- Research Article
- Open access
- Published:
Perimeter Coverage Scheduling in Wireless Sensor Networks Using Sensors with a Single Continuous Cover Range
EURASIP Journal on Wireless Communications and Networking volume 2010, Article number: 926075 (2010)
Abstract
In target monitoring problem, it is generally assumed that the whole target object can be monitored by a single sensor if the target falls within its sensing range. Unfortunately, this assumption becomes invalid when the target object is very large that a sensor can only monitor part of it. In this paper, we study the perimeter coverage problem where the perimeter of a big object needs to be monitored, but each sensor can only cover a single continuous portion of the perimeter. We describe how to schedule the sensors so as to maximize the network lifetime in this problem. We formally prove that the perimeter coverage scheduling problem is NP-hard in general. However, polynomial time solution exists in some special cases. We further identify the sufficient conditions for a scheduling algorithm to be a 2-approximation solution to the general problem, and propose a simple distributed 2-approximation solution with a small message overhead.
1. Introduction
Wireless sensor networks have caught lots of attention in recent years. One of the major problems is the coverage problem. Traditionally, coverage problems concern whether a certain target area or a certain target object can be fully monitored by the sensors collaboratively. Instead of considering whether a certain area or a certain target object is completely covered, we focus on a specific coverage problem called the perimeter coverage problem. In this problem, we want to monitor the perimeter of a big target but each sensor can only monitor part of the perimeter. One typical application scenario is to monitor the coastline of a large lake so as to ensure that no people can go through its perimeter intentionally or accidentally. Another application scenario is to monitor the wall of a prison so as to ensure that no criminal can escape easily by digging holes through the wall. Therefore, perimeter monitoring is an important problem.
In [1–4], we studied how to identify a set of sensors to cover the perimeter of a large object with the minimum size and minimum cost. Since sensors are battery-powered and the battery is unlikely to be rechargeable, every sensor network has a functional network lifetime. In this work, we are particularly interested in how to schedule the sensors so as to maximize the network lifetime in the perimeter coverage problem. To the best of our knowledge, the lifetime maximization issue in the perimeter coverage problem was first studied in [5]. In [5], we adopted several heuristic energy-related scheduling objectives as cost metrics. Different sets of sensors are identified using these objectives to monitor the target at different times. The energy-related objectives include the minimization of energy of each sensor set found, the minimization of the battery cost which is defined as the reciprocal of the remaining battery capacity of the sensor, the hybrid algorithm, and so forth. The heuristic scheduling algorithms developed based on the adoption of different energy-related objectives are then compared through extensive simulations.
Unlike that of [5], in this paper, we study the problem from the theoretical perspective and make the following contributions: (1) We formally prove that the perimeter coverage problem is NP-hard in general, but polynomial time solution exists in some special cases. (2) We identify the sufficient conditions for a perimeter coverage scheduling algorithm to be a  -approximation solution. (3) We develop a distributed scheduling algorithm that generates
-approximation solution. (3) We develop a distributed scheduling algorithm that generates  (size of the minimum cover) number of messages. The schedules generated must have a lifetime that is at least half of the optimal one. (4) We simulate the proposed algorithm and compare it with the optimal schedules.
(size of the minimum cover) number of messages. The schedules generated must have a lifetime that is at least half of the optimal one. (4) We simulate the proposed algorithm and compare it with the optimal schedules.
The paper is organized as follows. Section 2 discusses the related work on the other coverage problems. Section 3 describes the notations, problem statement, and the properties of the problem. Section 4 studies the special cases in which polynomial time optimal solutions exist. A formal proof of NP-hardness of this problem in general is given in Section 5. The sufficient condition for a perimeter coverage scheduling algorithm to be a  -approximation solution is discussed in Section 6. Our proposed distributed
-approximation solution is discussed in Section 6. Our proposed distributed  -approximation solution which requires
-approximation solution which requires  (size of the minimum cover) number of messages is also described. Section 7 presents the simulation results of our proposed algorithm by comparing it with the optimal schedules. Finally, we conclude our work with some of the future directions in Section 8.
(size of the minimum cover) number of messages is also described. Section 7 presents the simulation results of our proposed algorithm by comparing it with the optimal schedules. Finally, we conclude our work with some of the future directions in Section 8.
2. Related Work
Extensive research has been carried out to extend the lifetime of sensor networks [6–8]. In this study, network lifetime is defined as the length of the time period that the target area or target objects are being covered continuously. One way to extend network lifetime is to schedule the sensor nodes' activities to alternate between active and sleep modes so that only a minimal number of sensors are turned on at any time [9]. Tian and Georganas [10] propose a distributed scheduling algorithm which turns off the sensors with a cover area completely replaceable by the cover areas of their neighboring nodes. Yan et al. [11] adopt a similar concept. However, instead of considering whether the sensing area of a sensor is covered by its neighbors, the sensor considers a certain number of grid points inside the area. Later, Hsin and Liu [12] propose a randomized algorithm and a coordinated algorithm so as to schedule the sleeping times of the nodes. In the randomized algorithm, a sensor will sleep with a certain probability. In the coordinated algorithm, a sensor will sleep only when its sensing area is completely covered by others. On the other hand, Huang and Tseng [13] study the criteria for determining whether the sensing area of a sensor is covered by  different sensors simultaneously. Huang et al. [14] propose several decentralized energy-conserving and coverage-preserving protocols so as to solve the
different sensors simultaneously. Huang et al. [14] propose several decentralized energy-conserving and coverage-preserving protocols so as to solve the  area coverage problem. Other than those suggested above which aim at full area coverage, the fractional coverage problem, in which only a certain fraction of the target area has to be covered, has also been considered in [15]. In [15], Ye et al. first calculate the ideal density for providing a certain fraction of coverage. Then, each sensor is activated with a probability. This probability is determined based on the ratio between the current density and the ideal density calculated. On the contrary, Wang and Kulkarni [16] investigate similar problem in another direction, and they show that sacrificing a certain fraction of the target area can significantly increase the network lifetime. Ren et al. [17] study the relationship between the fraction of coverage and the quality of the object detection capability. As a result, the network can be deployed with a fraction of coverage that can achieve an acceptable quality.
area coverage problem. Other than those suggested above which aim at full area coverage, the fractional coverage problem, in which only a certain fraction of the target area has to be covered, has also been considered in [15]. In [15], Ye et al. first calculate the ideal density for providing a certain fraction of coverage. Then, each sensor is activated with a probability. This probability is determined based on the ratio between the current density and the ideal density calculated. On the contrary, Wang and Kulkarni [16] investigate similar problem in another direction, and they show that sacrificing a certain fraction of the target area can significantly increase the network lifetime. Ren et al. [17] study the relationship between the fraction of coverage and the quality of the object detection capability. As a result, the network can be deployed with a fraction of coverage that can achieve an acceptable quality.
Cardei et al. [18] study the target coverage problem where a target object has to be monitored by at least one sensor at any moment and each sensor can monitor multiple target objects if the objects fall within the sensor's sensing area. They formulate this target coverage problem as a set coverage problem, and propose both centralized approximation and distributed heuristic solutions. In [19], Liu et al. study similar problem. However, they assume that each sensor can only monitor one target object at any moment even if multiple targets fall within the sensing area of a sensor. Unfortunately, the cover formed by using these approaches may not be connected as some nodes in the cover may not have any route back to the sink node. Therefore, Zhao and Gurusamy [20] further investigate the connected target coverage problem. They prove that this problem is NP-complete, and develop a centralized approximation solution and a distributed heuristic solution. Thai et al. [21] propose an  -approximation distributed algorithm to solve the target coverage problem, where
-approximation distributed algorithm to solve the target coverage problem, where  denotes the number of sensors in the network. They organize the sensors into nondisjoint cover sets in which each set can cover all the target objects with high probability. They formally show that their solution is an
denotes the number of sensors in the network. They organize the sensors into nondisjoint cover sets in which each set can cover all the target objects with high probability. They formally show that their solution is an  approximation solution if the initial battery capacity of all the sensors is the same, but the approximation ratio is worsen if the initial battery capacity of the sensors is different. On the other hand, Calines and Ellis [22] suggest an
approximation solution if the initial battery capacity of all the sensors is the same, but the approximation ratio is worsen if the initial battery capacity of the sensors is different. On the other hand, Calines and Ellis [22] suggest an  -approximation algorithm. Their solution achieves the same approximation ratio no matter the initial battery capacity of all the sensors is the same or not. Unfortunately, these algorithms cannot guarantee that all the targets are covered all the time.
-approximation algorithm. Their solution achieves the same approximation ratio no matter the initial battery capacity of all the sensors is the same or not. Unfortunately, these algorithms cannot guarantee that all the targets are covered all the time.
Another related problem is the barrier coverage problem. In [23], Kumar et al. consider the  barrier coverage problem. They assume that an intruder can be detected by a sensor if it falls within its sensing area. They consider the scenario in which an intruder will be detected by at least
barrier coverage problem. They assume that an intruder can be detected by a sensor if it falls within its sensing area. They consider the scenario in which an intruder will be detected by at least  sensors if she goes through a thin strip of area (known as belt) no matter where her start point and her end point are. In [23], Kumar et al. propose a polynomial time mechanism to determine whether there exists
sensors if she goes through a thin strip of area (known as belt) no matter where her start point and her end point are. In [23], Kumar et al. propose a polynomial time mechanism to determine whether there exists  barrier coverage. On the other hand, Kumar et al. [24] study the optimal sleeping schedule on the
barrier coverage. On the other hand, Kumar et al. [24] study the optimal sleeping schedule on the  barrier coverage problem. They transform the problem to a maximum flow problem so that it can be solved optimally in a centralized manner. Chen et al. further propose a localized algorithm in [25]. They first study the critical conditions for the existence of
barrier coverage problem. They transform the problem to a maximum flow problem so that it can be solved optimally in a centralized manner. Chen et al. further propose a localized algorithm in [25]. They first study the critical conditions for the existence of  barrier coverage locally. The sensor can then turn into sleep mode when it determines that
barrier coverage locally. The sensor can then turn into sleep mode when it determines that  barrier coverage can be provided by its neighbors. Chen et al. further study how to find and measure the quality of
barrier coverage can be provided by its neighbors. Chen et al. further study how to find and measure the quality of  barrier coverage accurately in [26]. Later, Liu et al. [27] discover that it may not be possible to guarantee
barrier coverage accurately in [26]. Later, Liu et al. [27] discover that it may not be possible to guarantee  barrier coverage by using the approach in [25] under some special situations. They identify the critical conditions for the existence of a strong barrier coverage and devise an efficient technique to guarantee
barrier coverage by using the approach in [25] under some special situations. They identify the critical conditions for the existence of a strong barrier coverage and devise an efficient technique to guarantee  coverage. Other than that, Saipulla et al. [28] study the barrier coverage problem where the sensors are dropped from air. They suggest that the sensors are deployed along a line with a certain offset by using this deployment strategy. They show that the performance achievable by using this method is much better than that of using the random deployment strategy which is generally assumed in most of the literatures.
coverage. Other than that, Saipulla et al. [28] study the barrier coverage problem where the sensors are dropped from air. They suggest that the sensors are deployed along a line with a certain offset by using this deployment strategy. They show that the performance achievable by using this method is much better than that of using the random deployment strategy which is generally assumed in most of the literatures.
