- Research Article
- Open access
- Published:
A Novel Real-Time Coal Miner Localization and Tracking System Based on Self-Organized Sensor Networks
EURASIP Journal on Wireless Communications and Networking volume 2010, Article number: 142092 (2010)
Abstract
With the development of information technology, we envision that the key of improving coal mine safety is how to get real-time positions of miners. In this paper, we propose a prototype system for real-time coal miner localization and tracking based on self-organized sensor networks. The system is composed of hardware and software platform. We develop a set of localization hardware devices with the Safety Certificate of Approval for Mining Products include miner node, wired fixed access station, and base with optical port. On the software side, we develop a layered software architecture of node application, server management, and information dissemination and broadcasting. We also develop three key localization technologies: an underground localization algorithm using received signal strength indication- (RSSI-) verifying algorithm to reduce the influence of the severe environment in a coal mine; a robust fault-tolerant localization mechanism to improve the inherent defect of instability of RSSI localization; an accurate localization algorithm based on Monte Carlo localization (MCL) to adapt to the underground tunnel structure. In addition, we conduct an experimental evaluation based on a real prototype implementation using MICA2 motes. The results show that our system is more accurate and more adaptive in general than traditional localization algorithms.
1. Introduction
Coal plays a strategic role in the current world and has tremendous impacts on lots of industries, such as energy, chemical, and material industry. It is quite obvious that coal is one of the basic industries of the national economy, and it is really important to develop the coal industry preferentially. On the other hand, in recent years, the coal industry is a restrictive factor of the development of the national economy in China. During the past four years, there were about 20,000 people killed in the coal mine disasters in China [1]. Therefore, coal mine disasters are a bottleneck factor in the development of the coal industry and is an issue that we have to face.
Why there are so many disasters and why do so many people die? Though there are management shortcomings in coal mines, there do still exist some imperfection in current technologies. In an ordinary coal mine in China, security monitoring system must already have been deployed which can monitor methane, wind speed, carbon monoxide, temperature, and the states of underground equipments. However, most disasters happen in such a short time that it is difficult for us to prevent them by monitoring underground coal mines. Nevertheless, if we can get the real-time positions of coal miners, we can warn underground miners to use life-support devices in disasters and attempt rescue according to miners' final positions as soon as possible. Consequently, delay can be reduced to a minimum.
So, the problem is how to get the real-time information of coal miners' positions. There are some critical requirements: firstly, the locations of miners must be more accurate than just knowing which area they are in; secondly, the system must be real-time; thirdly, the system must be easy to deploy and be able to work after disaster. Old technologies such as cable networks [2], trunked radio systems [3], and radio frequency identification (RFID) [4] do not satisfy all these requirements, and global position system (GPS) [5] system cannot work in an underground mine, so we have to find a new technology.
Self-organized sensor networks [6] are new technologies with the characteristics of low price, low power consumption, quick deployment, scalability, and strong environment adaptiveness. They have the functions of localization, self-organized communication and battery supply, and network node is convenient to carry with people for its tiny size. In recent years, research on self-organized sensor networks has developed quickly [7–10], and applied devices from Crossbow [11] and Freescale [12] have been developed to make self-organized sensor network applications possible. Recently, there have been lots of papers [13, 14] describing the design and implementation of coal miner monitoring systems based on self-organized sensor networks. So, it seems quite easy to monitor real-time coal miners' positions by the self-organized sensor networks key technologies.
Are all these true? At least, in our opinion, they are not as suitable as they seem to be. When we started to devise a workable system, there were many new questions that previous researchers have not been willing to face. Firstly, all underground coal mine tunnels are full of gas, and any spark may cause an explosion, so every device used in a coal mine should be fully safe and explosion-proof; secondly, the underground tunnel conditions are more complicated than those on the ground, poor underground conditions may badly influence localization algorithms; thirdly, the traffic of miners and trains in tunnels may influence the radio signals and the stability of localization algorithms; finally, all miners keep moving while they are in tunnels, so the accuracy of localization algorithms is a critical issue that we cannot avoid. To sum up the above arguments, we think the applications of self-organized sensor networks in coal mine still have long way to go.
In this paper, we design and implement an applied prototype system based on self-organized sensor networks technology to solve the problems of real-time coal miner localization and tracking. The contributions of this paper are fourfold. Firstly, we are the first to propose and implement a set of localization devices for underground mines based on wireless self-organized sensor networks with the Safety Certificate of Approval for Mining Products, which means this set of devices can be used in a real underground mine in real-time. Secondly, to meet the demands of the extremely adverse and complex environment, we propose a received signal strength indication- (RSSI-) based localization algorithm independent of the environment. Thirdly, we propose a robust localization mechanism to solve the problem of instability and jitter of results. Finally, we propose a practical localization algorithm for mobile nodes in the tunnel environment. The evaluation shows this set of localization algorithms have a 25% improvement on average error and a 10% improvement on accumulated probability distribution of error than a typical weighted-centroid algorithm while in adverse conditions, an 85% improvement on average stability than a typical weighted-centroid algorithm and a 40% improvement on accumulated probability distribution of error than a centroid algorithm which is absolutely steady, a 0.4 radio-range improvement on average error distance than normal Monte Carlo localization for mobile networks.
This paper is organized as follows. Section 2 analyzes the system requirements of a coal miner positioning application. Section 3 firstly gives the system architecture then describes the design and implementation of the hardware and software platform. Section 4 details the research on positioning key technologies which includes RSSI-verifying algorithm, a steady localization mechanism, and an accurate algorithm suitable for underground conditions. Section 5 describes the implementation of the whole system. Performance evaluation is reported in Section 6, paper summary is concluded in Section 7, and future work is discussed in Section  . Finally, acknowledgements are given Section
. Finally, acknowledgements are given Section  .
.
2. System Requirements
The underground conditions are more dangerous and complex than we can imagine. Firstly, the tunnel is long, dark, sinuous, and narrow; secondly, it is wet and probably inundated; thirdly, it's full of dangerous gas and may result in an accidental detonation. Besides these, we have no more specific devices but sensor nodes, so the only way we can use to localize is RSSI. So, if we want to solve the miner positioning problems out, we have to face the following application problems.
-
(i)
Firstly, no equipment can be used into coal mine directly without the Safety Certificate of Approval for Mining Products, for any electrical equipment may cause an explosion of gas in underground mine. Therefore, we have to prove that our equipments are of intrinsic safety [15] or place our equipment in the flameproof-modified enclosure [16]. This is the very first step of any coal mine applications.
-
(ii)
Secondly, the conditions of an underground tunnel are more complicated than those on the ground; they are wet, grotesque, and full of electromagnetic radiation. the adverse conditions may influence the accuracy of localization algorithms, especially the RSSI-based localization algorithms. So, how to reduce the influences of the underground conditions to RSSI-based localization algorithms is a great problem.
-
(iii)
Thirdly, the traffic of miners and trains in the tunnel may influence the radio signals and bring jitter to results of RSSI-based localization algorithms. So, how to reduce those bad influences and keep the stability of localization algorithms is another critical issue.
-
(iv)
Finally, all miners keep in moving status while they are in tunnels, but most localization algorithms are designed for static sensor networks, so they must not have pretty good performance in mobile networks. To design an accurate localization algorithm for underground mobile miner sensor networks according to some proper characteristics of mine tunnel is the most important part of the whole system.
3. System Architecture
Our system can be divided into two parts: hardware platform and software platform. These two parts need to work together and finally get the real-time position of every miner in the underground tunnel.
3.1. Hardware Platform
