i) none of the real-time flows experience worse channel conditions than the expected poor channel conditions, and (ii) a packet has a delay bound of 1 packet transmission time, which is equal to the size of the packet divided by the requested average rate of the flow. With these assumptions, Figure 6 shows the probability of delay violations experienced by real-time flows. In case of CFCA and (CFC-DBA), the number of delay violations of real-time packets is 0 at all loads. The admission control presented in Section 4 and the DBA algorithm help CFCA and (CFC-DBA) achieve this result. Since (CFC-DBA) does not use the concept of  -hop affinity-mate, it will incur more signaling overhead, which is shown in Figure 8. FCFS scheme has a delay violation probability at all loads because FCFS does not do any dynamic bandwidth allocation to compensate for the loss in data rate due to poor channel conditions. At very low loads of up to 50 Erlangs, CHAU and KAM achieve a very low delay violation probability of 0. At low loads, the OVSF code tree has free capacity and CHAU and KAM allocate this free capacity to real-time flows with poor channel conditions. As the load increases, the delay violation probability increases for CHAU and KAM. CHAU, and KAM do not distinguish between real-time and non-real-time flows during prioritization. As a result, real-time flows may not receive a higher priority sometimes in code allocation. The reason for KAM to have higher delay violations than CHAU is due to the fact that KAM only tries to assign a higher rate ancestor code and two real-time calls assigned to sibling codes might block each other. Figure 7 shows the average delay experienced by real-time packets. At low loads, CHAU and KAM have lower average delay than CFCA. This can be attributed to the fact CHAU and KAM always try to assign a higher-rate code when the OVSF code tree has enough capacity, unlike CFCA that assigns a higher-rate code only when the value of CRD becomes greater than 0.
-hop affinity-mate, it will incur more signaling overhead, which is shown in Figure 8. FCFS scheme has a delay violation probability at all loads because FCFS does not do any dynamic bandwidth allocation to compensate for the loss in data rate due to poor channel conditions. At very low loads of up to 50 Erlangs, CHAU and KAM achieve a very low delay violation probability of 0. At low loads, the OVSF code tree has free capacity and CHAU and KAM allocate this free capacity to real-time flows with poor channel conditions. As the load increases, the delay violation probability increases for CHAU and KAM. CHAU, and KAM do not distinguish between real-time and non-real-time flows during prioritization. As a result, real-time flows may not receive a higher priority sometimes in code allocation. The reason for KAM to have higher delay violations than CHAU is due to the fact that KAM only tries to assign a higher rate ancestor code and two real-time calls assigned to sibling codes might block each other. Figure 7 shows the average delay experienced by real-time packets. At low loads, CHAU and KAM have lower average delay than CFCA. This can be attributed to the fact CHAU and KAM always try to assign a higher-rate code when the OVSF code tree has enough capacity, unlike CFCA that assigns a higher-rate code only when the value of CRD becomes greater than 0.
While any code placement scheme can achieve a delay performance comparable to that of our scheme using our DBA algorithm, the drawback of such schemes is that they do not consider the overhead of code allocation in dynamic bandwidth allocation. This is evident in Figure 8 where (CFC-DBA) has a much higher overhead when compared to CFCA, though they both use the same DBA algorithm. The FCFS scheme has no overhead, but it incurs significant delay, rate, and fairness violations. In case of CHAU and (CFC-DBA) any code assignment is informed using the entire branch and layer numbers of the code. Therefore, the signaling overhead is high. CFCA and KAM use fewer bits to inform code assignments during dynamic bandwidth allocation because they almost always use ancestor codes during dynamic bandwidth allocation. KAM has a lower signaling overhead when compared to CFCA because KAM only uses its ancestor codes for reassignments, whereas CFCA sometimes assigns a code that is not an  -hop affinity-mate. In our simulations we found the reduction in the control overhead because of the CFCA protocol that makes use of the concept of
-hop affinity-mate. In our simulations we found the reduction in the control overhead because of the CFCA protocol that makes use of the concept of  -hop affinity-mate and KAM to be 60% less than the (CFC+DBA) and CHAU scheme as shown in Figure 8.