3. Notations, Problem Statement, and Properties
We assume that the object is a very big one and we want the whole perimeter to be monitored continuously. Each sensor has a certain sensing range. It can monitor a point such that the distance between the point and the sensor is less than or equal to the sensing range. The area that the sensor can monitor, called sensing area, is a circle. The object that falls within the sensing area of a sensor is said to be monitored by the sensor. It is assumed that each sensor can only monitor a single continuous portion of the perimeter, and no sensor can monitor the whole perimeter as shown in Figure 1. Sensors are randomly distributed around the big object. The set of sensors that can cover a portion of the target object is denoted as  . Also, we use
. Also, we use  to denote the number of sensors in
to denote the number of sensors in  , that is,
, that is,  .
.
3.1. Cover Range, Proper Set of Sensors, and General Set of Sensors
Cover range is defined as the portion of the perimeter of the target object covered by the sensing area of a sensor node. In this paper, we represent the cover range in terms of angular measurement for the ease of discussion. It is worth noting that the perimeter of the target object can be in any irregular shape as long as it forms a loop, a sensor only has a single continuous cover range, and the sensor can determine its cover range. Note that under some extreme conditions, the assumption that each sensor only has a single continuous cover range may not be valid, such as, the target object contains a sharp convex or concave shape on the perimeter. In this case, the sensor has multiple cover ranges instead [29]. This makes the problem a lot more complicated, and we leave it as future work. On the other hand, how a sensor determines the range is application dependent, and is outside the scope of this paper. Interested readers are referred to [30–32].
We denote the cover range of a sensor node  as
as  as shown in Figure 1. We refer to
as shown in Figure 1. We refer to  as the start angle and
as the start angle and  as the end angle.
as the end angle.  for most
for most  . Sensor
. Sensor  that covers
that covers  would have
would have  . We denote the set of sensors that cover
. We denote the set of sensors that cover  as
as  .
.
 is a proper set of sensors if
is a proper set of sensors if  ,
,  , such that
, such that  or
or  . In other words,
. In other words,  is a proper set of sensors if none of the sensors has cover range containing or contained inside another sensor. Otherwise,
is a proper set of sensors if none of the sensors has cover range containing or contained inside another sensor. Otherwise,  is known as a general set of sensors. As an example, the set of sensors shown in Figure 4 is a proper set of sensors. On the other hand, the set of sensors shown in Figure 2 is a general set of sensors.
is known as a general set of sensors. As an example, the set of sensors shown in Figure 4 is a proper set of sensors. On the other hand, the set of sensors shown in Figure 2 is a general set of sensors.
3.2. Cover, Proper Cover, and Mutually Disjoint Cover Set
A set  is a cover if for each angle
is a cover if for each angle  , there exists a sensor
, there exists a sensor  in
in  such that
such that  . In other words,
. In other words,  . Figure 2 illustrates a scenario of 9 sensors surrounding a target object. Each arrow represents the cover range of a node.
. Figure 2 illustrates a scenario of 9 sensors surrounding a target object. Each arrow represents the cover range of a node.  ,
,  , and
, and  are all covers.
are all covers.
A proper cover is a cover that every sensor is essential for the coverage. That is, if  is a proper cover, then
is a proper cover, then  ∖
∖ is not a cover for any
is not a cover for any  . For instance,
. For instance,  and
and  are proper covers in Figure 2.
are proper covers in Figure 2.
Suppose  and
and  are two covers. We say
are two covers. We say  and
and  are mutually disjoint if
are mutually disjoint if  . A set of covers Ϝ is a mutually disjoint cover set if any arbitrary pair of covers inside
. A set of covers Ϝ is a mutually disjoint cover set if any arbitrary pair of covers inside  are mutually disjoint. Formally, for any
are mutually disjoint. Formally, for any  ,
,  . Refering to Figure 4,
. Refering to Figure 4,  can be
can be  .
.
3.3. Sensor Lifetime—Uniform and Nonuniform, Schedule, Network Lifetime, and Problem Statement
We adopt the cycle-based scheduling mechanism as in [33, 34]. In other words, a cover is selected to monitor the target object in each cycle, and the duration of each cycle is the same. The sensor lifetime of a sensor  ,
,  , is the number of cycles it can be turned on. If
, is the number of cycles it can be turned on. If  for all
for all  , we say that the sensors have uniform battery. Otherwise, they have nonuniform battery.
, we say that the sensors have uniform battery. Otherwise, they have nonuniform battery.
In each cycle, a set of sensors is turned on to monitor the target. Those sensors that are not in the set can switch to sleep mode to conserve energy. A schedule defines the cycles in which a sensor has to be turned on or off. We use a matrix  of size
of size  to represent the schedule.
to represent the schedule.  means Sensor
means Sensor  should be turned on at cycle
should be turned on at cycle  ;
;  otherwise. With the definition of the schedule, network lifetime
otherwise. With the definition of the schedule, network lifetime refers to the number of cycles that the perimeter of the target can be monitored continuously according to the schedule
refers to the number of cycles that the perimeter of the target can be monitored continuously according to the schedule  . Note that different schedules will result in different network lifetimes. An optimal scheduling algorithm finds a schedule
. Note that different schedules will result in different network lifetimes. An optimal scheduling algorithm finds a schedule  such that the maximum network lifetime
such that the maximum network lifetime  on a set of sensors
on a set of sensors  can be achieved. In other words, no scheduling algorithm can find a schedule
can be achieved. In other words, no scheduling algorithm can find a schedule  which can achieve a network lifetime
which can achieve a network lifetime  on
on  .
.
Therefore, the objective of the scheduling problem is to find a schedule  to monitor the target object continuously so that the lifetime
to monitor the target object continuously so that the lifetime  is maximized. Formally, we would like to find an
is maximized. Formally, we would like to find an  which maximizes
which maximizes  , such that
, such that  ,
,  , where
, where  .
.
3.4. Neighbors, Backward Neighbors, and Forward Neighbors
If two nodes' cover ranges overlap, they are neighbors. Formally,  and
and  are neighbors if
are neighbors if  or
or  (This applies when both
(This applies when both  and
and  do not cover
do not cover  . The definition can be extended easily to ranges that cover
. The definition can be extended easily to ranges that cover  but we leave it out for the ease of discussion.). We assume that a node can only communicate with its neighbors. It is possible that
but we leave it out for the ease of discussion.). We assume that a node can only communicate with its neighbors. It is possible that  completely contains
completely contains  , such as Sensors
, such as Sensors  and
and  in Figure 2. When two sensors have overlapping cover ranges and none of them is contained in the other, one of them is a backward neighbor and the other is a forward neighbor.
in Figure 2. When two sensors have overlapping cover ranges and none of them is contained in the other, one of them is a backward neighbor and the other is a forward neighbor.  is a backward neighbor of
is a backward neighbor of  and
and  is a forward neighbor of
is a forward neighbor of  if
if  . Refer to Figure 2, Sensors
. Refer to Figure 2, Sensors  and
and  are forward neighbors of Sensor
are forward neighbors of Sensor  , while Sensors
, while Sensors  and
and  are backward neighbors of Sensor
are backward neighbors of Sensor  .
.
3.5. Perimeter Segment and Properties of the Problem
An endpoint can be any start angle  or end angle
or end angle  of any sensor
of any sensor  . Suppose all the endpoints are distinct, there are
. Suppose all the endpoints are distinct, there are  endpoints formed by
endpoints formed by  sensors in the network. We denote each endpoint as
sensors in the network. We denote each endpoint as  where
where  in ascending order. Figure 3 illustrates the endpoints of the sensors in Figure 2. The perimeter segment is the portion of the perimeter of the target object formed by a pair of consecutive endpoints
in ascending order. Figure 3 illustrates the endpoints of the sensors in Figure 2. The perimeter segment is the portion of the perimeter of the target object formed by a pair of consecutive endpoints  , where
, where  . When
. When  , the perimeter segment is
, the perimeter segment is  . We denote
. We denote  as the segment
as the segment  as shown in Figure 3. Now, we use
as shown in Figure 3. Now, we use  to denote the set of all perimeter segments formed by consecutive endpoints, that is,
to denote the set of all perimeter segments formed by consecutive endpoints, that is,  . Since
. Since  , if
, if  covers
covers  ,
,  , then
, then  is a cover. Similarly, if
is a cover. Similarly, if  is a cover, it covers all
is a cover, it covers all  .
.
Since  covers all
covers all  if and only if
if and only if  covers [
covers [ ), an upper bound of the lifetime of covering
), an upper bound of the lifetime of covering  can be derived. To start the discussion, we further define some terms as follows and we use the example in Figure 3 to explain them. For the ease of discussion, we use
can be derived. To start the discussion, we further define some terms as follows and we use the example in Figure 3 to explain them. For the ease of discussion, we use  ,
,  in the examples.
in the examples.
-
(i)
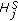 denotes the set of sensors in
denotes the set of sensors in  which cover
which cover  . Formally,
. Formally, 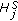 =
= 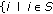 covers
covers  . For instance,
. For instance,  . We further let
. We further let 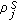 denote
denote 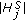 . For instance,
. For instance, 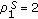 .
. -
(ii)
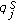 denotes the total number of energy cycles of the sensors in
denotes the total number of energy cycles of the sensors in 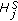 . Formally,
. Formally, 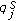 =
= 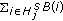 . For instance,
. For instance, 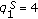 since
since 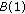 +
+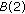 =
= 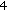 .