As mentioned before, no ready-made platform can be used into coal mine directly no matter it is made by Crossbow, Freescale, or any other manufacturer. Furthermore, we cannot modify the architecture and design of the bought platform, but during the safety certification, it is unavoidable for us to modify the circuit design and retrofit the explosion-proof shell so as to fit the mining products safety standard. Therefore, we have to design and implement the hardware platform from the very beginning, for the safety certificate of approval for mining products.
Our hardware platform is based on CC2420 [17] chip which is made by Chipcon and working on 2.4 GHz and conforming to IEEE 802.15.4, so it meets the Zigbee standard. The chip surrounding electrical circuits include crystal timing circuit, radio frequency (RF) in/out matching circuit, and microcontroller interface circuit, then using the referenced antijamming directed sequence spread spectrum (DSSS) [18] modulation type. Here, we give a snapshot of the exposed basic node in Figure 2, which has been proven to be of intrinsic safety when working on the recommended power voltage.
The whole hardware platform is composed of miner node, fixed station, and base with Ethernet or optical port
3.1.1. Miner Node
As shown in Figure 1, the core part of miner node is just an exposed basic node. We warp the exposed basic node into the miner's lamp. Then, we can guarantee each miner has a node and it must be working while in the mine, because every miner must carry a miner lamp and keep it working if he is in the mine. The power supply of the miner lamp is Li-ion battery. Firstly, its voltage fits the requirements of the exposed basic node, so the whole miner lamp keeps intrinsic safety. Secondly, each miner lamp can be charged during the night and the capacity of the battery can keep the lamp and node working for one day, so we do not have to care about energy constraints.
3.1.2. Fixed Station
As shown in Figure 1, the exposed basic node is also the core of the fixed station. But there are some differences between the power supply and the RF antenna. The fixed station can get the electrical power from electrical wires in the mine as it is deployed on the tunnel wall and there must have electrical wires. On the other hand, if some disaster happens and the electrical wires power supply is cut off, the fixed station must be able to work for sufficient period with the battery inside. In order to use the wired power, there must be some transformers inside. Therefore, it is not intrinsically safe anymore, and we must place all devices into a explosion-proof shell. Unfortunately, the shell is made in very thick steel, so the RF signal cannot penetrate through it. Thus, we have to extend the antenna from the printed circuit board (PCB) to out of the shell.
3.1.3. Base with Optical Port
The construction of coal mine is very special, and there might be dozens of kilometers far from the entrance of mine to some face. It is impossible for us to deploy a network to cover such a long tunnel and transfer data from face to control center out of mine hop by hop. Firstly, most accidents happen in the face. We just have to monitor the face nearby so as to cover most accidents. Secondly, the hardware platform cannot afford such long way multihop. The time delay and packet loss will be quite inconceivable. Thirdly, we can recur to the made optical network. Thus, we need a bridge between WSNs and optical, base with optical port. First of all, we need a basic node to communicate with WSNs as a base, and then we engineer a serial module and send all data to the RS232 interface, and finally, we buy the 277SM module which can convert the RS232 serial data into optical signal. We pack all these modules into one explosion-proof shell, and then we get the base with optical port.
3.2. Software Platform
We can divide our system into three layers: node application layer, server layer, and information publishing layer. The protocols in the node application layer can help node get data from its neighbors. The main function of the server layer is to collect data from base and send it to the information publishing layer after processing. The information publishing layer is to publish collected data to the end user directly and vividly.
3.2.1. Node Application Layer
In this layer, we focus on the technologies on collecting, selecting, packing, and transmitting of localization data. As there are differences between functions of similar node hardware, mobile nodes and anchor nodes should be considered in the design of node application layer.
-
(i)
Mobile nodes sample localization data periodically, and they are designed to passively collect localization data because the node number is too huge. Firstly, all anchor nodes send localization detection packets in
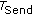 cycle, and all mobile nodes receive localization detection packets in
cycle, and all mobile nodes receive localization detection packets in 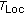 cycle
cycle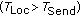 . In one
. In one  cycle, mobile nodes collect and buffer all localization detection packets they received. At the end of this cycle, they pack and send these packets. On the other hand, mobile nodes can receive management and query instructions and send response results.
cycle, mobile nodes collect and buffer all localization detection packets they received. At the end of this cycle, they pack and send these packets. On the other hand, mobile nodes can receive management and query instructions and send response results. -
(ii)
Anchor nodes can send localization detection packets and transmit packed data packets as routing node. They can also receive management and query instructions and send response results.
3.2.2. Server Layer
Server layer is in the middle of the whole system and plays the role of a bridge between node application layer and information publishing layer. Its main function is to write data collected by sensor networks into database. There are five modules in this layer: data-sampling module, message pool module, status-updating module, localization module, and data-storage module, as shown in Figure 2.
-
(i)
Data-sampling module: it reads input data. When a message packet has been read from serial port, data-sampling module will start a thread to analyze this packet and then insert it into corresponding message queue according to its packet type.
-
(ii)
Message pool module: it buffers and processes all messages which include two basic functions of inserting and retrieving. There are several message queues for different message types and the module is multithread competitive.
-
(iii)
Status-updating module: it modifies and stores node status information in message pool.
-
(iv)
Localization module: it calculates position by input localization detection message. This module is multi-thread, and each thread calculates one localization detection packet.
-
(v)
Data-storage module: it stores data messages which include node-status message and localization detection messages.
3.2.3. Information Publishing Layer
The main functions of information publishing layer include real-time coal miner dynamic display, 3D geographic information system (GIS) user interface, alarming, querying trajectories of all miners, and emergency rescue supporting. This layer is been developed with the service-oriented architecture (SOA).
-
(i)
Function of real-time miner display: the system can display how many miners, who are they, and where are they in underground coal mine tunnels in one specific time, can query the real-time position and the moving path in a period of one specific miner, can monitor some important inspectors' working status and prevent any human accident.
-
(ii)
Function of attendance: the system can record the attendance information of every miner and calculate the statistical information of all miners, and it can establish all kinds of report forms such as forms of working time, forms of monthly attendance, forms of overtime work, and forms of absence.
-
(iii)
Function of forbidden zone management: if there is any miner enter into appointed forbidden zone, the system will warn corresponding manager and give all information of this miner.
-
(iv)
Function of emergent rescue: the system can give the information of position of diaster, number and personal information of miners been trapped, and positions of every trapped miner to help rescuing. On the other hand, the network can work by battery supply for quite a while after the diaster, this may give some extent help.
4. Research of Localization Key Technologies
Localization key technologies are the base of the positioning and tracking system. We have to develop applied localization key technologies before developing the application system. Firstly, we focus on the localization algorithm based on RSSI, because RSSI is the most common way to solve WSNs localization problems. Then, we discuss the stability of localization algorithm based on RSSI, and finally we will try to solve the localization problems in underground mobile network by Monte Carlo method.
4.1. Underground Localization Algorithm Based on RSSI-Verification
In research on self-organized sensor networks localization, we can divide all algorithms into two sorts: range-based and range-free. Range-based means this sort of algorithm has to measure distances or angles between nodes during positioning them. The most common way is using RSSI to calculate distance. Range-free means this kind of algorithm need not distances or angles information during localization, but need the information of connectivity. The centroid localization algorithm [19] is the most basic algorithm in range-free algorithm. Based on this algorithm, the weighted centroid localization algorithm [20] is raised by using the RSSI value as weight. But in fact, the effect of RSSI is very much influenced by the underground conditions, so we propose a new RSSI-verifying algorithm which can enhance the adaptability to different conditions.
4.1.1. Basic Principle of Algorithm
In weighted centroid localization algorithm, suppose that there are  fixed nodes. The position of node
fixed nodes. The position of node  is
is  , where for each
, where for each  ,
,  . One mobile node
. One mobile node  wants to know its position
wants to know its position  , so we have
, so we have