-hop affinity-mate and KAM to be 60% less than the (CFC+DBA) and CHAU scheme as shown in Figure 8.
To measure the fairness for non-real-time traffic types from the perspective of satisfying average rates, we employ the satisfaction index parameter SI defined in [30, 45] as  , where
, where  is equal to 1 if a flow receives at least the average requested data rate and is equal to
is equal to 1 if a flow receives at least the average requested data rate and is equal to  otherwise. If SI equals 1, 100% of the flows meet their average rate requirements fairly. Thus, this serves as a measure of how fairly the average rate requirements of flows are met. As can be seen from Figure 9, the CFCA, CHAU, and KAM achieve better user satisfaction. For CFCA, at a load of 100 Erlangs, 95% of the flows meet their average rate requirements fairly. CHAU and KAM have a slightly higher satisfaction index than CFCA because, CHAU and KAM treat real-time and non-real-time flows in the same fashion, whereas CFCA assigns a higher priority to real-time flows over non-real-time flows. This results in some unfairness to non-real-time flows because real-time flows may use the codes originally assigned to non-real-time flows.
otherwise. If SI equals 1, 100% of the flows meet their average rate requirements fairly. Thus, this serves as a measure of how fairly the average rate requirements of flows are met. As can be seen from Figure 9, the CFCA, CHAU, and KAM achieve better user satisfaction. For CFCA, at a load of 100 Erlangs, 95% of the flows meet their average rate requirements fairly. CHAU and KAM have a slightly higher satisfaction index than CFCA because, CHAU and KAM treat real-time and non-real-time flows in the same fashion, whereas CFCA assigns a higher priority to real-time flows over non-real-time flows. This results in some unfairness to non-real-time flows because real-time flows may use the codes originally assigned to non-real-time flows.
8. Conclusion
The performance of WCDMA- and VSF-OFCDM-based cellular networks depends on the proper utilization of OVSF codes. OVSF codes suffer from the code blocking problem. Hence, OVSF code allocation and reassignment algorithms have significant impact on the performance of WCDMA-based cellular networks. Dynamic bandwidth allocation, which is done to meet rate and delay requirements in WCDMA systems involves dynamic OVSF code assignments. But, dynamic code assignments involve significant control overhead because of code blocking. Therefore, code allocation should be designed with dynamic code assignment in mind so that signaling overhead of DCA is low. This paper has proposed a code allocation algorithm, CBP, that allocates codes to flows by considering the possibility of assigning higher rate codes to flows when they experience poor channel conditions. The CBP algorithm reduces the overhead of code reassignments through the concept of  -hop affinity-mate. The proposed code reassignment algorithm, CBR, reduces the number of reassignments experienced by real-time calls, while assisting the DBA algorithm in meeting the delay and rate requirements of calls. The CRD metric prioritizes the flows for dynamic bandwidth allocation and ensures fairness in terms of both delay and rate. Delay and rate guarantees for real-time flows are met as long as their channel conditions are not worse than the expected poor channel conditions. Simulation results show that the proposed CFCA protocol reduces the control overhead for reassignments by 60% at high network loads for WCDMA systems. The proposed VSF-OFCDM-CBP algorithm, determines the time domain and frequency domain spreading factors so that the frequency domain spreading is maximized while keeping the intrauser multicode interference on time domain codes low.
-hop affinity-mate. The proposed code reassignment algorithm, CBR, reduces the number of reassignments experienced by real-time calls, while assisting the DBA algorithm in meeting the delay and rate requirements of calls. The CRD metric prioritizes the flows for dynamic bandwidth allocation and ensures fairness in terms of both delay and rate. Delay and rate guarantees for real-time flows are met as long as their channel conditions are not worse than the expected poor channel conditions. Simulation results show that the proposed CFCA protocol reduces the control overhead for reassignments by 60% at high network loads for WCDMA systems. The proposed VSF-OFCDM-CBP algorithm, determines the time domain and frequency domain spreading factors so that the frequency domain spreading is maximized while keeping the intrauser multicode interference on time domain codes low.