. -
(iii)
 denotes the
denotes the 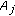 with the minimum
with the minimum 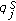 . Formally,
. Formally,  =
= 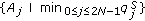 , for example,
, for example, 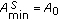 .
. -
(iv)
 =
= 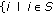 covers
covers 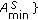 ,
, 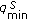 =
=  , and
, and  =
=  . For instance,
. For instance, 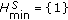 ,
, 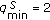 , and
, and 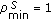 .
.
We now prove that the maximum achievable lifetime of sensor set  (
( ) is upper bounded by
) is upper bounded by  .
.
Property 1.
 .
.
Proof.
Suppose  . In each cycle, at least one sensor
. In each cycle, at least one sensor  is selected to cover
is selected to cover  . Since each sensor
. Since each sensor  can be activated at most
can be activated at most  units of time,
units of time,  is at most covered
is at most covered  units of time. Afterwards,
units of time. Afterwards,  cannot be covered by any sensor. Therefore, this leads to the contradiction that
cannot be covered by any sensor. Therefore, this leads to the contradiction that  .
.
When all the sensors have the same initial battery  ,
,  . Therefore, in the uniform battery case, Property 1 can naturally be extended to Property 2.
. Therefore, in the uniform battery case, Property 1 can naturally be extended to Property 2.
Property 2.
If  , then
, then  .
.
4. Proper Set of Sensors
In this section, we describe how to find a schedule when  is a proper sensor set, such that there is no sensor whose cover range is contained inside another sensor. We consider two scenarios: uniform battery scenario and nonuniform battery scenario. In the following, we drop the superscript
is a proper sensor set, such that there is no sensor whose cover range is contained inside another sensor. We consider two scenarios: uniform battery scenario and nonuniform battery scenario. In the following, we drop the superscript  in notations for simplicity if the context is clear.
in notations for simplicity if the context is clear.
4.1. Uniform Battery Scenario
In this scenario, by Property 2, the maximum lifetime  . Hence, if there exists a mutually disjoint cover set
. Hence, if there exists a mutually disjoint cover set  where
where  , an optimal schedule can be found by activating each cover
, an optimal schedule can be found by activating each cover  for
for  cycles. We consider two cases: (1)
cycles. We consider two cases: (1)  ; (2)
; (2)  .
.
(1)  : in this case, we can find a mutually disjoint cover set
: in this case, we can find a mutually disjoint cover set  with exactly
with exactly  covers and each cover has exactly
covers and each cover has exactly  number of sensors. To find these covers, we first label the nodes in
number of sensors. To find these covers, we first label the nodes in  in the clockwise manner where the most anti-clockwise sensor in
in the clockwise manner where the most anti-clockwise sensor in  is labeled as
is labeled as  . In Figure 4,
. In Figure 4,  and so
and so  is Sensor
is Sensor  . Let
. Let  ,
,  ,
, ,
,  be subsets of
be subsets of  where
where  . On the other hand, a collection of
. On the other hand, a collection of  , where
, where  , is denoted as
, is denoted as  . Refering to Figure 4, a mutually disjoint cover set
. Refering to Figure 4, a mutually disjoint cover set  with
with  covers is formed. We show that
covers is formed. We show that  is a mutually disjoint cover set with
is a mutually disjoint cover set with  covers by the following property and lemma.
covers by the following property and lemma.
Property 3.
If  is proper,
is proper,  is a backward neighbor of
is a backward neighbor of  .
.
Proof.
Let the start angle and end angle of sensor  be
be  and
and  , respectively. Let
, respectively. Let  . Suppose
. Suppose  is not the backward neighbor of
is not the backward neighbor of  where
where  . This implies that
. This implies that  as
as  and
and  do not overlap in terms of sensing range. Since
do not overlap in terms of sensing range. Since  is covered by
is covered by  sensors, we know that the range
sensors, we know that the range  (which may be a union of several perimeter segments) must be covered by at least
(which may be a union of several perimeter segments) must be covered by at least  sensors. In this case,
sensors. In this case,  is covered by Sensors
is covered by Sensors  ,
, ,
, . It implies that
. It implies that  is only covered by
is only covered by  sensors. This contradicts to the definition of
sensors. This contradicts to the definition of  . Therefore,
. Therefore,  is a backward neighbor of
is a backward neighbor of  .
.
Lemma 1.
If  , then
, then  forms a mutually disjoint cover set with
forms a mutually disjoint cover set with  covers.
covers.
Proof.
By Property 3, we know that  is the backward neighbor of
is the backward neighbor of  . Similarly,
. Similarly,  is the backward neighbor of
is the backward neighbor of  , and so on. Since
, and so on. Since  is divisible by
is divisible by  , for each
, for each  , the last member is
, the last member is  . By Property 3,
. By Property 3,  is the backward neighbor of
is the backward neighbor of  . This implies that every
. This implies that every  , where
, where  , forms a cover. As a result,
, forms a cover. As a result,  covers are formed. On the other hand, a sensor in
covers are formed. On the other hand, a sensor in  falls into exactly one of the
falls into exactly one of the  , where
, where  . Therefore,
. Therefore,  forms a mutually disjoint cover set with
forms a mutually disjoint cover set with  covers.
covers.
The direct consequence of Lemma 1 is that the maximum lifetime schedule can be achieved by activating each cover  , where
, where  , for
, for  units of time and the corresponding lifetime is
units of time and the corresponding lifetime is  .
.
(2)  : in this case, Lemma 1 cannot be directly applied to
: in this case, Lemma 1 cannot be directly applied to  . Refering to Figure 5, if we set
. Refering to Figure 5, if we set  , then
, then  ,
,  , and
, and  . However,
. However,  is not a cover. To solve the problem, one possible way is to split
is not a cover. To solve the problem, one possible way is to split  into
into  with
with  sensors and
sensors and  with
with  sensors such that
sensors such that  and
and  and
and  . Then, Lemma 1 can be applied to
. Then, Lemma 1 can be applied to  and
and  individually to form two corresponding mutually disjoint cover sets, denoted as
individually to form two corresponding mutually disjoint cover sets, denoted as  and
and  , with
, with  covers and
covers and  covers, respectively. Refering back to Figure 5, two mutually disjoint cover sets with
covers, respectively. Refering back to Figure 5, two mutually disjoint cover sets with  covers in total do exist. Suppose the broken arcs are sensors in
covers in total do exist. Suppose the broken arcs are sensors in  , that is,
, that is,  . On the other hand, solid arcs are sensors in
. On the other hand, solid arcs are sensors in  , that is,
, that is,  . In this case, we set
. In this case, we set  in
in  and
and  in
in  . Hence,
. Hence,  where
where  and
and  .
.  where
where  . Finally,
. Finally,  forms a mutually disjoint cover set with
forms a mutually disjoint cover set with  covers in total.
covers in total.
However, let us consider Figure 6. In this example, the maximum network lifetime is  if
if  ,
,  units. This can be achieved by activating the sets
units. This can be achieved by activating the sets  ,
,  , and
, and  , each for
, each for  time unit. In this example, although we know that
time unit. In this example, although we know that  , there is no way for us to find
, there is no way for us to find  and
and  such that
such that  . Instead, we can only identify a single mutually disjoint cover set that contains one cover. By activating this only cover, the achievable network lifetime is
. Instead, we can only identify a single mutually disjoint cover set that contains one cover. By activating this only cover, the achievable network lifetime is  units. Hence, we can conclude that when we cannot find a mutually disjoint cover set with exactly
units. Hence, we can conclude that when we cannot find a mutually disjoint cover set with exactly  covers using the sensor partitioning method, we cannot be sure we have an optimal solution. This implies that even if we can find a mutually disjoint cover set with
covers using the sensor partitioning method, we cannot be sure we have an optimal solution. This implies that even if we can find a mutually disjoint cover set with  covers, the set found may not be an optimal solution as shown in the example in Figure 6. The sensor partitioning problem aforementioned can be transformed to a shortest path problem and solved with the time complexity of
covers, the set found may not be an optimal solution as shown in the example in Figure 6. The sensor partitioning problem aforementioned can be transformed to a shortest path problem and solved with the time complexity of  . We refer readers for details in [35, 36].
. We refer readers for details in [35, 36].
4.2. Nonuniform Battery Scenario
In the nonuniform battery scenario, it is possible to transform  into a sensor set
into a sensor set  such that all sensors have the same initial battery. For every
such that all sensors have the same initial battery. For every  with
with  units of battery and with the cover range
units of battery and with the cover range  , we put
, we put  sensors in
sensors in  , each with
, each with  unit of battery and cover range
unit of battery and cover range  . Then, the maximum achievable lifetime on
. Then, the maximum achievable lifetime on  is the same as the maximum achievable lifetime on
is the same as the maximum achievable lifetime on  . However,
. However,  is no longer a proper set since all the sensors we put in
is no longer a proper set since all the sensors we put in  based on
based on  share the same cover range. Figure 7 illustrates an example of the transformation with
share the same cover range. Figure 7 illustrates an example of the transformation with  . The next section studies how to find a schedule when the sensor set is not proper.
. The next section studies how to find a schedule when the sensor set is not proper.
5. General Set of Sensors
In this section, we would like to prove that the perimeter coverage scheduling problem is NP-hard if  is a general set of sensors. We first consider the situation where
is a general set of sensors. We first consider the situation where  ,
,  . To prove the perimeter coverage scheduling problem is NP-hard, a reduction is constructed from the
. To prove the perimeter coverage scheduling problem is NP-hard, a reduction is constructed from the  -coloring problem on a circular-arc graph, which was first shown to be NP-hard in [37], to the perimeter coverage scheduling problem. Here,
-coloring problem on a circular-arc graph, which was first shown to be NP-hard in [37], to the perimeter coverage scheduling problem. Here,  denotes a perimeter scheduling problem instance with a set of sensors
denotes a perimeter scheduling problem instance with a set of sensors  , and the maximum lifetime achievable on
, and the maximum lifetime achievable on  is
is  .
.