In this equation,  means the weight of every fixed node, and it maybe a function of the distance between a mobile node and a fixed node. If there is no possible communication channel between mobile node
means the weight of every fixed node, and it maybe a function of the distance between a mobile node and a fixed node. If there is no possible communication channel between mobile node  and fixed node
and fixed node  , then we have
, then we have  .
.
As mentioned before, RSSI is very much influenced by environments in wireless self-organized sensor networks. There might be great difference of RSSI value between the same node pair in the same relative position and in different conditions. There might also be great difference in different areas or direction but in the same condition. That is to say, one RSSI value may mean different distances between different node pairs in the same network topology, so its corresponding weight must be different. If we calculate the position of mobile node  just by considering RSSI value between mobile node
just by considering RSSI value between mobile node  and fixed node
and fixed node  without any modification, the accuracy of the algorithm must be very much influenced by these conditions. Thus, we are here considering to verify the weight of every fixed node by consulting distances and RSSI values between fixed nodes.
without any modification, the accuracy of the algorithm must be very much influenced by these conditions. Thus, we are here considering to verify the weight of every fixed node by consulting distances and RSSI values between fixed nodes.
4.1.2. Description of Algorithm Implementation
Suppose that  means the average value of RSSI values which are received from fixed node
means the average value of RSSI values which are received from fixed node  by mobile node
by mobile node  and its unit is
and its unit is  .
.  means the average value of signal intensity values which are received from fixed node
means the average value of signal intensity values which are received from fixed node  by mobile node
by mobile node  and its unit is
and its unit is  . So, we have
. So, we have