Appendix
Proof of Lemma 1.
In order to show that the algorithm DBA meets the delay guarantee of flow  , it suffices to show that flow
, it suffices to show that flow  does not achieve a data rate less than its average data rate in more than
does not achieve a data rate less than its average data rate in more than  consecutive time slots out of
consecutive time slots out of  consecutive time slots. When flow
consecutive time slots. When flow  experiences poor channel conditions, its
experiences poor channel conditions, its  value increases above zero. Line 17 of the DBA algorithm assigns a higher-rate code to a real-time flow, when it finds the
value increases above zero. Line 17 of the DBA algorithm assigns a higher-rate code to a real-time flow, when it finds the  value of the flow to be greater than zero. Thus, in the worst case,
value of the flow to be greater than zero. Thus, in the worst case,  of flow
of flow  would be greater than zero in only one window out of
would be greater than zero in only one window out of  windows. Therefore, as long as higher-rate code and required power budget can be allocated to the real-time flow
windows. Therefore, as long as higher-rate code and required power budget can be allocated to the real-time flow  , the average data rate would not be met in only
, the average data rate would not be met in only  time slots out of
time slots out of  time slots.
time slots.
This indicates that, in order to prove the lemma, we need to show that a higher-rate code can be assigned to a real-time flow when its  becomes greater than zero. Assignment of a higher-rate code for a frame is possible as long as the network has residual network capacity after allocating
becomes greater than zero. Assignment of a higher-rate code for a frame is possible as long as the network has residual network capacity after allocating  for all real-time flows. Step 1 of CFCA ensures that this residual network capacity is available as long as the channel conditions are not worse than the expected poor channel conditions. To prove that a higher-rate code is available and not blocked, there are three cases to be considered in ASSIGN_HRC, depending on the status of the affinity-mate codes of flow
for all real-time flows. Step 1 of CFCA ensures that this residual network capacity is available as long as the channel conditions are not worse than the expected poor channel conditions. To prove that a higher-rate code is available and not blocked, there are three cases to be considered in ASSIGN_HRC, depending on the status of the affinity-mate codes of flow  's code.
's code.
Case 1.
In this case, it is assumed that the  -hop affinity-mate codes of
-hop affinity-mate codes of  's code are free, for
's code are free, for  . In lines 1 to 5 of ASSIGN_HRC, flow
. In lines 1 to 5 of ASSIGN_HRC, flow  is assigned such a free affinity-mate code that makes
is assigned such a free affinity-mate code that makes  equal to zero.
equal to zero.
Case 2.
In this case, it is assumed that the  -hop affinity-mates of
-hop affinity-mates of  's code are not free, but at least one of them is assigned to a non-real-time flow. Because
's code are not free, but at least one of them is assigned to a non-real-time flow. Because  has higher priority than the non-real-time flow, the higher rate affinity-mate code of
has higher priority than the non-real-time flow, the higher rate affinity-mate code of  is assigned to
is assigned to  to make
to make  zero.
zero.
Case 3.
In this case, it is assumed that all the  -hop affinity-mate codes of
-hop affinity-mate codes of  's code are already assigned to real-time flow. In lines 6 to 7 of ASSIGN_HRC, flow
's code are already assigned to real-time flow. In lines 6 to 7 of ASSIGN_HRC, flow  is assigned a code by doing code reassignments in the algorithm CBR, so that
is assigned a code by doing code reassignments in the algorithm CBR, so that  is made equal to zero.
is made equal to zero.
Proof of Lemma 2.