Before we go into details about the transformation, we first describe the  -coloring problem on a circular arc graph
-coloring problem on a circular arc graph  . A circular arc
. A circular arc  in
in  is denoted as
is denoted as  , where
, where  denotes the anti-clockwise endpoint, and
denotes the anti-clockwise endpoint, and  denotes the clockwise endpoint of a circular arc. In other words, a circular arc is open on the clockwise endpoint. We further assume that all the endpoints are distinct. Arcs
denotes the clockwise endpoint of a circular arc. In other words, a circular arc is open on the clockwise endpoint. We further assume that all the endpoints are distinct. Arcs  and
and  are neighbors if the arcs overlap. In the
are neighbors if the arcs overlap. In the  -coloring problem, we would like to determine whether
-coloring problem, we would like to determine whether  colors are enough to assign a color to each arc such that no two neighbor arcs share the same color.
colors are enough to assign a color to each arc such that no two neighbor arcs share the same color.
We further introduce some notations so as to define the problem formally. Here, we use  to denote the number of circular arcs in
to denote the number of circular arcs in  . Therefore, there are
. Therefore, there are  endpoints in
endpoints in  . We sort the endpoints in ascending order, and denote them as
. We sort the endpoints in ascending order, and denote them as  , where
, where  . A pair of consecutive endpoints
. A pair of consecutive endpoints  are denoted as
are denoted as  . We use
. We use  to denote the set of arcs covering
to denote the set of arcs covering  , that is,
, that is,  ,
,  . Let
. Let  denote the set of circular arcs with Color
denote the set of circular arcs with Color  . Since the sensors in
. Since the sensors in  are neighbors of each other, at least
are neighbors of each other, at least  colors are needed.
colors are needed.
Given any instance  of the
of the  -coloring problem in the circular arc graph, where
-coloring problem in the circular arc graph, where  is an integer larger than or equal to
is an integer larger than or equal to  , an instance
, an instance  of the perimeter coverage scheduling problem can be constructed from
of the perimeter coverage scheduling problem can be constructed from  as follows.
as follows.
-
(1)For
each
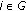 , put Sensor
, put Sensor 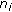 in
in 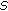 and the cover range of
and the cover range of 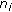 is
is  .
. -
(2)
 ,
, 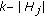 sensors with cover range of
sensors with cover range of  are put in
are put in  . These sensors are named with
. These sensors are named with  , where
, where  .
. -
(3)
 ,
, 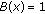 .
.
Consider Arcs  ,
, ,
, in Figure 8; Sensors
in Figure 8; Sensors  ,
, ,
, are put into
are put into  according to (1) in Figure 9. Suppose
according to (1) in Figure 9. Suppose  = 3. Consider the range
= 3. Consider the range  ; according to (2), Sensor
; according to (2), Sensor  is put in
is put in  . Similarly, Sensors
. Similarly, Sensors  ,
,  ,
,  ,
,  ,
,  ,
,  ,
,  ,
,  ,
,  ,
,  ,
,  , and
, and  are put into
are put into  as shown in Figure 9. As a result, we know that
as shown in Figure 9. As a result, we know that  . Since
. Since  ,
,  . Therefore,
. Therefore,  .
.
Lemma 2.
 is
is  -colorable if and only if the maximum lifetime on
-colorable if and only if the maximum lifetime on  is
is  .
.
Proof.
"⇒" part: if  is
is  -colorable, we can put the arcs into
-colorable, we can put the arcs into  different partitions
different partitions  according to their colors. We show that
according to their colors. We show that  covers
covers  can be formed in
can be formed in  by using the following approach:
by using the following approach:
-
(1)
if
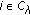 ,
, 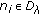 .
. -
(2)
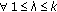 ,
, 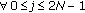 , if there is no sensor in
, if there is no sensor in 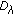 which can cover
which can cover  , then we can randomly select a sensor
, then we can randomly select a sensor 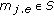 , where
, where 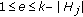 , with cover range
, with cover range 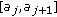 into
into  to cover
to cover  . Recall that there are
. Recall that there are 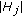 arcs in
arcs in 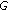 covering
covering 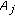 and these arcs must fall into
and these arcs must fall into 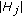 different colors, that is, different partitions. Since we have constructed
different colors, that is, different partitions. Since we have constructed 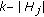 sensors with cover range
sensors with cover range 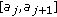 in
in  , if there is no sensor in
, if there is no sensor in 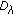 which can cover
which can cover 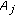 , then we can always find a sensor
, then we can always find a sensor 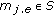 , where
, where 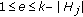 , with cover range
, with cover range 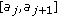 to put into
to put into  .
.
The corresponding  formed,
formed,  , are covers, because
, are covers, because  ; there is a sensor in
; there is a sensor in  covering
covering  . At the same time,
. At the same time,  ,
,  . Therefore,
. Therefore,  , for any
, for any  . Since
. Since  is
is  and
and  , by Property 2, the maximum lifetime
, by Property 2, the maximum lifetime  is upper bounded by
is upper bounded by  . Hence, the maximum lifetime
. Hence, the maximum lifetime  can be achieved by activating each cover for
can be achieved by activating each cover for  unit of time. This results in
unit of time. This results in  . Therefore, if
. Therefore, if  is
is  -colorable, then the maximum lifetime on
-colorable, then the maximum lifetime on  is
is  .
.
" " part: If the maximum lifetime
" part: If the maximum lifetime  on
on  is
is  and the corresponding schedule is
and the corresponding schedule is  , then there must exist a mutually disjoint cover set with
, then there must exist a mutually disjoint cover set with  covers since each sensor has a battery lifetime of
covers since each sensor has a battery lifetime of  unit. Without loss of generality, these
unit. Without loss of generality, these  covers are
covers are  . In other words,
. In other words,  and
and  , where
, where  .
.
Hence, with the existence of  covers,
covers,  partitions
partitions  on
on  can be formed by the following approach:
can be formed by the following approach:
 ,
,  ,
,  . Note that we do not need to consider the sensors
. Note that we do not need to consider the sensors  in
in  , where
, where  and
and  .
.
Since  is constructed in such a way that every
is constructed in such a way that every  , where
, where  , is exactly covered by
, is exactly covered by  sensors, if there exist
sensors, if there exist  covers, then every
covers, then every  is exactly covered by
is exactly covered by  sensor in each cover. Therefore, by constructing
sensor in each cover. Therefore, by constructing  ,
,  , according to the above description, neighbor arcs must fall into different color partitions. As a result,
, according to the above description, neighbor arcs must fall into different color partitions. As a result,  ,
,  , forms a color partition and so
, forms a color partition and so  is
is  -colorable if the maximum lifetime on
-colorable if the maximum lifetime on  is
is  .
.
By Lemma 2, Theorem 1 can then be developed.
Theorem 1.
The perimeter coverage scheduling problem is NP-hard.
6. Approximation Solutions
Since the perimeter coverage problem is NP-hard, it is not likely to have a polynomial time solution. The problem can be formulated as a mixed integer programming problem, and solved by some existing software. However, a centralized approach is not appropriate. Therefore, we develop a distributed approximation solution with a small overhead. Before describing our algorithm, we first show that any scheduling algorithm that selects a proper cover in each cycle is a  -approximation algorithm.
-approximation algorithm.
6.1. Properties of Proper Covers
Property 4.
In a proper cover, there are at most two sensors covering  for each
for each  .
.
Proof.
Suppose  all cover range
all cover range  , and the cover ranges of
, and the cover ranges of  ,
,  , and
, and  are
are  ,
,  , and
, and  , respectively. Without loss of generality, we assume
, respectively. Without loss of generality, we assume  . In this case,
. In this case,  . This contradicts to the definition of proper cover as
. This contradicts to the definition of proper cover as  is redundant.
is redundant.
Property 4 says that each portion on the perimeter is at most covered by  sensors in a proper cover. Lemma 3 shows that any scheduling algorithm which selects a proper cover to monitor the target object in each cycle is a
sensors in a proper cover. Lemma 3 shows that any scheduling algorithm which selects a proper cover to monitor the target object in each cycle is a  -approximation solution.
-approximation solution.
Lemma 3.
Suppose  is the schedule which selects a proper cover in each cycle.
is the schedule which selects a proper cover in each cycle.  has a lifetime
has a lifetime  , where
, where  is the maximum lifetime on
is the maximum lifetime on  .
.
Proof.
We use  to denote the remaining energy of Sensor
to denote the remaining energy of Sensor  after cycle
after cycle  . At the beginning,
. At the beginning,  ,
,  . We further use the term
. We further use the term  to denote
to denote  covers
covers  . That is,
. That is,  covers
covers  and
and  . By Property 4, at most
. By Property 4, at most  sensors cover
sensors cover  in cycle
in cycle  . In fact, this implies that
. In fact, this implies that  if
if  sensors are required to cover
sensors are required to cover  in each cycle
in each cycle  ,
,  . Note that this is the worst possible case for the selection of a proper cover in each cycle as
. Note that this is the worst possible case for the selection of a proper cover in each cycle as  is covered by sensors with the least total amount of energy cycle. Here, we assume
is covered by sensors with the least total amount of energy cycle. Here, we assume  . Therefore,
. Therefore,  if
if  is even and
is even and  if
if  is odd. In case
is odd. In case  is odd, all the sensors can be activated in the last unit of time. This is possible as
is odd, all the sensors can be activated in the last unit of time. This is possible as  . Since
. Since  ,
,  .
.
All the heuristic algorithms we proposed in [5] identify a proper cover in each cycle. By Lemma 3, we know that all of them are 2-approximation solutions if no message transmission cost is considered. Unfortunately, these approaches have very high message overheads. It may require  minimum size of cover
minimum size of cover  size of
size of  number of messages during the whole network lifetime, where
number of messages during the whole network lifetime, where  denotes the set of sensors with cover range passing through
denotes the set of sensors with cover range passing through  .
.
6.2. Our Proposed 2-Approximation Algorithm
To reduce message overhead, our approximation algorithm identifies as many proper covers as possible by circulating messages around the sensors once. This can be done by using a similar method suggested in [3], which will be discussed later in this section. In the uniform battery case, we try to find a mutually disjoint cover set with as many proper covers as possible. Then, each proper cover can be activated for  units of time. On the other hand, in the nonuniform battery scenario, each sensor with
units of time. On the other hand, in the nonuniform battery scenario, each sensor with  units of battery is transformed to
units of battery is transformed to  sensors with
sensors with  unit each similar to that discussed in Section 4.2, and thus the battery of the transformed set of sensors becomes uniform. Then, we try to find a mutually disjoint cover set with as many proper covers as possible and each cover is activated for
unit each similar to that discussed in Section 4.2, and thus the battery of the transformed set of sensors becomes uniform. Then, we try to find a mutually disjoint cover set with as many proper covers as possible and each cover is activated for  unit of time.
unit of time.