We are now considering to verify the weight of every fixed node by consulting distances and RSSI values between fixed nodes. Suppose that  means the average value of RSSI values which are received from fixed node
means the average value of RSSI values which are received from fixed node  by fixed node
by fixed node  and its unit is
and its unit is  .
.  means the average value of signal intensity values which are received from fixed node
means the average value of signal intensity values which are received from fixed node  by fixed node
by fixed node  and its unit is
and its unit is  . So, we have
. So, we have

Suppose that  means the distance between fixed node
means the distance between fixed node  and
and  ,
,  means the distance between mobile node
means the distance between mobile node  and fixed node
and fixed node  which is calculated by substituting information between fixed node
which is calculated by substituting information between fixed node  and
and  into pass loss model of shadowing radio propagation model
into pass loss model of shadowing radio propagation model  , so we have
, so we have

We can define the distance  as the average value of all
as the average value of all  and define the weight of fixed node
and define the weight of fixed node  relative to mobile node
relative to mobile node  as
as

We can calculate the position of mobile node  according to the calculated weights of fixed nodes and (1). Lastly, suppose that the real position is
according to the calculated weights of fixed nodes and (1). Lastly, suppose that the real position is  , and we can define the error of localization
, and we can define the error of localization  as
as

4.2. Robust Localization Mechanism in Wireless Self-Organized Sensor Networks
As there is no critical functional relationship between RSSI value and distance, and as RSSI value maybe greatly influenced by conditions; therefore, we here propose a novel robust localization mechanism on the basis of RSSI-verifing algorithm.
4.2.1. Description of Principle
The basic procedure of this mechanism is using RSSI-verifying algorithm to get the original position, realizing discretization of localization by the way of dynamic geographic division and avoiding jumping of localization result by the way of automatic state machine, and finally getting the position.
-
(1)
Space Discretization
As mentioned before, we will realize discretization of localization by the way of dynamic geographic division. Now, we give the detailed procedure: firstly, we divide the whole field into nonoverlapping squares of
 . Then, we assume the original position in time
. Then, we assume the original position in time  of unknown node is
of unknown node is 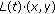 and its position after discretization in time
and its position after discretization in time 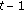 is
is  . Next, we can have the position after discretization in time
. Next, we can have the position after discretization in time 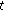 : if the distance between
: if the distance between 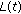 and
and 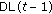 is less than
is less than 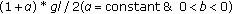 , then
, then 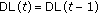 ; otherwise,
; otherwise, 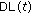 equals to the center of the square where
equals to the center of the square where 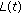 locates.
locates. -
(2)
Robust Localization Mechanism Based on Finite State Machine
We assume
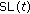 is the shown position of unknown node in time
is the shown position of unknown node in time 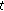 and use function
and use function 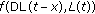 (
(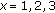 ) to compute the position after discretization of unknown node in time
) to compute the position after discretization of unknown node in time 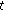 by its original position
by its original position 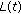 in time
in time 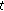 and positions after discretization in time
and positions after discretization in time 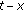 , and the initial state of the function is 0. Here, we have the steady localization mechanism based on automatic state machine which is shown in Figure 3.
, and the initial state of the function is 0. Here, we have the steady localization mechanism based on automatic state machine which is shown in Figure 3. -
(3)
A Robust Method for Avoiding Intermittent Interference
Here, we suppose that
 means the average value of RSSI values in time
means the average value of RSSI values in time 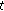 ,
, 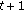 and
and 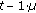 is a given threshold. Then, we will give a modification of intermittent interference avoiding by the way of filtering abnormal data packets.
is a given threshold. Then, we will give a modification of intermittent interference avoiding by the way of filtering abnormal data packets.-
(i)
The initial state is 0. If the difference between the max RSSI value in last round and RSSI value in time
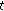 is less than
is less than 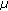 , then update
, then update 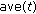 ; otherwise,
; otherwise, 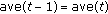 and go to state 1.
and go to state 1. -
(ii)
In state 1, if the difference between the max RSSI value in last round and RSSI value in time
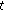 is less than
is less than 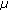 , then update ave(
, then update ave(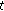 ) and go to state 0; otherwise,
) and go to state 0; otherwise, 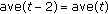 and go to state 2.
and go to state 2. -
(iii)
In state 2, go to state 0 directly at first. Then, if the difference between the max RSSI value in last round and RSSI value in time
 is less than
is less than  , then update
, then update  ; otherwise,
; otherwise, 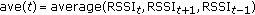 .
.
-
(i)
4.3. Accurate Localization Algorithm Based on Monte Carlo Localization (MCL) Suitable for Underground Mobile Networks
Localization algorithms based on MCL [21, 22] are frequently used in mobile target positioning. They are composed of two phases: predication and filtering. In traditional works, random movement models are the most common models of movement, but this kind of models may cause some impossible move actions such as sudden turning and stop which are really rare in normal people's movements. Actually, in underground mine, all movements are limited in mine tunnel and most tunnel are smooth, which means most movements are alone the tunnel and ought to be smooth. Based on the unique characteristics of underground mine environments, we have developed a new accurate MCL-based localization algorithm: we interpolate several previous positions of node to predicate its moving tendency and its next position, narrow the possible position area of node, and finally reduce the workload and enhance the accuracy.
4.3.1. Movement Predication of Node
Suppose that there is a mobile node  in a two-dimensional plane, and we have already known its positions
in a two-dimensional plane, and we have already known its positions  in time
in time  , and we have to predicate its moving tendency in time
, and we have to predicate its moving tendency in time  . As we all known, 3-dimensional interpolation must be the proper way to solve these. After considering the computing ability and energy of sensor node, we decide to use 2-dimensional Newton interpolation to interpolate
. As we all known, 3-dimensional interpolation must be the proper way to solve these. After considering the computing ability and energy of sensor node, we decide to use 2-dimensional Newton interpolation to interpolate  and
and  of
of  former time points
former time points . We suppose that the values of function
. We suppose that the values of function  in
in  different time
different time  are
are  , which are namely
, which are namely  . According to Newton interpolation polynomials, we have
. According to Newton interpolation polynomials, we have