Consider two continuously backlogged flows  and
and  that have identical channel conditions. The worst case condition for the fairness bound occurs when one non-real-time flow
that have identical channel conditions. The worst case condition for the fairness bound occurs when one non-real-time flow  is always assigned its requested data rate whereas another flow
is always assigned its requested data rate whereas another flow  is not assigned any data rate. In this case, CRDdiff (i.e., the difference in the CRD values of
is not assigned any data rate. In this case, CRDdiff (i.e., the difference in the CRD values of  and
and  ) becomes the maximum. Recall that a CRD value ranges from 0 to 1, so that the maximum difference between two CRD values could be 1. Let us assume that
) becomes the maximum. Recall that a CRD value ranges from 0 to 1, so that the maximum difference between two CRD values could be 1. Let us assume that  at the current frame, where
at the current frame, where  . In addition, because a CRD is computed over
. In addition, because a CRD is computed over  time slots (or frames), the value of a CRD can increase or decrease by at most
time slots (or frames), the value of a CRD can increase or decrease by at most  over a frame time. Note that if the CRD values of both flows decrease or increase at the same time, then CRDdiff does not change. Therefore, the only case where CRDdiff exceeds CRDth at the next frame is that the CRD value of one flow increases while the CRD value of the other flow decreases. We will show next that the algorithms DBA and ASSIGN_HRC do not allow this case to occur.
over a frame time. Note that if the CRD values of both flows decrease or increase at the same time, then CRDdiff does not change. Therefore, the only case where CRDdiff exceeds CRDth at the next frame is that the CRD value of one flow increases while the CRD value of the other flow decreases. We will show next that the algorithms DBA and ASSIGN_HRC do not allow this case to occur.
Without loss of generality, let us assume that  and
and  at current frame time. Because
at current frame time. Because  equals CRDth, line 25 in the algorithm DBA chooses flow
equals CRDth, line 25 in the algorithm DBA chooses flow  due to its higher CRD value for code allocation. Because
due to its higher CRD value for code allocation. Because  , line 27 in the algorithm DBA invokes ASSIGN_HRC to assign a higher-rate code to flow
, line 27 in the algorithm DBA invokes ASSIGN_HRC to assign a higher-rate code to flow  . If line 10 in ASSIGN_HRC assigns a free code to flow
. If line 10 in ASSIGN_HRC assigns a free code to flow  ,
,  is reduced and, therefore, CRDdiff does not exceed CRDth. On the other hand, if line 10 in ASSIGN_HRC cannot assign a free code to flow
is reduced and, therefore, CRDdiff does not exceed CRDth. On the other hand, if line 10 in ASSIGN_HRC cannot assign a free code to flow  ,
,  and the CRD value of any other flow including
and the CRD value of any other flow including  increase, thereby keeping CRDdiff the same. (Note that if
increase, thereby keeping CRDdiff the same. (Note that if  cannot be assigned a code, the other non-real-time flows cannot be assigned a code either because
cannot be assigned a code, the other non-real-time flows cannot be assigned a code either because  has the highest priority due to its highest CRD value.) It follows that CRDdiff does not increase beyond CRDth at any frame time.
has the highest priority due to its highest CRD value.) It follows that CRDdiff does not increase beyond CRDth at any frame time.
References
Hanzo L, Liew TH: Adaptive coding and transmission paradigms for wireless channels. In Proceedings of the 2nd IMA International Conference on Mathematics in Communications, 2002, London, UK. University of Lancaster; 1-8.
Qiu X, Chawla K: On the performance of adaptive modulation in cellular systems. IEEE Transactions on Communications 1999, 47(6):884-895. 10.1109/26.771345
Chao C-M, Tseng Y-C, Wang L-C: Dynamic bandwidth allocation for multimedia traffic with rate guarantee and fair access in WCDMA systems. Proceedings of the 6th ACM International Workshop on Modeling, Analysis and Simulation of Wireless and Mobile Systems (MSWiM '03), September 2003, San Diego, Calif, USA 136-139.