Note that although the uniform battery case is discussed here, the suggested algorithm can be extended to the nonuniform battery case easily. Basically, our proposed algorithm works as follows. A message is passed around the sensors in the clockwise direction. A sensor passing through  creates the message. The message contains information for constructing mutually disjoint covers. When a sensor receives the message, it is responsible for filling in the information and passes it to a neighbor sensor. When the message is received by another sensor passing through
creates the message. The message contains information for constructing mutually disjoint covers. When a sensor receives the message, it is responsible for filling in the information and passes it to a neighbor sensor. When the message is received by another sensor passing through  , mutually disjoint covers are identified.
, mutually disjoint covers are identified.
Suppose  denotes the set of sensors with cover range passing through
denotes the set of sensors with cover range passing through  . The sensor with the largest ending angle in
. The sensor with the largest ending angle in  , denoted as
, denoted as  , initiates the algorithm. It first puts its neighbors which are in
, initiates the algorithm. It first puts its neighbors which are in  into
into  different sets. Then, for each set, it identifies some remaining neighbors to be put in the set, such that the sensors in the set can cover the range
different sets. Then, for each set, it identifies some remaining neighbors to be put in the set, such that the sensors in the set can cover the range  . The detailed procedure is as follows:
. The detailed procedure is as follows:  keeps track of a sorted order of the sets based on the ending angles of the cover ranges in the sensors of the sets. It takes the set with the smallest ending angle, and identifies a sensor that can extend its cover range. After putting the sensor in the set, the ending angle is updated. The process ends when there is no more sensor to extend the cover range of the set. It is possible that not all the sets can cover the whole range
keeps track of a sorted order of the sets based on the ending angles of the cover ranges in the sensors of the sets. It takes the set with the smallest ending angle, and identifies a sensor that can extend its cover range. After putting the sensor in the set, the ending angle is updated. The process ends when there is no more sensor to extend the cover range of the set. It is possible that not all the sets can cover the whole range  after all the neighbors of
after all the neighbors of  are put in the sets. In this case, these sets are removed and would not be put in the message. We argue that the removal of these sets will not affect the approximation ratio of the algorithm. Suppose no neighbor can extend the cover range of a set without a gap. Since this is the set with the smallest ending angle among all the sets and there are at least
are put in the sets. In this case, these sets are removed and would not be put in the message. We argue that the removal of these sets will not affect the approximation ratio of the algorithm. Suppose no neighbor can extend the cover range of a set without a gap. Since this is the set with the smallest ending angle among all the sets and there are at least  sensors covering the gap, this implies that
sensors covering the gap, this implies that  sensors that can cover the gap must fall into
sensors that can cover the gap must fall into  different sets. Therefore, there are still
different sets. Therefore, there are still  different sets remaining even the aforementioned one is removed.
different sets remaining even the aforementioned one is removed.
Refering to Figure 10, Sensor  is the sensor in
is the sensor in  with the largest end angle, so
with the largest end angle, so  is Sensor
is Sensor  . Sensor
. Sensor  puts Sensors
puts Sensors  ,
,  , and
, and  into
into  different sets, denoted as Set
different sets, denoted as Set  , Set
, Set  , and Set
, and Set  , respectively. Since Sensor
, respectively. Since Sensor  ends before Sensor
ends before Sensor  and Sensor
and Sensor  do, Sensor
do, Sensor  tries to put a neighbor into Set
tries to put a neighbor into Set  to extend its cover range. Hence, Sensor
to extend its cover range. Hence, Sensor  is put into Set
is put into Set  by Sensor
by Sensor  . Now, Sensor
. Now, Sensor  updates the ending angle of each set and finds that Set
updates the ending angle of each set and finds that Set  still ends before the others. Unfortunately, other neighbors of Sensor
still ends before the others. Unfortunately, other neighbors of Sensor  cannot be put into Set
cannot be put into Set  to extend the range of Set
to extend the range of Set  . Set
. Set  will then be removed. At this moment, only Set
will then be removed. At this moment, only Set  and Set
and Set  are remaining. Sensor
are remaining. Sensor  puts Sensor
puts Sensor  into Set
into Set  , and Sensor
, and Sensor  into Set
into Set  . Note that Sensor
. Note that Sensor  is not put in either set because it cannot extend the cover ranges of both sets. Now, Set
is not put in either set because it cannot extend the cover ranges of both sets. Now, Set  consists of
consists of  , while Set
, while Set  consists of
consists of  .
.
After the sets are identified,  puts the information in a message. The message format is
puts the information in a message. The message format is  , where each tuple
, where each tuple  contains the information of one set. The first element represents the identifier of the set. The second element represents the first member in the set
contains the information of one set. The first element represents the identifier of the set. The second element represents the first member in the set  . Note that this member must be a sensor in
. Note that this member must be a sensor in  and can later be used for determining whether the set
and can later be used for determining whether the set  forms a cover or not. Without loss of generality, we assume the tuple in the message is sorted according to the ending angle of
forms a cover or not. Without loss of generality, we assume the tuple in the message is sorted according to the ending angle of  . The third element represents the list of members selected to be included in the set
. The third element represents the list of members selected to be included in the set  by the node sending the message. The message is sent to the onlygreedy forward neighbor of
by the node sending the message. The message is sent to the onlygreedy forward neighbor of  . The greedy forward neighbor of
. The greedy forward neighbor of  , denoted as
, denoted as  , is the forward neighbor of
, is the forward neighbor of  with the largest end angle. Refering back to the example in Figure 10. Since Sensor
with the largest end angle. Refering back to the example in Figure 10. Since Sensor  selects
selects  into Set
into Set  and
and  into Set
into Set  , it sends out
, it sends out  to Sensor
to Sensor  .
.
When  receives the message, it tries to extend the cover ranges of the sets by putting its neighbors in them. The procedure is similar to what
receives the message, it tries to extend the cover ranges of the sets by putting its neighbors in them. The procedure is similar to what  did earlier. Refering back to the example in Figure 10, when Sensor
did earlier. Refering back to the example in Figure 10, when Sensor  receives
receives  , it finds that the ending angle of Set
, it finds that the ending angle of Set  is smaller than that of Set
is smaller than that of Set  . Therefore, it puts Sensor
. Therefore, it puts Sensor  into Set
into Set  . Then, it further puts Sensor
. Then, it further puts Sensor  into Set
into Set  , and then informs its own greedy forward neighbor to continue the set construction.
, and then informs its own greedy forward neighbor to continue the set construction.
We let the node with the smallest start angle in  be
be  . Since the message has been passed in the clockwise manner, it must be received by one of the backward neighbors of
. Since the message has been passed in the clockwise manner, it must be received by one of the backward neighbors of  , say
, say  . After
. After  has performed the set construction, it sends the message to
has performed the set construction, it sends the message to  instead of its greedy forward neighbor. After receiving the message,
instead of its greedy forward neighbor. After receiving the message,  continues the set construction for those sets which have not yet formed a cover. After considering all the neighbors that can extend the cover range of the sets, if there still exist sets which have not yet formed covers,
continues the set construction for those sets which have not yet formed a cover. After considering all the neighbors that can extend the cover range of the sets, if there still exist sets which have not yet formed covers,  reorganizes those sets. To avoid ambiguity, we now use covers to denote those sets which have formed covers.
reorganizes those sets. To avoid ambiguity, we now use covers to denote those sets which have formed covers.  keeps track of a sorted order of the sets based on the ending angles of the cover ranges in the sensors of the sets. It starts to form a cover from the set with the smallest ending angle. If no neighbors can be identified to form a cover, the sensors in the set with the largest identifier will be used, and the set with the largest identifier will no longer be considered for forming a cover. We argue that there will be at least
keeps track of a sorted order of the sets based on the ending angles of the cover ranges in the sensors of the sets. It starts to form a cover from the set with the smallest ending angle. If no neighbors can be identified to form a cover, the sensors in the set with the largest identifier will be used, and the set with the largest identifier will no longer be considered for forming a cover. We argue that there will be at least  covers formed at the end of the process. As discussed before, when no covers have been formed yet,
covers formed at the end of the process. As discussed before, when no covers have been formed yet,  sets are remaining. However, the worst case occurs when half of the sets are removed by
sets are remaining. However, the worst case occurs when half of the sets are removed by  so that the sensors can be moved to fill up the gaps to form the covers in the other half. Note that each perimeter segment is covered by at most
so that the sensors can be moved to fill up the gaps to form the covers in the other half. Note that each perimeter segment is covered by at most  sensors in a proper cover, and so it is not possible to remove more than
sensors in a proper cover, and so it is not possible to remove more than  sets.
sets.
Let us consider the example in Figure 10 again. Since Sensor  selects
selects  into Set
into Set  and
and  into Set
into Set  , it sends
, it sends  to
to  . Sensor
. Sensor  sends
sends  to
to  . Sensor
. Sensor  further puts Sensor
further puts Sensor  into Set
into Set  and then removes Set
and then removes Set  . Therefore, it sends
. Therefore, it sends  to Sensor
to Sensor  which is the forward neighbor of Sensor
which is the forward neighbor of Sensor  . Now, Sensor
. Now, Sensor  finds that Sensor
finds that Sensor  is the backward neighbor of
is the backward neighbor of  . As a result, a cover is formed in Set
. As a result, a cover is formed in Set  .
.
It is worth mentioning that all other sensors which do not involve in the circulation of the message can overhear the message transmission. Therefore, they know the set which they have been selected in. When  completes the covers formation process, it can construct the activation schedule. Then,
completes the covers formation process, it can construct the activation schedule. Then,  announces the activation schedule of different covers. The message about the activation schedule can be circulated through the whole network in the same manner as the cover identification process. By overhearing this message, all the sensors know their schedules. The whole process can then be terminated when the message circulates back to
announces the activation schedule of different covers. The message about the activation schedule can be circulated through the whole network in the same manner as the cover identification process. By overhearing this message, all the sensors know their schedules. The whole process can then be terminated when the message circulates back to  again. The pseudocodes of Sensors
again. The pseudocodes of Sensors  and
and  who receives the cover identification message are provided in Algorithms 1 and 2, respectively.
who receives the cover identification message are provided in Algorithms 1 and 2, respectively.