In the same way, we have

According to (7) and (10), we can predicate the speed of mobile node  in
in  -direction and
-direction and  -direction
-direction  and
and  in time
in time  are
are

Suppose that the position of mobile node  in time
in time  is origin, we have the equation of the moving direction of mobile node
is origin, we have the equation of the moving direction of mobile node

and the speed of mobile node  is
is

There are some principles when selecting interpolation points
-
(1)
Maintain a sample window which includes
 sample points, so as to interpolate the track of mobile node.
sample points, so as to interpolate the track of mobile node. -
(2)
These
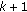 sampling points can be modified values of predicated positions in former
sampling points can be modified values of predicated positions in former 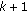 time points. The time interval can be random, but it would be better if it is more intensive and closer to current time.
time points. The time interval can be random, but it would be better if it is more intensive and closer to current time. -
(3)
Keep to maintain all sample points according the standards of time and accuracy. The following are some rules
-
(a)
Compare filtering-modified value of positions with positions got by interpolation. If there are great differences between the moving tendencies of these two positions, we must discard the former
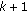 sample points, add the modified value into sample window, select those sample points in the window which has the minimum difference to the modified value, and start a new round interpolation from now on.
sample points, add the modified value into sample window, select those sample points in the window which has the minimum difference to the modified value, and start a new round interpolation from now on. -
(b)
If the difference between the moving tendencies of these two positions is less than a fixed threshold, we do not have to restart a new round interpolation.
-
(c)
Renew the window compulsorily at regular intervals.
-
(a)
4.3.2. Position Predication of Node
As mentioned before, in underground mine, all movements are limited in mine tunnels and most tunnels are smooth, which means most movements are along the tunnel and ought to be smooth. That is to say, we can fit the shapes of most tunnels and also most moving tracks by second order curves. Thus, we have.
-
(i)
Define a sector with the radius of
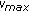 which branches at
which branches at 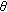 (
(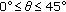 ) angle clockwise and counter-clockwise to the moving direction of mobile node
) angle clockwise and counter-clockwise to the moving direction of mobile node 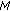 .
. -
(ii)
Define
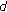 as second order curves which are tangent to the moving direction of mobile node
as second order curves which are tangent to the moving direction of mobile node 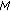 .
. -
(iii)
Select
 points as the predication positions from these
points as the predication positions from these 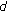 curves and these
curves and these  points must be in the sector.
points must be in the sector. -
(iv)
If the point number is less than
 after filtering, we can double the angle
after filtering, we can double the angle  and use the same way to complement the absent part. This part will repeat until we have
and use the same way to complement the absent part. This part will repeat until we have  points which can satisfy our requirements.
points which can satisfy our requirements.

4.3.3. Filtering Algorithm
We first give some definitions
Definition 1 (Neighbor nodes).
The unknown nodes in the communication radius of mobile node  .
.
Definition 2 (Inner anchor nodes).
All anchor nodes in the communication radius of mobile node  in current time, we call them the inner anchor nodes.
in current time, we call them the inner anchor nodes.
Definition 3 (Neighbor anchor nodes).
All anchor nodes in the communication radius of all mobile node  's neighbors in current time, we call them the neighbor anchor nodes.
's neighbors in current time, we call them the neighbor anchor nodes.
According to the broadcasting information during time  and
and  , we can get the inner anchor node aggregation and the neighbor anchor node aggregation of mobile node
, we can get the inner anchor node aggregation and the neighbor anchor node aggregation of mobile node  and record them as IS and NS, respectively. It is obvious that the distance between mobile node
and record them as IS and NS, respectively. It is obvious that the distance between mobile node  and one of its inner anchor nodes
and one of its inner anchor nodes  is not bigger than communication radius
is not bigger than communication radius  , and the distance mobile node
, and the distance mobile node  and one of its neighbor anchor nodes
and one of its neighbor anchor nodes  is bigger than
is bigger than  but less than
but less than  . Thus, we have the filter formula
. Thus, we have the filter formula

We can filter those predication positions which cannot satisfy (15) and suppose that their weights are all  . The rest part is operational predication positions and their weights are all
. The rest part is operational predication positions and their weights are all  . Suppose that the weight of predication position
. Suppose that the weight of predication position  is
is  , the number of position that we have to resample
, the number of position that we have to resample  is
is

We keep sampling and filtering in a cycle until  . Then, we have our
. Then, we have our  prediction positions which can satisfy (15). Because the weights of all predication positions are the same, so we can get the modified predication in time
prediction positions which can satisfy (15). Because the weights of all predication positions are the same, so we can get the modified predication in time  position by averaging the
position by averaging the  predication positions
predication positions