Adachi F, Sawahashi M, Okawa K: Tree-structured generation of orthogonal spreading codes with different lengths for forward link of DS-CDMA mobile radio. Electronics Letters 1997, 33(1):27-28. 10.1049/el:19970022
Chih-Lin I, Gitlin RD: Multi-code CDMA wireless personal communications networks. Proceedings of the IEEE International Conference on Communications, June 1995 1060-1064.
Çam H: Non-blocking OVSF codes and enhancing network capacity for 3G wireless and beyond systems. Computer Communications 2003, 26(17):1907-1917. 10.1016/S0140-3664(03)00156-7
Atarashi H, Abeta S, Sawahashi M: Variable spreading factor-orthogonal frequency and code division multiplexing (VSF-OFCDM) for broadband packet wireless access. IEICE Transactions on Communications 2003, E86-B(1):291-299.
Atarashi H, Maeda N, Abeta S, Sawahashi M: Broadband packet wireless access based on vsf-ofcdm and mc/ds-cdma. IEICE Transactions on Communications 2002, 291-299.
Maeda N, Kishiyama Y, Atarashi H, Sawahashi M: Variable spreading factor-OFCDM with two dimensional spreading that prioritizes time domain spreading for forward link broadband wireless access. IEICE Transactions on Communications 2005, E88-B(2):487-497. 10.1093/ietcom/E88-B.2.487
Chang BJ, Wu CH: Adaptive load balancing MDP-based approach of two-dimensional spreading for VSF-OFCDM in 4G next-generation cellular communications. IEEE Transactions on Vehicular Technology 2009, 58(3):1143-1156.
Hasegawa K, Shimura R, Sasase I: OVSF code allocation and two-stage combining method to reduce intercode interference in OFCDM system. Electronics and Communications in Japan. Part I 2007, 90(9):16-24. 10.1002/ecja.20381
Cheng ST, Hsieh MT: Design and analysis of time-based code allocation schemes in W-CDMA systems. IEEE Transactions on Mobile Computing 2005, 4(6):604-615.
Chen YS, Lin TL: Code placement and replacement schemes for WCDMA rotated-OVSF code tree management. IEEE Transactions on Mobile Computing 2006, 5(3):224-239.
Tseng Y-C, Chao C-M: Code placement and replacement strategies for wideband CDMA OVSF code tree management. IEEE Transactions on Mobile Computing 2002, 1(4):293-302. 10.1109/TMC.2002.1175542
Yang Y, Yum TSP: Maximally flexible assignment of orthogonal variable spreading factor codes for multirate traffic. IEEE Transactions on Wireless Communications 2004, 3(3):781-792. 10.1109/TWC.2004.827765
Assarut R, Kawanishi K, Yamamoto U, Onozato Y, Matsushita M: Region division assignment of orthogonal variable-spreading-factor codes in W-CDMA. Proceedings of the 54th IEEE Vehicular Technology Conference (VTC '01), October 2001, Atlantic City, NJ, USA 1884-1888.
Fantacci R, Nannicini S: Multiple access protocol for integration of variable bit rate multimedia traffic in UMTS/IMT-2000 based on wideband CDMA. IEEE Journal on Selected Areas in Communications 2000, 18(8):1441-1454. 10.1109/49.864009
Chen WT, Wu YP, Hsiao HC: A novel code assignment scheme for W-CDMA systems. Proceedings of the 54th IEEE Vehicular Technology Conference (VTC '01), October 2001, Atlantic City, NJ, USA 1182-1186.
Tsai YR, Lin LIC: Quality based OVSF code assignment and reassignment strategies for WCDMA systems. Proceedings of the International Conference on Wireless Networks, Communications and Mobile Computing, June 2005 238-243.
Chen J-C, Chen W-SE: Queue-aided BLRU scheme for orthogonal variable-spreading-factor code assignment in 3G WCDMA. Proceedings of the 14th International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC '03), Sepember 2003, Beijing, China 1: 74-78.
Rouskas AN, Skoutas DN: OVSF codes assignment and reassignment at the forward link of W-CDMA. Proceedings of the 13th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC '02), September 2002, Lisbon, Portugal 5: 2404-2408.