Algorithm 1: Pseudocode of  receives
receives  sent by
sent by  .
.
1:  is a set of sensors selected into available set
is a set of sensors selected into available set  by
by  . Initially, the last member of
. Initially, the last member of  is put into
is put into  .
.
2:  is the last member in
is the last member in  .
.
3:  is the index of the set which has the smallest ending angle among all
is the index of the set which has the smallest ending angle among all  , where
, where  .
.
4:  is the next hop target for the message.
is the next hop target for the message.
5:If is forward neighbor of
is forward neighbor of  then
then
6:  is
is  .
.
7:else
8:  is
is  .
.
9:end if
10:  selects neighbors to extend the cover range of the sets.
selects neighbors to extend the cover range of the sets. 
11:for each neighbor  do
do
12: If cannot extend the cover range of set
cannot extend the cover range of set  then
then
13: Remove the Set  .
.
14: end if
15: if is the forward neighbor of
is the forward neighbor of  then
then
16: Put  into
into  and
and  .
.
17: end if
18: Find the set with the smallest end angle and denote it as  .
.
19:end for
20: Send the message  , for
, for  to
to  and set
and set  has not been removed, to
has not been removed, to  .
.
Algorithm 2: Pseudocode of  receives message
receives message  .
.
1:  is a set of sensors which has originally been selected into a set but later removed by
is a set of sensors which has originally been selected into a set but later removed by  .
.
2:  is a set of sensors selected into available set
is a set of sensors selected into available set  by
by  . Initially, the last member of
. Initially, the last member of  is put into
is put into  .
.
3:  is the last member in
is the last member in  .
.
4:  is the index of the available set which has the smallest ending angle among all
is the index of the available set which has the smallest ending angle among all  and has not yet formed
and has not yet formed
a cover, where  .
.
5:  selects neighbors to extend the cover range of the sets.
selects neighbors to extend the cover range of the sets. 
6: for each set  do
do
7: while (set  does not form a cover) do
does not form a cover) do
8: Select sensors in  which can cover [
which can cover [ ,
, ] to
] to  .
.
9: if Set  still does not form a cover then
still does not form a cover then
10:  Remove the available set with the highest index number, that is,
Remove the available set with the highest index number, that is, 
11: Move sensors in  ,
,  , and
, and  to
to  .
.
12:  .
.
13: end if
14: end while
15: end for
16: Announce  , for
, for  to
to  , together with the activation schedule for each cover.
, together with the activation schedule for each cover.
In fact, we can further optimize the message overheads in terms of the number of messages required by removing the activation schedule circulation process. To do so, we can reorganize the sets when we find that the cover range of a set cannot be extended by putting a neighbor into the set. Here, we always use the sensors in the set with the largest identifier to extend the cover range of a set, and the set with the largest identifier will no longer be considered for forming a cover. By doing so, we know that if  covers are formed finally, they will have set identifiers
covers are formed finally, they will have set identifiers  . Since the sensors can overhear in which set they are selected in, they can activate automatically following the time slot allocated to the cover with a specific set identifier without the need of circulating the activation schedule.
. Since the sensors can overhear in which set they are selected in, they can activate automatically following the time slot allocated to the cover with a specific set identifier without the need of circulating the activation schedule.
7. Simulation Results
For comparison, we have implemented several algorithms. The first algorithm is the optimal solution found by transforming the maximum lifetime scheduling problem to the Multicommodity Network Flow problem, and solved by AMPL-CPLEX [38], which is denoted as Optimal in our figures. The second algorithm is the one proposed in this paper, which is denoted as Proposed algorithm in the figures. The third algorithm is the one proposed in [5], which is denoted as Round-based algorithm in the figures. In this algorithm, a minimum size cover, known as  , is found to monitor the target object in each monitoring cycle until no more MC can be found. The fourth algorithm is denoted as Single-MC in the figures. In this algorithm, an MC is found and this MC is activated until a sensor is running out of energy. Afterwards, another MC is found and activated again. This process continues until no more MC can be found.
, is found to monitor the target object in each monitoring cycle until no more MC can be found. The fourth algorithm is denoted as Single-MC in the figures. In this algorithm, an MC is found and this MC is activated until a sensor is running out of energy. Afterwards, another MC is found and activated again. This process continues until no more MC can be found.
In our simulations, we considered an area of  grids
grids  grids. Each grid takes up an area of
grids. Each grid takes up an area of  unit
unit and has a certain probability of containing a sensor. A grid that is partially/completely occupied by the target does not have any sensor. This probability is known as thesensor availability probability, and we use
and has a certain probability of containing a sensor. A grid that is partially/completely occupied by the target does not have any sensor. This probability is known as thesensor availability probability, and we use  to denote it. If the grid contains a sensor, the sensor is located at the center of the grid. This is similar to the simulation environment considered in [5]. Each sensor has a sensing range
to denote it. If the grid contains a sensor, the sensor is located at the center of the grid. This is similar to the simulation environment considered in [5]. Each sensor has a sensing range  ; The target object is located at the center
; The target object is located at the center  with the object radius of
with the object radius of  . For uniform initial battery case, each sensor has
. For uniform initial battery case, each sensor has  units of energy. In the nonuniform battery case, each sensor has a mean value
units of energy. In the nonuniform battery case, each sensor has a mean value  units of energy. The uniform case is denoted as
units of energy. The uniform case is denoted as  , while the nonuniform case is denoted as
, while the nonuniform case is denoted as  in the figures. Each monitoring cycle is assumed to take up
in the figures. Each monitoring cycle is assumed to take up  units of energy, and each message takes up
units of energy, and each message takes up  unit of energy if transmission cost is counted.
unit of energy if transmission cost is counted.
7.1. Effect of Energy Needed Per Cycle
First of all, we simulated the scenario in which  ,
,  units,
units,  units, and
units, and  units. In the simulations, we vary
units. In the simulations, we vary  from
from  to
to  units per cycle. Figure 11(a) illustrates the network lifetime achieved by various algorithms under different energy needed per cycle without transmission cost. The figure shows that all the algorithms have shorter lifetimes when each monitoring cycle requires more energy. On the other hand, our proposed algorithm achieves similar network lifetime with that ofSingle-MC andRound-based algorithm as all the algorithms are
units per cycle. Figure 11(a) illustrates the network lifetime achieved by various algorithms under different energy needed per cycle without transmission cost. The figure shows that all the algorithms have shorter lifetimes when each monitoring cycle requires more energy. On the other hand, our proposed algorithm achieves similar network lifetime with that ofSingle-MC andRound-based algorithm as all the algorithms are  -approximation solutions if no transmission cost is counted. All of them achieve around
-approximation solutions if no transmission cost is counted. All of them achieve around  of the maximum lifetime under the uniform battery environment. This is mainly because many sensors have never been chosen in any proper cover. In the nonuniform situation, the lifetimes of the algorithms are about
of the maximum lifetime under the uniform battery environment. This is mainly because many sensors have never been chosen in any proper cover. In the nonuniform situation, the lifetimes of the algorithms are about  of the optimal one. This is mainly due to the reason that more nodes are involved.
of the optimal one. This is mainly due to the reason that more nodes are involved.
Varying energy needed per cycle scenario. Network lifetime versus energy needed per cycle without transmission costNetwork lifetime versus energy needed per cycle with transmission costNumber of messages versus energy needed per cycle with transmission costNumber of rounds versus energy needed per cycle with transmission cost
Figure 11(b) shows the performance under different energy needed per cycle with transmission cost. It can be shown thatRound-based algorithm is affected the most by the transmission cost as an MC needs to be found every cycle, while our proposed algorithm is affected by the transmission cost the least. Therefore, our purposed algorithm outperforms the others. Figures 11(c) and 11(d) illustrate the number of messages and the number of scheduling rounds required by various algorithms throughout the network lifetime. As expected,Round-based algorithm requires the most number of messages and rounds, while our algorithm requires the least. It is worthwhile to state that our proposed algorithm requires only one scheduling round with  (size of the
(size of the  ) and this contributes to the good performance shown in Figures 11(c) and 11(d). On the other hand, the figures also show that our proposed algorithm and the Round-based algorithm require similar amount of messages and rounds no matter the initial battery capacity of a sensor is uniform or not. However, there is a large discrepancy between uniform and nonuniform battery for theSingle-MC algorithm. It is becauseSingle-MC algorithm finds an MC and then it is activated until a sensor in this MC fails. In the uniform battery scenario, nearly all the sensors in an MC runs out of energy simultaneously. However, this is not the case in nonuniform battery scenario.
) and this contributes to the good performance shown in Figures 11(c) and 11(d). On the other hand, the figures also show that our proposed algorithm and the Round-based algorithm require similar amount of messages and rounds no matter the initial battery capacity of a sensor is uniform or not. However, there is a large discrepancy between uniform and nonuniform battery for theSingle-MC algorithm. It is becauseSingle-MC algorithm finds an MC and then it is activated until a sensor in this MC fails. In the uniform battery scenario, nearly all the sensors in an MC runs out of energy simultaneously. However, this is not the case in nonuniform battery scenario.
7.2. Effect of Initial Battery Capacity
In Figures 12(a) and 12(b), we simulated the scenario where  units,
units,  units, and
units, and  units per cycle. In these simulations, we vary the mean value
units per cycle. In these simulations, we vary the mean value  from
from  to
to  units. Figures 12(a) and 12(b) illustrate the network lifetime achieved by various algorithms under different initial battery capacity settings without transmission cost and with transmission cost, respectively. The figure shows that all the algorithms have longer lifetimes when the initial battery capacity increases. Similar to the results in Figure 11(a), all the
units. Figures 12(a) and 12(b) illustrate the network lifetime achieved by various algorithms under different initial battery capacity settings without transmission cost and with transmission cost, respectively. The figure shows that all the algorithms have longer lifetimes when the initial battery capacity increases. Similar to the results in Figure 11(a), all the  -approximation solutions achieve about
-approximation solutions achieve about  and over
and over  of the optimal solution under the uniform and nonuniform scenarios, respectively. These results show that the algorithms considered generally achieve good performance although they are 2-approximation solutions. Similar to that in Figures 11(a) and 11(b), our proposed algorithm performs similarly to the Round-based and Single-MC algorithms in case no transmission cost is counted. However, our proposed algorithm outperforms them when transmission cost is considered. This is mainly due to the reasons that more messages are required in other algorithms as shown in Figure 12(c) where the number of messages required grows with the increasing initial battery capacity.
of the optimal solution under the uniform and nonuniform scenarios, respectively. These results show that the algorithms considered generally achieve good performance although they are 2-approximation solutions. Similar to that in Figures 11(a) and 11(b), our proposed algorithm performs similarly to the Round-based and Single-MC algorithms in case no transmission cost is counted. However, our proposed algorithm outperforms them when transmission cost is considered. This is mainly due to the reasons that more messages are required in other algorithms as shown in Figure 12(c) where the number of messages required grows with the increasing initial battery capacity.