5. System Implementation
The system is implemented and distributed in XinYuan Mine of XinAn Coal Mine, ShanDong Province and in the experiment building of National High Performance Computing Center (NHPCC), University of Science and Technology of China (USTC). The programs on wireless self-organized sensor networks nodes are developed on TinyOS platform and with NesC, and the rest part of software is developed with Visual C# and Microsoft SQL 2000. According to the security arrangement between XinAn Coal Mine and us, we cannot release any information about the structure and detailed situation of the underground mine. Thus, we just show the implemented system in the experiment building of NHPCC, USTC.
In the implementation in the experiment building of NHPCC, the whole system is deployed from the second floor to the fifth floor and its main structure is a 300-meters-long tunnel which includes three pairs of stairs, as shown in part (a) of Figure 4. The snapshots of real implementation in XinYuan Mine of XinAn Coal Mine is shown in part (b) of Figure 4. There are lots of resemblances between these two scenes, which are linear multihop network, reinforced concrete tunnel structure, full of obstacles, and so on. In this implementation, there are 40 fixed nodes and its maximum hop is 13. After implementation, we can see that the timing-delay of localization is less than 10 s and its positioning accuracy is less than 5 m.
The system has the main functions of operator login, real-time 3D display, setting parameters, alarming of entering dangerous area, tracking, emergency response, and data statistical analysis and management. All functions are shown in Figure 5.
6. System Evaluation
A critical part of the system is the three new localization technologies. They determine the practicability of the system. In this section, we design simulations to evaluate the localization performance of the system with respect to the influence of environment, robustness of algorithms, and suitability for mobile networks.
6.1. Evaluation 1: Influence of Environment
6.1.1. Simulation
Our simulation program is based on TinyOS and MicaZ platform of CrossBow, which is developed by NesC language. The RF level is set to TXPOWER_MAX. In this simulation, there are five nodes. Four of them are fixed which are deployed on the four vertexes of one  rectangle in the underground mine in XinAn Coal Mine. Their coordinates are
rectangle in the underground mine in XinAn Coal Mine. Their coordinates are  , and
, and  . It is obvious that the whole simulation area can be divided into 48 little square
. It is obvious that the whole simulation area can be divided into 48 little square  . We randomly select 16 of them as the positions of mobile node.
. We randomly select 16 of them as the positions of mobile node.
The simulation is composed of two phases: RSSI collection phase which includes 50 cycles, and each cycle is 2 s. We record the RSSI values be received by mobile node from every fixed node on file and calculate the average value from each fixed node. At the same time, we record the RSSI values between every two fixed nodes on file and calculate the corresponding average value. The second phase is to calculate position of mobile node.
6.1.2. Evaluation
According to the shadowing radio propagation model, the parameter  should be in the range of 1.6
should be in the range of 1.6 1.8, so we change
1.8, so we change  in the range with the step of 0.05.
in the range with the step of 0.05.
It is obvious from Table 1 that the average error of the algorithm is minimum when  . Thus, we carry our analysis out under the condition of
. Thus, we carry our analysis out under the condition of  . Part (a) of Figure 6 shows the relationships between the real position of mobile node
. Part (a) of Figure 6 shows the relationships between the real position of mobile node  and the error of the algorithm, and part (b) of Figure 6 shows accumulated probability distribution of localization error of weighted centroid algorithm and RSSI-verifying algorithm.
and the error of the algorithm, and part (b) of Figure 6 shows accumulated probability distribution of localization error of weighted centroid algorithm and RSSI-verifying algorithm.
 .
.6.2. Evaluation2: Stability of Results
6.2.1. Simulation
The hardware platform of the simulation is MicaZ and its RF energy level is set to  . The software is developed based on TinyOS 1.1.10 and NesC. Six MicaZ nodes are used in the Simulation. Four of them are deployed at the four corners of a 5 m
. The software is developed based on TinyOS 1.1.10 and NesC. Six MicaZ nodes are used in the Simulation. Four of them are deployed at the four corners of a 5 m  5 m square in the underground mine in XinAn Coal Mine. Their coordinates are
5 m square in the underground mine in XinAn Coal Mine. Their coordinates are  , and
, and  . Suppose that node
. Suppose that node  is the base and be connected with computer and node
is the base and be connected with computer and node  is mobile node. Then, we divide the 5 m
is mobile node. Then, we divide the 5 m  5 m square into twenty-five 1 m
5 m square into twenty-five 1 m  1 m squares and select randomly ten of them as the location of the mobile node
1 m squares and select randomly ten of them as the location of the mobile node  . We let
. We let  and calculate position. The simulation is composed of two phases: RSSI collection phase which includes 50 cycles and each cycle is 2 s. We record the RSSI values received by mobile node from every fixed node on file and calculate the average value from each fixed node. The second phase is to calculate position of mobile node by different algorithms.
and calculate position. The simulation is composed of two phases: RSSI collection phase which includes 50 cycles and each cycle is 2 s. We record the RSSI values received by mobile node from every fixed node on file and calculate the average value from each fixed node. The second phase is to calculate position of mobile node by different algorithms.
6.2.2. Evaluation
We compare this mechanism with centroid algorithm, and weighted centroid algorithm, and give some tables and figures to show the effects, merits, and characteristics of this mechanism. These figures and tables are based on some typical demonstrations using this mechanism, and all technical schemes using this mechanism by equally substitutions or equivalent transformations must have the same effects.
According to the shadowing radio propagation model, the evaluation are carried out in indoor visible conditions, so the  value of radio propagation model should be in the range of 1.6
value of radio propagation model should be in the range of 1.6 1.8. We change
1.8. We change  in the range with the step of 0.05 and the result of changing
in the range with the step of 0.05 and the result of changing  is shown in Table 2. Form this table, we can learn that the steady rate of weighted centroid algorithm is increasing with the growth of
is shown in Table 2. Form this table, we can learn that the steady rate of weighted centroid algorithm is increasing with the growth of  , so we compare these three algorithms under the condition of
, so we compare these three algorithms under the condition of  . The distribution of ten sampling localization stability is shown in part (a) of Figure 7. Part (b) of Figure 7 shows us the distribution of three algorithms' localization error accumulative probability.
. The distribution of ten sampling localization stability is shown in part (a) of Figure 7. Part (b) of Figure 7 shows us the distribution of three algorithms' localization error accumulative probability.
 .
.We can see that the steady mechanism is more accurate and steady than the weighted centroid algorithm. It has material technical characteristics and marked technical progresses, and its application future will be very bright.
6.3. Evaluation 3: Mobile Network in Underground Tunnel
6.3.1. Simulation