Dell'Amico M, Merani ML, Maffioli F: Efficient algorithms for the assignment of OVSF codes in wideband CDMA. Proceedings of the International Conference on Communications (ICC '02), May 2002 5: 3055-3060.
Dell'Amico M, Maffioli F, Merani ML: A tree partitioning dynamic policy for OVSF codes assignment in wideband CDMA. IEEE Transactions on Wireless Communications 2004, 3(4):1013-1017. 10.1109/TWC.2004.827768
Sekine Y, Kawanishi K, Yamamoto U, Onozato Y: Hybrid OVSF code assignment scheme in W-CDMA. Proceedings of the EEE Pacific Rim Conference on Communications Computers and Signal Processing (PACRIM '03), August 2003 1: 384-387.
Assarut R, Kawanishi K, Yamamoto U, Onozato Y: Performance evaluation of orthogonal variable-spreading-factor code assignment schemes based on UMTS/IMT-2000 in W-CDMA. Proceedings of the 56th IEEE Vehicular Technology Conference (VTC '02), September 2002, Vancouver, Canada 3: 1585-1589.
Minn T, Siu KY: Dynamic assignment of orthogonal variable-spreading-factor codes in W-CDMA. IEEE Journal on Selected Areas in Communications 2000, 18(8):1429-1440. 10.1109/49.864008
Shueh F-F, Chen W-SE: Minimizing WCDMA channel reallocation. Proceedings of the 14th International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC '03), Sepember 2003, Beijing, China 1: 41-45.
Xu L, Shen X, Mark JW: Fair resource allocation with guaranteed statistical QoS for multimedia traffic in wideband CDMA cellular network. IEEE Transactions on Mobile Computing 2005, 4(2):166-177.
Zhao D, Shen X, Mark JW: Radio resource management for cellular CDMA systems supporting heterogeneous services. IEEE Transactions on Mobile Computing 2003, 2(2):147-160. 10.1109/TMC.2003.1217235
Chao HL, Liao W: Credit-based slot allocation for multimedia mobile ad hoc networks. IEEE Journal on Selected Areas in Communications 2003, 21(10):1642-1651. 10.1109/JSAC.2003.815232
Fossa CE, Davis NJ: Dynamic code assignment improves channel utilization for bursty traffic in third-generation wireless networks. Proceedings of the International Conference on Communications (ICC '02), May 2002 5: 3061-3065.
Chen M, Hwang R-H: Fair and efficient scheduling algorithms for multiple classes of service under QoS guarantee in UMTS. International Journal of Communication Systems 2005, 18(4):409-426. 10.1002/dac.714
Kim DI, Hossain E, Bhargava VK: Dynamic rate and power adaptation for provisioning class-based QoS in cellular multirate WCDMA systems. IEEE Transactions on Wireless Communications 2004, 3(5):1590-1601. 10.1109/TWC.2004.833492
Kam AC, Minn T, Siu KY: Supporting rate guarantee and fair access for bursty data traffic in W-CDMA. IEEE Journal on Selected Areas in Communications 2001, 19(11):2121-2130. 10.1109/49.963799
Záruba GV, Chlamtac I, Das SK: A prioritized real-time wireless call degradation framework for optimal call mix selection. Mobile Networks and Applications 2002, 7(2):143-151. 10.1023/A:1013726921905
Holma H, Toskala A: WCDMA for UMTS: Radio Access for Third Generation Mobile Communications. 2nd edition. John Wiley & Sons, New York, NY, USA; 2002.
Reyaz T, Burr A: Performance analysis of different spreading factors in various channel conditions with channel estimation for uplink WCDMA. Proceedings of the 16th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC '05), September 2005, Berlin, Germany 1204-1208.
Stallings W: Wireless Communications and Networks. Prentice-Hall, Upper Saddle River, NJ, USA; 2002.