In both the scenarios considered in Sections 7.1 and 7.2, the algorithms achieve longer lifetime when uniform initial battery is considered. It is because any portion of the perimeter is covered by sensors with approximately the same amount of total energy. Unfortunately, this is not the case in the nonuniform initial battery scenario where some portions have significantly higher total energy than others.
7.3. Effects of Sensing Range
In this section, we have simulated the scenario in which  ,
,  units,
units,  units, and mean value
units, and mean value  units. In the simulations, we vary
units. In the simulations, we vary  from
from  to
to  units. Here, we study two scenarios. First, each sensor has the same sensing range
units. Here, we study two scenarios. First, each sensor has the same sensing range  , we denote this as thehomogenous sensing range scenario. Second, different sensors may have different sensing ranges. In other words, each sensor has the sensing range with the mean value
, we denote this as thehomogenous sensing range scenario. Second, different sensors may have different sensing ranges. In other words, each sensor has the sensing range with the mean value  . We denote this scenario as the heterogenous sensing range scenario.
. We denote this scenario as the heterogenous sensing range scenario.
Let us start with the homogenous sensing range scenario. Generally speaking, the longer the sensing range, the fewer the sensors needed to cover the perimeter of the target object. This results in longer network lifetime in various algorithms as shown in Figure 13(a). On the other hand, Figure 13(b) illustrates that our proposed algorithm requires fewer messages when the sensing range increases. This is mainly due to the reason that the larger the sensing range the smaller the size of the minimum cover is. Recall that our proposed algorithm requires  (size of the minimum cover) number of messages to find all the schedules. However, Round-based and Single-MC algorithms require more messages when the sensing range increases. On one hand, the longer the sensing range, fewer messages are needed to find an MC. On the other hand, the longer the sensing range, less sensors are required to cover a target object. This results in a larger number of scheduling rounds. Since the second factor outweighs the first factor, the number of messages increases in both the Round-based and Single-MC algorithms.
(size of the minimum cover) number of messages to find all the schedules. However, Round-based and Single-MC algorithms require more messages when the sensing range increases. On one hand, the longer the sensing range, fewer messages are needed to find an MC. On the other hand, the longer the sensing range, less sensors are required to cover a target object. This results in a larger number of scheduling rounds. Since the second factor outweighs the first factor, the number of messages increases in both the Round-based and Single-MC algorithms.
We further consider the heterogenous sensing range scenario in Figure 14(a). Figure 14(a) exhibits similar trend as that of the homogenous sensing range scenario in Figure 13(a) due to the same reason aforementioned. However, when we compare the homogenous sensing range and the heterogenous sensing range scenarios with the mean value  in Figure 14(b), we can find that the lifetime achievable by the heterogenous scenario is better than that of the homogenous case. In fact, this phenomenon can be explained with the help of Figure 14(c). As we know that the network lifetime achievable is upper bounded by
in Figure 14(b), we can find that the lifetime achievable by the heterogenous scenario is better than that of the homogenous case. In fact, this phenomenon can be explained with the help of Figure 14(c). As we know that the network lifetime achievable is upper bounded by  , we compare
, we compare  of the homogenous and the heterogenous sensing range scenarios in Figure 14(c). In both scenarios, we can observe that
of the homogenous and the heterogenous sensing range scenarios in Figure 14(c). In both scenarios, we can observe that  of the uniform initial battery capacity case is higher than that of the nonuniform initial battery case. These agree with the results shown in Figures 13(a) and 14(a) that various algorithms achieve better lifetime in the uniform initial battery case than that in the nonuniform initial battery case. On the other hand, we can observe that
of the uniform initial battery capacity case is higher than that of the nonuniform initial battery case. These agree with the results shown in Figures 13(a) and 14(a) that various algorithms achieve better lifetime in the uniform initial battery case than that in the nonuniform initial battery case. On the other hand, we can observe that  of the homogenous sensing range scenario is generally smaller than that of the heterogenous sensing range scenario no matter the initial battery capacity of the sensor is uniform or not. This is mainly due to the reason that some sensors which are too far to cover any portion of the perimeter of the target object in the homogenous sensing range scenario may cover a certain portion of the perimeter in the heterogenous sensing range scenario. This also accounts for the better performance shown in heterogenous sensing range scenario.
of the homogenous sensing range scenario is generally smaller than that of the heterogenous sensing range scenario no matter the initial battery capacity of the sensor is uniform or not. This is mainly due to the reason that some sensors which are too far to cover any portion of the perimeter of the target object in the homogenous sensing range scenario may cover a certain portion of the perimeter in the heterogenous sensing range scenario. This also accounts for the better performance shown in heterogenous sensing range scenario.
Comparison between homogenous and heterogenous sensing range scenarios. Network lifetime versus sensing range with transmission cost (heterogenous sensing range scenario)Comparison between homogenous and heterogenous sensing range scenarios in terms of lifetimeComparison between homogenous and heterogenous sensing range scenarios in terms of 
7.4. Effect of Object Size
In this section, we have simulated the scenario in which  ,
,  ,
,  units, and mean value
units, and mean value  units. In the simulations, we vary
units. In the simulations, we vary  from
from  to
to  units. Generally speaking, the larger the target radius, the larger the number of sensors needed to cover the perimeter of the whole target object. This results in smaller network lifetime in various algorithms as shown in Figure 15(a). On the other hand, Figure 15(b) illustrates that various algorithms require larger amount of messages when the target radius increases. This is mainly due to the reason that the larger the target radius the larger the size of the minimum cover is. In both figures, we can observe that our proposed algorithm generally achieves better performance than the others.
units. Generally speaking, the larger the target radius, the larger the number of sensors needed to cover the perimeter of the whole target object. This results in smaller network lifetime in various algorithms as shown in Figure 15(a). On the other hand, Figure 15(b) illustrates that various algorithms require larger amount of messages when the target radius increases. This is mainly due to the reason that the larger the target radius the larger the size of the minimum cover is. In both figures, we can observe that our proposed algorithm generally achieves better performance than the others.
7.5. Effect of Network Density
In this section, we have simulated the scenario in which  units,
units,  units,
units,  units, and mean value
units, and mean value  units. In the simulations, we vary
units. In the simulations, we vary  from
from  to
to  units. Generally speaking, the smaller the sensor availability probability, the fewer the sensors exist in the network. This results in smaller network lifetime in various algorithms as shown in Figure 16(a). On the other hand, Figure 16(b) illustrates that our proposed algorithm requires similar amount of messages no matter what the value of
units. Generally speaking, the smaller the sensor availability probability, the fewer the sensors exist in the network. This results in smaller network lifetime in various algorithms as shown in Figure 16(a). On the other hand, Figure 16(b) illustrates that our proposed algorithm requires similar amount of messages no matter what the value of  is. However, Round-based and Single-MC require smaller amount of messages when
is. However, Round-based and Single-MC require smaller amount of messages when  becomes smaller. This is mainly due to the reason that fewer sensors exist in the network. Therefore, the total number of rounds required to find the
becomes smaller. This is mainly due to the reason that fewer sensors exist in the network. Therefore, the total number of rounds required to find the  decreases in both cases. Hence, this results in the smaller number of messages. Nevertheless, we still observe that our proposed algorithm generally achieves the best performance.
decreases in both cases. Hence, this results in the smaller number of messages. Nevertheless, we still observe that our proposed algorithm generally achieves the best performance.
8. Conclusion and Future Work
In this paper, we study the perimeter coverage scheduling problem. We found that this problem is solvable in polynomial time under some special sensor configurations. However, this problem is NP-hard in general. We realize that the selection of a proper cover in each cycle leads to a  -approximation solution. We then propose a simple distributed
-approximation solution. We then propose a simple distributed  -approximation solution with
-approximation solution with  size of the minimum cover
size of the minimum cover number of messages, and we demonstrate its effectiveness through simulations.
number of messages, and we demonstrate its effectiveness through simulations.
In the future, we plan to study the perimeter coverage scheduling issues on the scenario where a sensor can monitor multiple continuous portions of the perimeter on the target object instead of a single continuous portion. In [29], we have proposed a distributed  maximum number of cover ranges per sensor
maximum number of cover ranges per sensor approximation solution on the problem of finding the minimum size and minimum cost set of sensors to cover the perimeter of the whole target object. To the best of our knowledge, no approximation solution has been developed on the scheduling problem up to now and the approximation ratio is likely to be larger than
approximation solution on the problem of finding the minimum size and minimum cost set of sensors to cover the perimeter of the whole target object. To the best of our knowledge, no approximation solution has been developed on the scheduling problem up to now and the approximation ratio is likely to be larger than  maximum number of cover ranges per sensor
maximum number of cover ranges per sensor . Therefore, we would like to develop a distributed approximation solution to tackle this issue in the coming future.
. Therefore, we would like to develop a distributed approximation solution to tackle this issue in the coming future.
References
Chow K-Y, Lui K-S, Lam EY: Maximizing angle coverage in visual sensor networks. Proceedings of IEEE International Conference on Communications (ICC '07), June 2007 3516-3521.
Chow K-Y, Lui K-S, Lam EY:Achieving 360
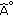 angle coverage with minimum transmission cost in visual sensor networks. Proceedings of IEEE Wireless Communications and Networking Conference (WCNC '07), March 2007 4115-4119.
angle coverage with minimum transmission cost in visual sensor networks. Proceedings of IEEE Wireless Communications and Networking Conference (WCNC '07), March 2007 4115-4119.Hung K-S, Lui K-S: On perimeter coverage of wireless sensor networks. Department of Electrical and Electronic Engineering, The University of Hong Kong; September 2008.
Hung K-S, Lui K-S: On perimeter coverage of wireless sensor networks with minimum cost. Department of Electrical and Electronic Engineering, The University of Hong Kong; December 2008.