We compare some similar work in the simulation. They are a basic localization algorithm based on MCL in paper [23] and CDL in paper [24]. We denote the algorithms in [23] and [24] as T-MCL and CDL, respectively. The algorithm in this section is denoted as A-MCL. The simulation are still carried out in the underground mine in XinAn Coal Mine. The tunnel is 3 m wide and 300 m long with no corner. Several people were deployed in the area, moving independently with max speed  and min speed
and min speed  . There are definitions of some correspond parameters of the simulation as follows
. There are definitions of some correspond parameters of the simulation as follows
-
(i)
Density of anchor node (AD): average number of anchor node in one hop transmitting radius.
-
(ii)
Time interval (
 ): localization cycle of algorithms.
): localization cycle of algorithms. -
(iii)
Node density (Nd): average number of all node in one hop transmitting radius.
-
(iv)
Accuracy evaluation parameter: the ratio of the distance between real position and result of algorithm and communication radius
 .
.
We define some other parameters in simulation in Table 3.
6.3.2. Evaluation
Figure 8 shows the evaluation of accurate localization algorithm based on MCL. Part (a) of Figure 8 shows the relationships between algorithm accuracy and running time of the three algorithms under the condition of  and
and  . Part (b) of Figure 8 shows the relationships between algorithm accuracy and density of anchor node of the three algorithms under the condition of
. Part (b) of Figure 8 shows the relationships between algorithm accuracy and density of anchor node of the three algorithms under the condition of  and
and  . Part (c) of Figure 8 shows the relationships between algorithm accuracy and node density of the three algorithms under the condition of
. Part (c) of Figure 8 shows the relationships between algorithm accuracy and node density of the three algorithms under the condition of  and
and  .
.
7. Conclusions and Future Work
In this paper, we have proposed a prototype system for real-time coal miner localization and tracking based on self-organized sensor networks. The system is composed of two parts: hardware and software platform. We have developed a set of localization hardware devices with the Safety Certificate of Approval for Mining Products include miner node, wired fixed access stations and base with optical port. On the software side, we have developed a layered software architecture of node application, server management, and information dissemination and broadcasting. In order to improve environmental adaptability, robustness, and suitability for mobile networks of self-organized sensor networks localization algorithms, we have developed three key localization technologies: an underground localization algorithm using received signal strength indication (RSSI-) verification to reduce the influence of severe environment in coal mine; a robust fault-tolerant localization mechanism to improve the inherent defect of instability of RSSI localization; an accurate localization algorithm based on Monte Carlo localization (MCL) to adapt to the underground tunnel structure. A comprehensive simulation has been designed to show the effectiveness and efficiency of the proposed system. The results from simulation and prototype show that our system is indeed more accurate and more adaptive generally in coal mine application than other traditional localization algorithms.
Considering the coal mine application of WSN is an interesting application with great promise, we plan to extend our first try in following three directions: firstly, try to deploy the system to all mines and solve the problems that we meet in large scale system; secondly, keep researching the node devices and try to enhance its robustness and reliability; finally, try to update the new system functions of equipments and material monitoring.
References
Wang H-Y, Hua G, Tian J: Research on detection device for broken wires of coal mine-hoist cable. Journal of China University of Mining and Technology 2007, 17(3):376-381. 10.1016/S1006-1266(07)60109-6
Chol L: Trunked Radio System, European Patent no. 1996-09-12, Publication number: KR960012082(B1), Application number: KR19930026622 19931206, Priority number(s): KR19930026622 19931206.
Bacheldor BAustralian Coal Mine to Enhance Safety Using RFID, RFID Journal, http://www.rfidjournal.com/
Kappler C, Mendes P, Prehofer C, Poyhonen P, Zhou D: A framework for self-organized sensor networks composition. In Autonomic Communication. Volume 3457. Springer, Berlin, Germany; 2005:139-151. 10.1007/11520184_11
Akyildiz IF, Su W, Sankarasubramaniam Y, Cayirci E: A survey on sensor networks. IEEE Communications Magazine 2002, 40(8):102-105. 10.1109/MCOM.2002.1024422
Estrin D, Culler D, Pister K, Sukhatme G: Connecting the physical world with pervasive networks. IEEE Pervasive Computing 2002, 1(1):59-69. 10.1109/MPRV.2002.993145
Estrin D, et al.: Next century challenges: scalable coordination in sensor networks. Proceedings of the 5th Annual ACM/IEEE International Conference on Mobile Computing and Networking (MOBICOM '99), 1999, Seattle, Wash, USA
Pottie G, Kaiser W: Wireless integrated network sensors. Communications of the ACM 2000, 43(5):51-58. 10.1145/332833.332838
Sengupta M: Environmental Impacts of Mining: Monitoring, Restoration, and Control. Lewis Publishers, Boca Raton, Fla, USA; 1993.
Li M, Liu Y: Underground coal mine monitoring with wireless sensor networks. ACM Transactions on Sensor Networks 2009., 5(2, article no. 10):
Rathore CS, Wright R: Monitoring the environmental impacts of surface coal mining. International Journal of Remote Sensing 1993, 14(6):1021-1042. 10.1080/01431169308904394
Li M, Liu Y: Underground structure monitoring with wireless sensor networks. Proceedings of the 6th International Symposium on Information Processing in Sensor Networks (IPSN '07), 2007, Cambridge, Mass, USA 69-78.
Bulusu N, Heidemann J, Estrin D: GPS-less low-cost outdoor localization for very small devices. IEEE Personal Communications 2000, 7(5):28-34. 10.1109/98.878533
Shen X, Wang Z, Jiang P, Lin R, Sun Y: Connectivity and RSSI based localization scheme for wireless sensor networks. Proceedings of the International Conference on Intelligent Computing (ICIC '05), August 2005, Lecture Notes in Computer Science 578-587.
Dellaert F, Fox D, Burgard W, Thrun S: Monte Carlo localization for mobile robots. Proceedings of the 1999 IEEE International Conference on Robotics and Automation (ICRA '99), May 1999 1322-1328.
Thrun S, Fox D, Burgard W, Dellaert F: Robust Monte Carlo localization for mobile robots. Artificial Intelligence 2001, 128(1-2):99-141. 10.1016/S0004-3702(01)00069-8
Hu L, Evans D: Localization for mobile sensor networks. Proceedings of the 10th Annual International Conference on Mobile Computing and Networking (MobiCom '04), 2004, Philadelphia, Pa, USA
Shee SH, Wang KC: Color theory based dynamic localization in mobile wireless sensor networks. Proceedings of the Workshop on Wireless, Ad Hoc, Sensor Networks, August 2005
Acknowledgments
The authors gratefully acknowledge Professor Yi Shang from University of Missouri-Columbia and Dr. An Liu from USTC for valuable comments and suggestions on draft versions of this paper. And also thank anonymous reviewers for reading this paper and giving valuable comments. This paper is supported by the National Grand Fundamental Research 973 Program of China under Grant no. 2006CB303006, the National Natural Science Foundation no. 60903055 and the China Postdoctoral Science Foundation funded project under Grant no. 20080430776.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License (https://creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Wang, Y., Huang, L. & Yang, W. A Novel Real-Time Coal Miner Localization and Tracking System Based on Self-Organized Sensor Networks. J Wireless Com Network 2010, 142092 (2010). https://doi.org/10.1155/2010/142092
Received:
Accepted:
Published:
DOI: https://doi.org/10.1155/2010/142092