Amaldi E, Capone A, Malucelli F: Planning UMTS base station location: optimization models with power control and algorithms. IEEE Transactions on Wireless Communications 2003, 2(5):939-952. 10.1109/TWC.2003.817438
Amaldi E, Capone A, Malucelli F: Optimizing base station siting in UMTS networks. Proceedings of the 53rd IEEE Vehicular Technology Conference (VTC '01), May 2001, Rhodes, Greece 2828-2832.
Sohn S, Jo GS: Optimization of base stations positioning in mobile networks. International Conference on Computational Science and Its Applications (ICCSA '06), 2006, Glasgow, UK, Lecture Notes in Computer Science 3981: 779-787.
Dottling M, Michel J, Raaf B: Hybrid ARQ and adaptive modulation and coding schemes for high speed downlink packet access. Proceedings of the 13th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC '02), September 2002, Lisbon, Portugal 1073-1077.
Sallent O, Pérez-Romero J, Casadevall FJ, Agustí R: An emulator framework for a new radio resource management for QoS guaranteed services inc W-CDMA systems. IEEE Journal on Selected Areas in Communications 2001, 19(10):1893-1904. 10.1109/49.957305
Chou CT, Shin KG: Analysis of adaptive bandwidth allocation in wireless networks with multilevel degradable quality of service. IEEE Transactions on Mobile Computing 2004, 3(1):5-17. 10.1109/TMC.2004.1261813
Jain RK, Chiu DW, Hawe WR: A quantitative measure of fairness and discrimination for resource allocation in shared computer system. DEC; 1984.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License (https://creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Challa, N., Çam, H. Class-Based Fair Code Allocation with Delay Guarantees for OVSF-CDMA and VSF-OFCDM in Next-Generation Cellular Networks. J Wireless Com Network 2010, 738325 (2010). https://doi.org/10.1155/2010/738325
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1155/2010/738325

 denote the number of those free OVSF codes whose SF equals
denote the number of those free OVSF codes whose SF equals  . Label them 1 to
. Label them 1 to  from
from to
to  do
do to
to  do
do -hop affinity-mate of the free code
-hop affinity-mate of the free code  is blocked or being used by an RT call) then
is blocked or being used by an RT call) then
 -hop affinity-mate of the free code
-hop affinity-mate of the free code  is blocked or being used only by NRT calls)
is blocked or being used only by NRT calls)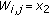
 -hop affinity-mate of the free code
-hop affinity-mate of the free code 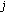 is free) then
is free) then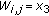
 -hop affinity-mate of the free code
-hop affinity-mate of the free code  is blocked or being used only by NRT calls) then
is blocked or being used only by NRT calls) then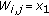
 -hop affinity-mate of the free code
-hop affinity-mate of the free code  is blocked or being used by an RT call) then
is blocked or being used by an RT call) then
 -hop affinity-mate of the free code
-hop affinity-mate of the free code 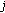 is free) then
is free) then
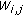 among the
among the  free codes
free codes is the smallest to break the tie. Any further ties are broken
is the smallest to break the tie. Any further ties are broken denote the number of those blocked codes whose SF equals
denote the number of those blocked codes whose SF equals  , and label them from 1 to
, and label them from 1 to  .
. codes determine the codes that have the maximum weight
codes determine the codes that have the maximum weight  for values of
for values of 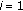
 and
and 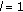 to
to  .
. that has the least number of busy descendant codes assigned to real-time
that has the least number of busy descendant codes assigned to real-time denote the number of those codes whose SF equals
denote the number of those codes whose SF equals  . Label them from 1 to
. Label them from 1 to  .
.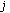 that has the least number of busy descendant codes assigned to real-time
that has the least number of busy descendant codes assigned to real-time denote the number of those codes of
denote the number of those codes of  that are free or assigned or blocked by
that are free or assigned or blocked by is not available, search for a free code of the nearest
is not available, search for a free code of the nearest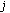 that is assigned to a non-real-time call with the minimum CRD value. Any
that is assigned to a non-real-time call with the minimum CRD value. Any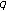 denote the number of calls that are already assigned
denote the number of calls that are already assigned  descendants codes of code
descendants codes of code 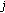 .