Chow K-Y, Lui K-S, Lam EY: Wireless sensor networks scheduling for full angle coverage. Multidimensional Systems and Signal Processing 2009, 20(2):101-119. 10.1007/s11045-008-0062-3
Dong Q: Maximizing system lifetime in wireless sensor networks. Proceedings of the 4th International Symposium on Information Processing in Sensor Networks (IPSN '05), April 2005 13-19.
Schurgers C, Srivastava MB: Energy efficient routing in wireless sensor networks. Proceedings of IEEE Military Communications Conference (MILCOM '01), October 2001 1: 357-361.
Dietrich I, Dressler F: On the lifetime of wireless sensor networks. ACM Transactions on Sensor Networks 2009., 5(1, article 5):
Huang C-F, Lo L-C, Tseng Y-C, Chen W-T: Decentralized energy-conserving and coverage-preserving protocols for wireless sensor networks. Proceedings of IEEE International Symposium on Circuits and Systems (ISCAS '05), May 2005 1: 640-643.
Tian D, Georganas ND: A coverage-preserving node scheduling scheme for large wireless sensor networks. Proceedings of the ACM International Workshop on Wireless Sensor Networks and Applications, September 2002 32-41.
Yan T, He T, Stankovic JA: Differentiated surveillance for sensor networks. Proceedings of the 1st International Conference on Embedded Networked Sensor Systems (SenSys '03), November 2003 51-62.
Hsin C-F, Liu M: Network coverage using low duty-cycled sensors: random and coordinated sleep algorithms. Proceedings of the 3rd International Symposium on Information Processing in Sensor Networks (IPSN '04), April 2004 433-442.
Huang C-F, Tseng Y-C: The coverage problem in a wireless sensor network. Proceedings of the 2nd ACM International Workshop on Wireless Sensor networks and Applications (WSNA '03), September 2003 115-121.
Huang C-F, Lo L-C, Tseng Y-C, Chen W-T: Decentralized energy-conserving and coverage-preserving protocols for wireless sensor networks. ACM Transactions on Sensor Networks 2006, 2(2):182-187. 10.1145/1149283.1149285
Ye M, Chan E, Chen G, Wu J: Energy efficient fractional coverage schemes for low cost wireless sensor networks. Proceedings of the 26th IEEE International Conference on Distributed Computing Systems Workshops (ICDCS '06), July 2006
Wang L, Kulkarni SS: Sacrificing a little coverage can substantially increase network lifetime. Ad Hoc Networks 2008, 6(8):1281-1300. 10.1016/j.adhoc.2007.11.013
Ren S, Li Q, Wang H, Chen X, Zhang X: Design and analysis of sensing scheduling algorithms under partial coverage for object detection in sensor networks. IEEE Transactions on Parallel and Distributed Systems 2007, 18(3):334-350.
Cardei M, Thai MT, Li Y, Wu W: Energy-efficient target coverage in wireless sensor networks. Proceedings of IEEE Conference on Computer Communications (INFOCOM '05), March 2005 3: 1976-1984.
Liu H, Wan P, Jia X: Maximal lifetime scheduling for sensor surveillance systems with K sensors to one target. IEEE Transactions on Parallel and Distributed Systems 2006, 17(12):1526-1536.
Zhao Q, Gurusamy M: Lifetime maximization for connected target coverage in wireless sensor networks. IEEE/ACM Transactions on Networking 2008, 16(6):1378-1391.
Thai MT, Li Y, Du D-Z, Wang F: O (log n)-localized algorithms on the coverage problem in heterogeneous sensor networks. Proceedings of the 27th IEEE International Performance Computing and Communications Conference (IPCCC '07), April 2007 85-92.
Calines G, Ellis RB: Monitoring schedules for randomly deployed sensor networks. Proceedings of the 5th ACM International Workshop on Foundations of Mobile Computing (DIALM-POMC '08), August 2008 3-11.
Kumar S, Lai TH, Arora A: Barrier coverage with wireless sensors. Wireless Networks 2007, 13(6):817-834. 10.1007/s11276-006-9856-0
Kumar S, Lai TH, Posner ME, Sinha P: Optimal sleep-wakeup algorithms for barriers of wireless sensors. Proceedings of the 4th International Conference on Broadband Communications, Networks and Systems (BroadNets '07), September 2007 327-336.
Chen A, Kumar S, Lai TH: Designing localized algorithms for barrier coverage. Proceedings of the 13th Annual International Conference on Mobile Computing and Networking (MOBICOM '07), September 2007 63-74.
Chen A, Lai TH, Xuan D: Measuring and guaranteeing quality of barrier-coverage in wireless sensor networks. Proceedings of the International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc '08), April 2008 421-430.
Liu B, Dousse O, Wang J, Saipulla A: Strong barrier coverage of wireless sensor networks. Proceedings of the 9th International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc '08), May 2008 411-419.
Saipulla A, Westphal C, Liu B, Wang J: Barrier coverage of line-based deployed wireless sensor networks. Proceedings of the IEEE Conference on Computer Communications (INFOCOM '09), April 2009 127-135.
Hung K-S, Lui K-S: Perimeter coverage made practical in wireless sensor networks. Proceedings of the 9th International Symposium on Communications and Information Technology (ISCIT '09), September 2009 87-92.
Lee H, Aghajan H: Vision-enabled node localization in wireless sensor networks. Proceedings of the Cognitive Systems with Interactive Sensors (COGIS '06), March 2006
McCormick C, Laligand P-Y, Lee H, Aghajan H: Distributed agent control with self-localizing wireless image sensor networks. Proceedings of the Cognitive Systems with Interactive Sensors (COGIS '06), March 2006
Tezcan N, Wang W: Self-orienting wireless multimedia sensor networks for maximizing multimedia coverage. Proceedings of IEEE International Conference on Communications (ICC '08), May 2008 2206-2210.
Cardei M, Wu J, Lu M: Improving network lifetime using sensors with adjustable sensing range. International Journal of Sensor Networks 2006, 1: 41-49. 10.1504/IJSNET.2006.010833
Deng J, Han YS, Heinzelman WB, Varshney PK: Balanced-energy sleep scheduling scheme for high-density cluster-based sensor networks. Computer Communications 2005, 28(14):1631-1642. 10.1016/j.comcom.2005.02.019
Bonuccelli MA: Dominating sets and domatic number of circular arc graphs. Discrete Applied Mathematics 1985, 12(3):203-213. 10.1016/0166-218X(85)90025-3
Orlin JB, Bonucceli MA, Bovet DP:An
 algorithm for coloring proper circular arc graphs. SIAM Journal on Algebraic Discrete Methods 1981, 2(2):88-93. 10.1137/0602012
algorithm for coloring proper circular arc graphs. SIAM Journal on Algebraic Discrete Methods 1981, 2(2):88-93. 10.1137/0602012Garey MR, Johnson DR, Miller GL, Paradimitriou CH: The complexity of coloring circular arcs and chords. SIAM Journal on Algebraic and Discrete Methods 1980, 1(2):216-223. 10.1137/0601025
Fourer R, Gay DM, Kernighan BW: AMPL: A Modeling Language for Mathematical Programming. 2nd edition. Cole Publishing Company; 2002.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License (https://creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Hung, KS., Lui, KS. Perimeter Coverage Scheduling in Wireless Sensor Networks Using Sensors with a Single Continuous Cover Range. J Wireless Com Network 2010, 926075 (2010). https://doi.org/10.1155/2010/926075
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1155/2010/926075




 .
.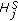 denotes the set of sensors in
denotes the set of sensors in  which cover
which cover  . Formally,
. Formally, 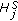 =
= 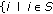 covers
covers  . For instance,
. For instance,  . We further let
. We further let 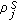 denote
denote 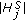 . For instance,
. For instance, 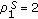 .
.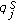 denotes the total number of energy cycles of the sensors in
denotes the total number of energy cycles of the sensors in 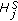 . Formally,
. Formally, 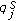 =
= 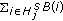 . For instance,
. For instance, 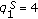 since
since 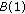 +
+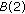 =
= 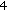 .
. denotes the
denotes the 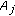 with the minimum
with the minimum 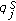 . Formally,
. Formally,  =
= 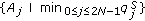 , for example,
, for example, 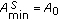 .
. =
= 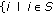 covers
covers 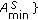 ,
, 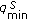 =
=  , and
, and  =
=  . For instance,
. For instance, 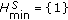 ,
, 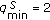 , and
, and 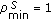 .
.
 .
.
 covers.
covers.

 from
from  .
. , put Sensor
, put Sensor  in
in  and the cover range of
and the cover range of 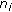 is
is  .
. ,
, 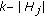 sensors with cover range of
sensors with cover range of  are put in
are put in 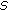 . These sensors are named with
. These sensors are named with 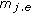 , where
, where  .
.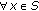 ,
, 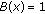 .
.
 .
.
 from
from  .
.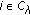 ,
,  .
.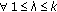 ,
, 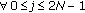 , if there is no sensor in
, if there is no sensor in 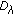 which can cover
which can cover  , then we can randomly select a sensor
, then we can randomly select a sensor 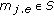 , where
, where 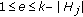 , with cover range
, with cover range 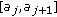 into
into  to cover
to cover  . Recall that there are
. Recall that there are 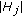 arcs in
arcs in 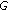 covering
covering 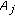 and these arcs must fall into
and these arcs must fall into 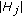 different colors, that is, different partitions. Since we have constructed
different colors, that is, different partitions. Since we have constructed 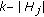 sensors with cover range
sensors with cover range 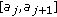 in
in  , if there is no sensor in
, if there is no sensor in 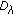 which can cover
which can cover 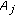 , then we can always find a sensor
, then we can always find a sensor 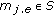 , where
, where 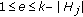 , with cover range
, with cover range 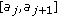 to put into
to put into  .
.






 angle coverage with minimum transmission cost in visual sensor networks. Proceedings of IEEE Wireless Communications and Networking Conference (WCNC '07), March 2007 4115-4119.
angle coverage with minimum transmission cost in visual sensor networks. Proceedings of IEEE Wireless Communications and Networking Conference (WCNC '07), March 2007 4115-4119. algorithm for coloring proper circular arc graphs. SIAM Journal on Algebraic Discrete Methods 1981, 2(2):88-93. 10.1137/0602012
algorithm for coloring proper circular arc graphs. SIAM Journal on Algebraic Discrete Methods 1981, 2(2):88-93. 10.1137/0602012