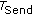 cycle, and all mobile nodes receive localization detection packets in
cycle, and all mobile nodes receive localization detection packets in 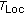 cycle
cycle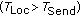 . In one
. In one  cycle, mobile nodes collect and buffer all localization detection packets they received. At the end of this cycle, they pack and send these packets. On the other hand, mobile nodes can receive management and query instructions and send response results.
cycle, mobile nodes collect and buffer all localization detection packets they received. At the end of this cycle, they pack and send these packets. On the other hand, mobile nodes can receive management and query instructions and send response results. . Then, we assume the original position in time
. Then, we assume the original position in time 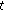 of unknown node is
of unknown node is 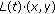 and its position after discretization in time
and its position after discretization in time 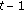 is
is  . Next, we can have the position after discretization in time
. Next, we can have the position after discretization in time 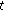 : if the distance between
: if the distance between 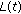 and
and 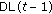 is less than
is less than 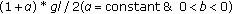 , then
, then 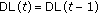 ; otherwise,
; otherwise, 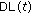 equals to the center of the square where
equals to the center of the square where 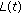 locates.
locates.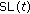 is the shown position of unknown node in time
is the shown position of unknown node in time 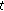 and use function
and use function 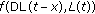 (
(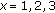 ) to compute the position after discretization of unknown node in time
) to compute the position after discretization of unknown node in time 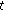 by its original position
by its original position 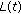 in time
in time 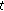 and positions after discretization in time
and positions after discretization in time 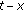 , and the initial state of the function is 0. Here, we have the steady localization mechanism based on automatic state machine which is shown in Figure
, and the initial state of the function is 0. Here, we have the steady localization mechanism based on automatic state machine which is shown in Figure 
 means the average value of RSSI values in time
means the average value of RSSI values in time 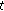 ,
, 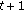 and
and 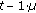 is a given threshold. Then, we will give a modification of intermittent interference avoiding by the way of filtering abnormal data packets.
is a given threshold. Then, we will give a modification of intermittent interference avoiding by the way of filtering abnormal data packets.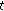 is less than
is less than 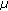 , then update
, then update 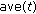 ; otherwise,
; otherwise, 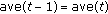 and go to state 1.
and go to state 1.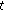 is less than
is less than 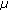 , then update ave(
, then update ave(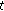 ) and go to state 0; otherwise,
) and go to state 0; otherwise, 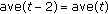 and go to state 2.
and go to state 2. is less than
is less than  , then update
, then update  ; otherwise,
; otherwise, 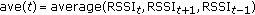 .
. sample points, so as to interpolate the track of mobile node.
sample points, so as to interpolate the track of mobile node.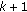 sampling points can be modified values of predicated positions in former
sampling points can be modified values of predicated positions in former 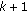 time points. The time interval can be random, but it would be better if it is more intensive and closer to current time.
time points. The time interval can be random, but it would be better if it is more intensive and closer to current time.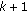 sample points, add the modified value into sample window, select those sample points in the window which has the minimum difference to the modified value, and start a new round interpolation from now on.
sample points, add the modified value into sample window, select those sample points in the window which has the minimum difference to the modified value, and start a new round interpolation from now on.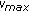 which branches at
which branches at 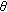 (
(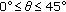 ) angle clockwise and counter-clockwise to the moving direction of mobile node
) angle clockwise and counter-clockwise to the moving direction of mobile node 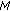 .
.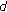 as second order curves which are tangent to the moving direction of mobile node
as second order curves which are tangent to the moving direction of mobile node 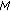 .
. points as the predication positions from these
points as the predication positions from these 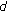 curves and these
curves and these  points must be in the sector.
points must be in the sector. after filtering, we can double the angle
after filtering, we can double the angle  and use the same way to complement the absent part. This part will repeat until we have
and use the same way to complement the absent part. This part will repeat until we have  points which can satisfy our requirements.
points which can satisfy our requirements.



 ): localization cycle of algorithms.
): localization cycle of algorithms. .
.