. , assign a code using the CBP algorithm, if there are more than one code of
, assign a code using the CBP algorithm, if there are more than one code of for the call. If no code is available of the required SF, then call CBR again to
for the call. If no code is available of the required SF, then call CBR again to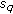 .
. to the new call or to the existing real-time or non-real-time call requesting code
to the new call or to the existing real-time or non-real-time call requesting code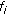 its initial code
its initial code  (
(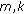 ) even if
) even if  was assigned a different code during
was assigned a different code during count + 1; for each flow
count + 1; for each flow 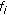 , compute
, compute 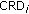 if (count mod
if (count mod 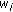 ) = 0.
) = 0. to 3 do
to 3 do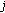 is 0 then
is 0 then "conversational".
"conversational". is 1 then
is 1 then "streaming".
"streaming". is 2 then
is 2 then "interactive".
"interactive". is 3then
is 3then "background".
"background". equal the number of all those flows of class type.
equal the number of all those flows of class type. and
and  do
do denote the class flow with the highest CRD value among those class flows that are
denote the class flow with the highest CRD value among those class flows that are then
then ,
, 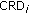 ,
, 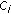 (
(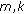 )).
)).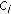 (
( ) of flow
) of flow  in this frame as well.
in this frame as well.
 and
and  do
do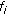 denote the class flow with the highest CRD value among those class flows that
denote the class flow with the highest CRD value among those class flows that ) and (Code
) and (Code 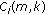 of flow
of flow  are not available due to its assignment to a
are not available due to its assignment to a ,
,  ,
, 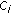 (
( )).
)).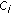 (
( ) of flow
) of flow 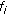 in this frame as well if it is available. Otherwise
in this frame as well if it is available. Otherwise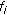 for this frame.
for this frame.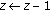



 to
to  do
do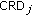 for all flows assigned to
for all flows assigned to  -hop affinity-mate codes of
-hop affinity-mate codes of 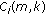 .
. -hop affinity-mate of the required rate that is not assigned to a
-hop affinity-mate of the required rate that is not assigned to a then
then -hop affinity-mate code to flow
-hop affinity-mate code to flow  . Exit ASSIGN HRC.
. Exit ASSIGN HRC. is real-time) and (the residual
is real-time) and (the residual ) then
) then by doing code reassignments among non-real-time flows,
by doing code reassignments among non-real-time flows, is reduced.
is reduced. is non-real-time) and (code
is non-real-time) and (code  of flow
of flow 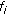 is not available) and (there is residual
is not available) and (there is residual ) then
) then by doing code reassignments among non-real-time flows,
by doing code reassignments among non-real-time flows, is reduced.
is reduced. of flow
of flow 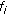 in this frame as well if it is available. Otherwise no code
in this frame as well if it is available. Otherwise no code for this frame.
for this frame.
 in (a). (b) shows how descendant codes of
in (a). (b) shows how descendant codes of  are assigned to calls A and B to reduce the multicode interference.
are assigned to calls A and B to reduce the multicode interference. of
of 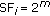 for call
for call  .
. is already being used as a time domain code for some other call)
is already being used as a time domain code for some other call) of code
of code  such that it is already used as a time domain
such that it is already used as a time domain of code
of code  such that none of the descendants of
such that none of the descendants of 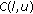
 be the time domain code.
be the time domain code.  .
. .
. and
and  ) do
) do be the number of calls using
be the number of calls using  as the time domain code. Label them 1 to
as the time domain code. Label them 1 to  from left
from left to r do
to r do .
. .
. that can be the new time domain code for call i,
that can be the new time domain code for call i,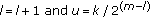 .
. on the new time domain code
on the new time domain code  .
. as the time domain code
as the time domain code  for call
for call  . Determine the frequency domain code
. Determine the frequency domain code for call
for call  so that
so that 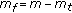 and
and